Remediate your open incidents
Please note that the IaC remediation features are currently in private beta. To activate them, please join the waitlist directly from your GitGuardian dashboard!
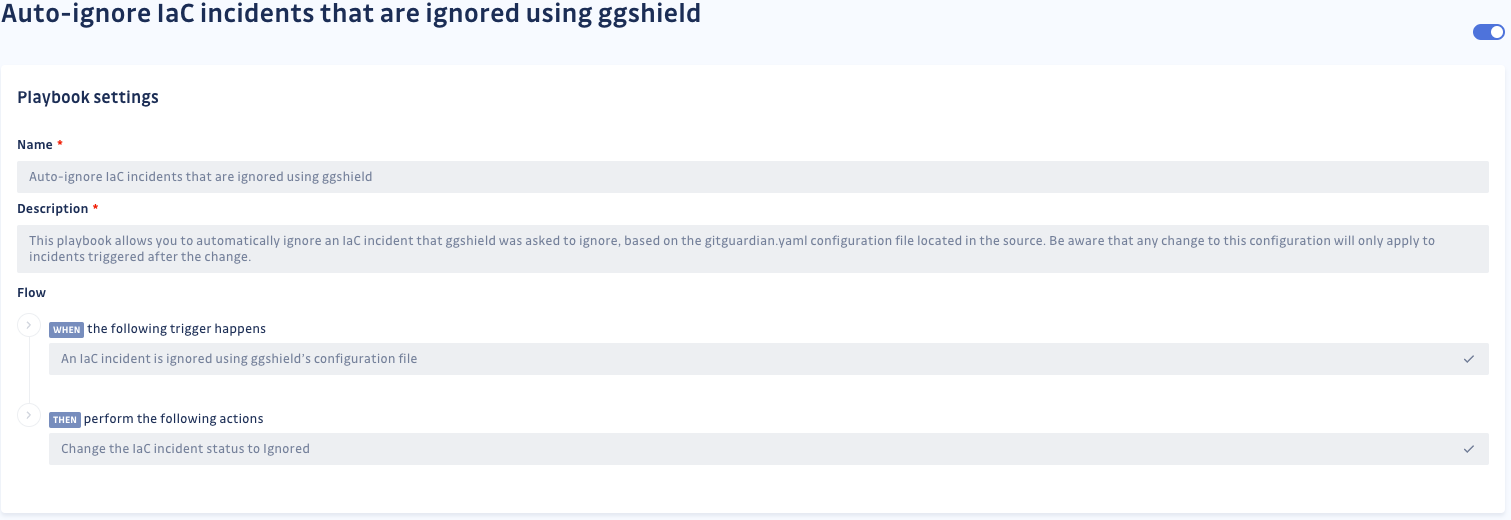
Prioritize your remediation
As you face multiple IaC incidents, prioritization is key for a successful and efficient remediation. Each IaC incident is enriched with the following context:
- A description of the underlying vulnerability.
- A list of its potential technical impacts.
- The level of exploitability indicates the ease with which malicious actors can exploit the vulnerability.
- The category of the provider's service it is affecting.
- The potential data exposure indicates the possibility of a data leak.
- Whether its exploitation is visible in the logs.
- Whether a legitimate user interaction is required to exploit the vulnerability further.
- Whether additional privileges are required to exploit the vulnerability further.
- Remediation guidelines outlining the steps to resolve the vulnerability.
- A potential external documentation listing additional resources.
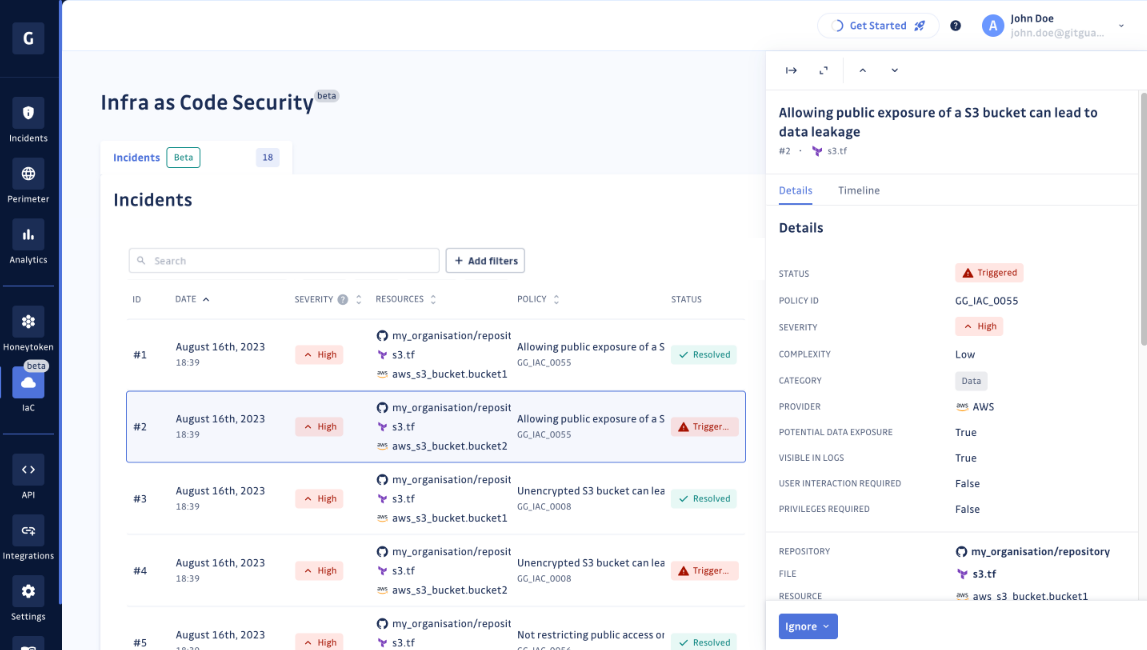
This context will help you fully grasp the impact of the IaC incident and guide you toward its remediation. You can access this information:
- Either through the sidebar displayed when clicking on a specific IaC incident, as shown above.
- Or by expanding the sidebar when focusing on a specific incident, as shown below.
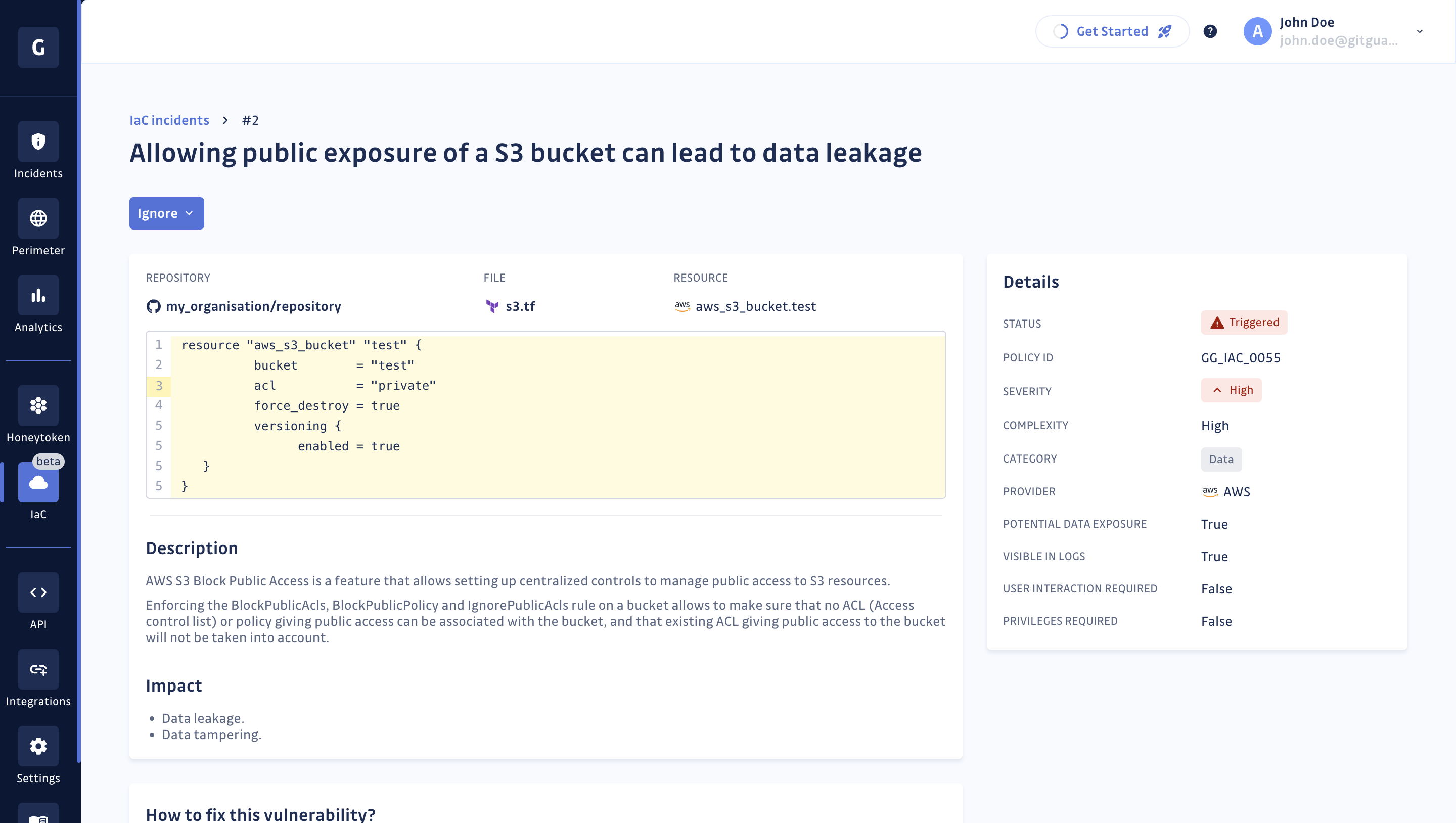
Share an IaC incident
By default, IaC incidents are only accessible to workspace Managers and Owners. Nevertheless, authorized users can share access to an incident with one or several Member(s) or Restricted user(s) by using the "Share" button located at the bottom right corner.
From there, you will be invited to enter the name(s) of the Member(s) and/or Restricted user(s) you want to have access to the incident. Then, click on "Grant access" to validate.
You will also be able to view Member(s) and/or Restricted user(s) that already have access to the incident. Lastly, you can revoke access for a Member or a Restricted user if you no longer wish them to have access to the incident.
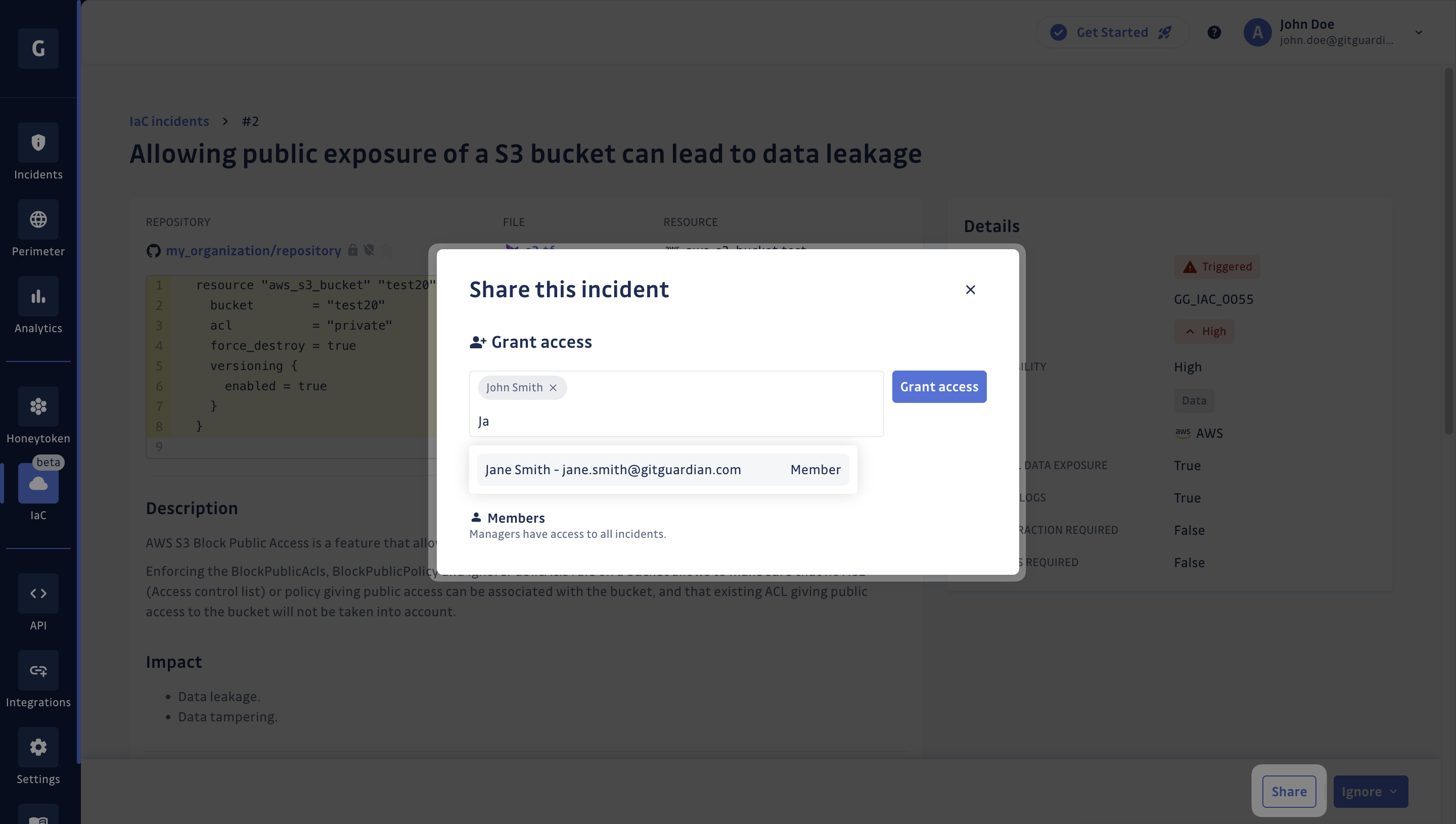
Once granted access to an incident, a Member or a Restricted user has the same permissions as a Manager or Owner on that incident, including the right to ignore it or share it with one or more other user(s).
Resolve an IaC incident
Resolving an IaC incident will require its underlying vulnerability to be fixed from the source, meaning directly within the IaC file.
To do so, please contact the team in charge of writing IaC files and let them know about this IaC incident. To ease the process, share them any of the information provided in the incident, especially:
- Its location, including the repository name, the filename and the resource name.
- The link to its corresponding rule using the policy ID.
Once the underlying vulnerability is fixed, its corresponding incident status will automatically change to resolved on the platform.
Feel free to also add any notes that may be useful to link to the incident. That way, one will be able to check them using the incident's timeline, alongside any activity that may have happened, including its detection and remediation.
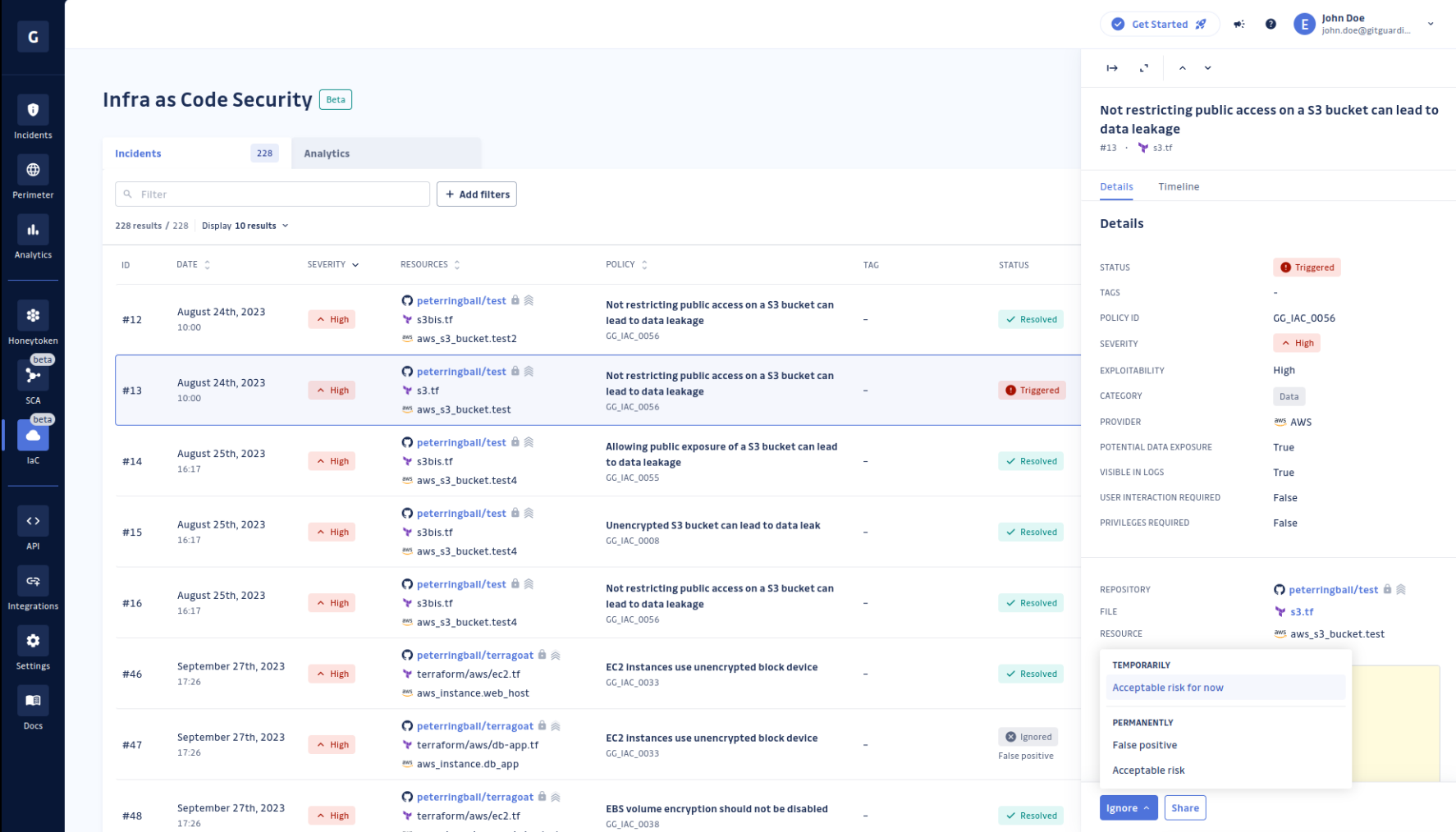
Ignore an IaC incident
There are instances when IaC incidents may not require a resolution, either because you consider their risk acceptable or due to other reasons. In such cases, you can:
- Ignore the incident permanently if you wish to disregard it in the future.
- Ignore the incident temporarily if you don't want to deal with this IaC incident right now.
Please note that any ignored incident can be reopened at any time through the platform, causing its status to revert to triggered.
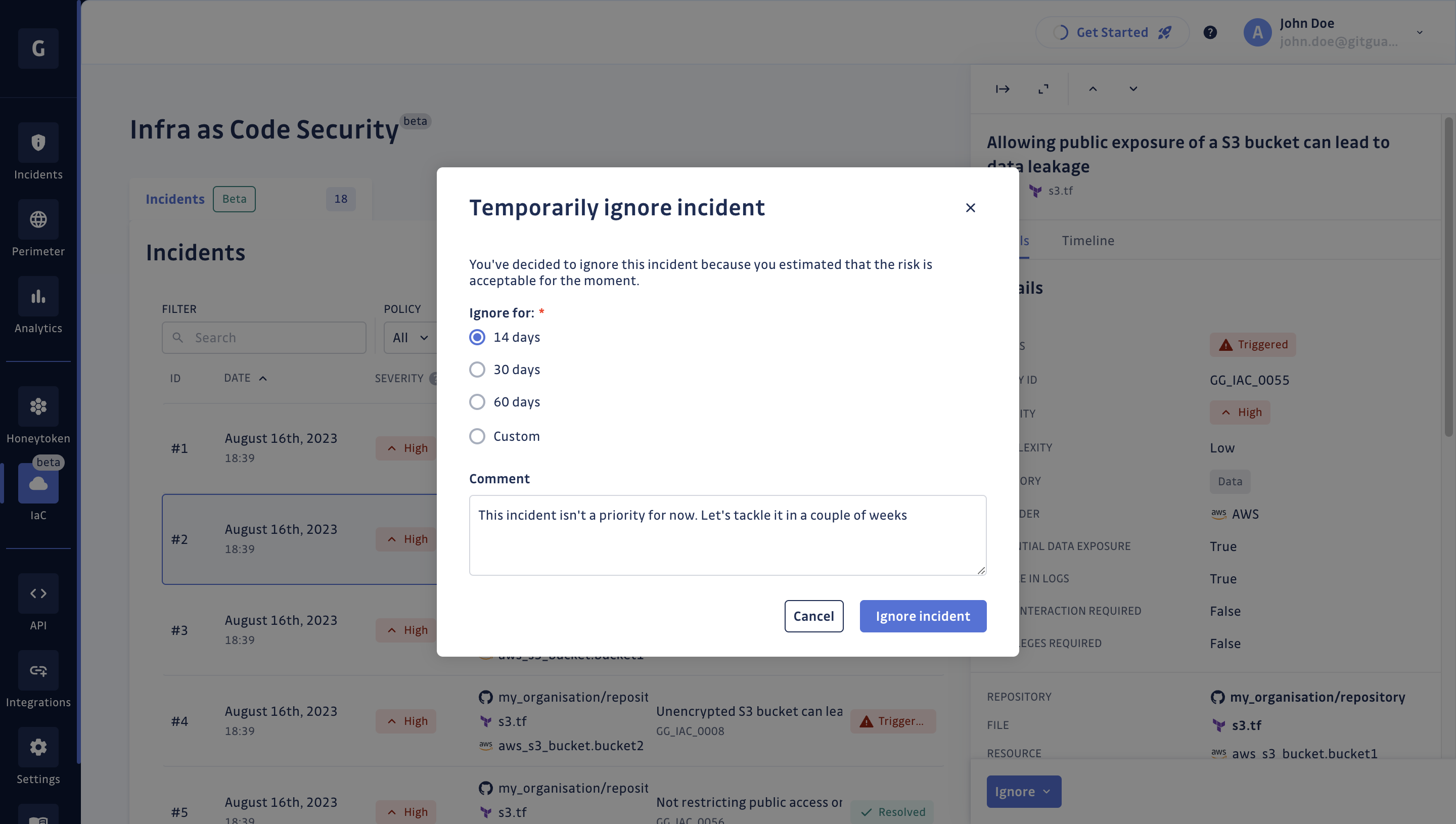
In case you decide to ignore it temporarily, you will be able to specify a grace period during which you want to ignore this incident, as you can see below.
If, by any chance, you consider an IaC incident a false positive–because it doesn't pertain to a valid IaC vulnerability–we kindly request that you select False positive when ignoring it. This action will prevent future notifications for this incident while assisting us in continually enhancing our detection capabilities.
Automate with playbooks
The playbooks enable you to customize and automate GitGuardian's functionalities and are accessible within your workspace settings only for business and business trial plans.
If you need other playbooks, do not hesitate to submit your request here. Also, please refer to this page for more details about other available Secret playbooks.
Auto-ignore playbook
The IaC auto-ignore playbook automatically ignores incidents on the platform that ggshield has been asked to ignore by one of your developers. This is based on the presence of the ignored using ggshield tag.
Note that the activation or deactivation of this playbook will only impact the incidents triggered subsequently.