Dependency Confusion Vulnerability Exposure
What is Dependency Confusion?
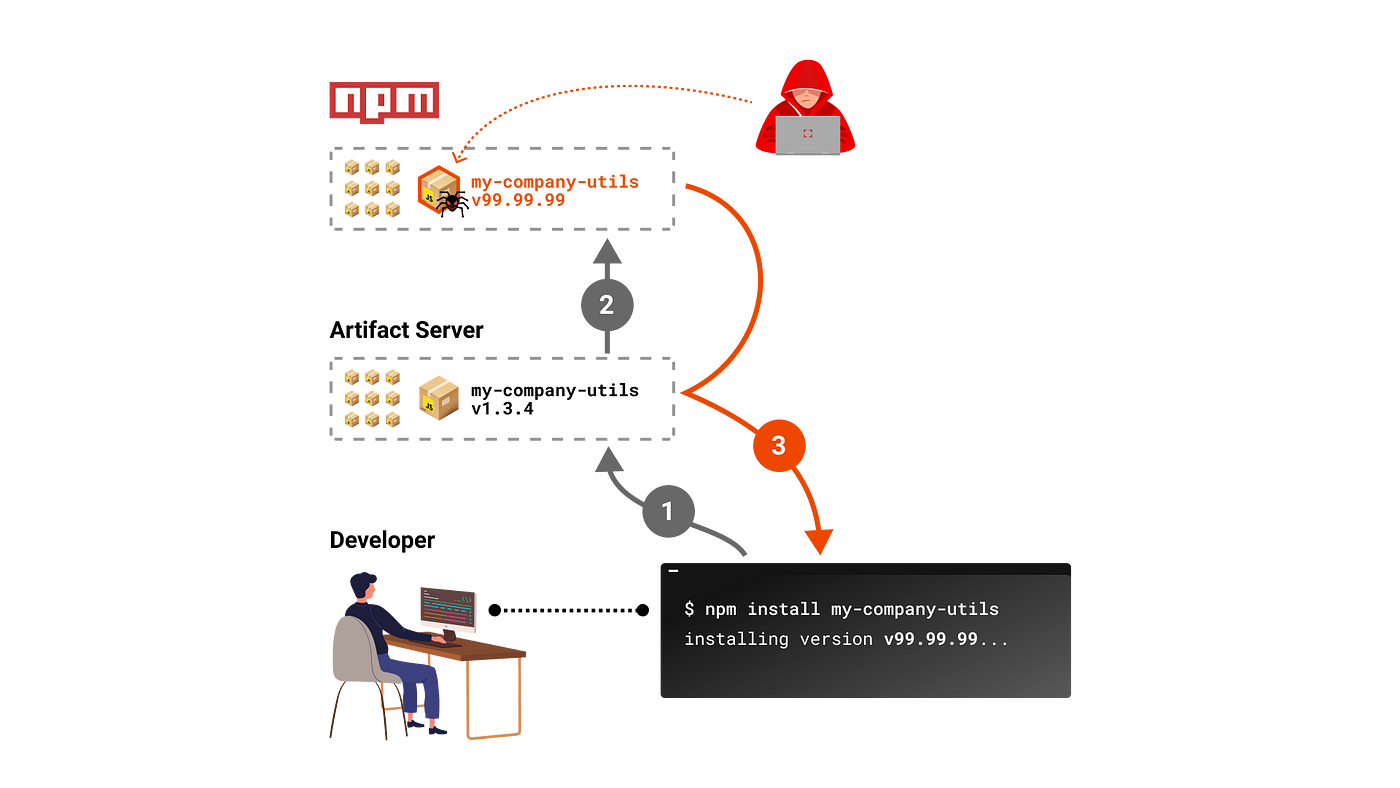
Dependency confusion occurs when a software project relies on both private and public package repositories. Attackers may register public packages with names identical to those of privately owned software dependencies. By leveraging the behavior of the package managers’ resolution algorithm, they aim to trick systems into mistakenly downloading the malicious public package instead of the safe, privately owned one. GitGuardian SCA identifies vulnerable packages that are prone to dependency confusion attacks.
Mitigation Strategies
There is no silver bullet, but GitGuardian recommends the following strategies to help you address dependency confusion risks:
- Namespace Reservation: Reserve a unique namespace for your internal packages to prevent naming collisions with public packages.
- Dependency Locking: Lock your dependencies to specific versions, ensuring that your build system always uses the intended packages.
- Repository Configuration: Configure your build system to prioritize internal repositories over public ones, reducing the likelihood of dependency confusion.
Dependency Confusion detection
GitGuardian SCA module scans your project's dependencies, comparing them against popular public repositories. If it finds any matches between your internal packages and public ones, it flags them as potential dependency confusion risks.
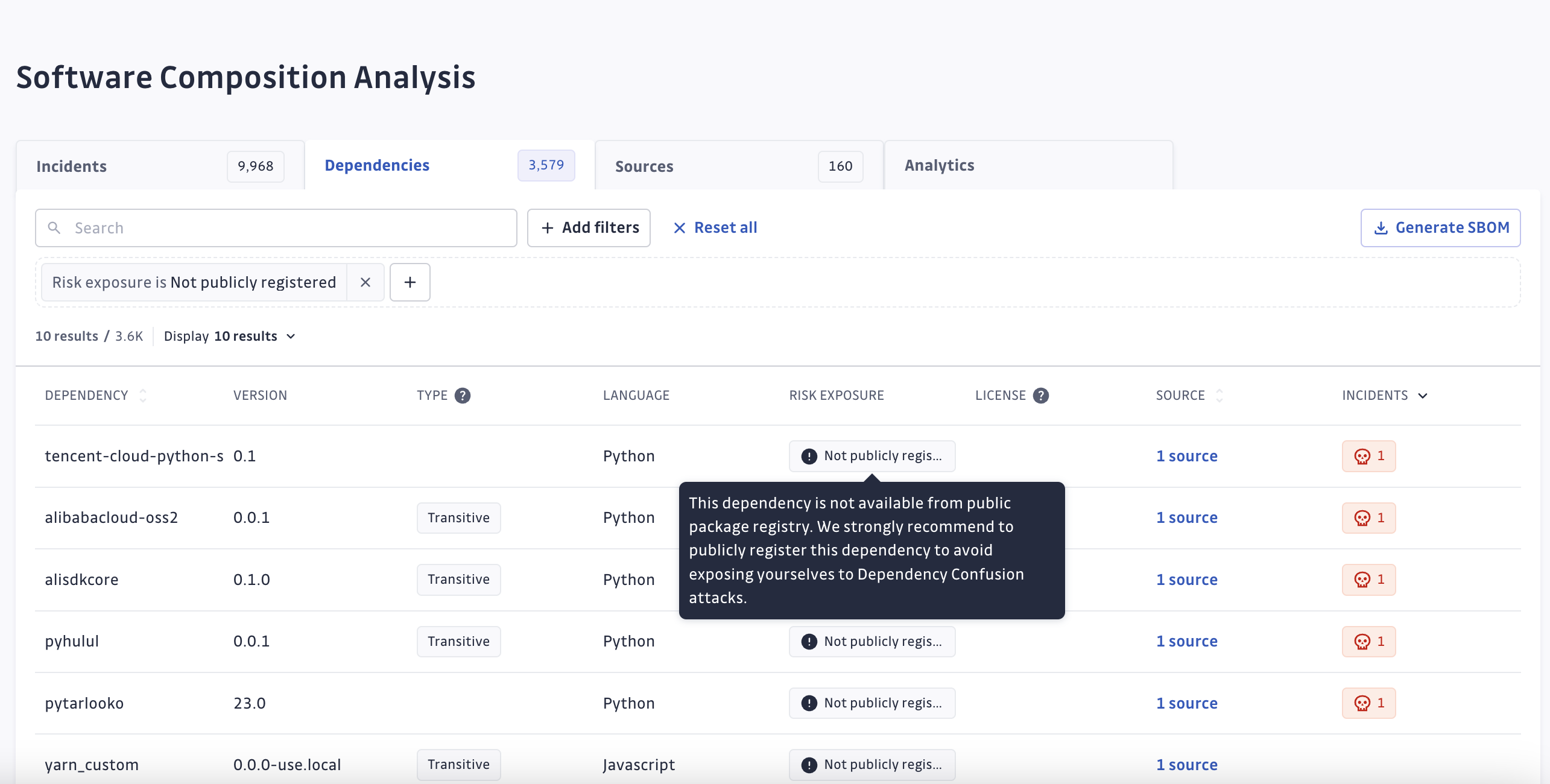
Two tags highlight the underlying Risk
- Not publicly registered, meaning that the namespace has not been publicly registered by your organization. By doing so, attackers may reserve the namespace and publish a malicious package that may affect your systems down the line.
- Unregistered organization, meaning that the package was registered but your organization, scope or domain was not. Attackers may still be in a position to register your organization's name and publish a malicious package with the same name to trick your organization's dependency managers into mistakenly downloading the malicious public package.
In both cases, GitGuardian strongly recommends you register your own organization, scope or domain and publicly register your packages namespace to make sure you are not vulnerable to Dependency Confusion.