SCA for self-hosted installations
Enabling SCA on self-hosted environments
To enable SCA in your self-hosted GitGuardian instance, please reach out to support@gitguardian.com. Exclusive to the new architecture.
After receiving your request, GitGuardian will enable the module and reach out to finalize the setup.
Please note that this feature is incompatible with air-gapped configuration as it requires access to public package managers (e.g. npm, PyPI, etc...) and vulnerability databases.
Synchronize your license
After receiving confirmation from your GitGuardian contact that the SCA module is enabled for your instance(s), it is crucial to synchronize your GitGuardian application's license accordingly.
Once done, the SCA module will appear on your GitGuardian dashboard within a few minutes.
Assuming your repositories are already integrated, the scan for dependency vulnerabilities of your repositories will be automatically launched upon the license synchronization. The scan duration depends on the size of your perimeter but can sometimes last a few minutes before it is completed.
Configure scaling settings
We recommend using dedicated workers for SCA. For more detailed information on scaling and configuration, please visit our scaling page.
Setup your GitHub Token
If your organization uses PHP and needs to enable the SCA scans on this specific ecosystem, a GitHub token with repo scope is required to fetch the dependencies from Packagist.
To configure your GitHub Token, you will need to:
- Access the Admin area of your GitGuardian dashboard (administrative rights are necessary).
- Navigate to Settings > SCA and fill in your GitHub Token.
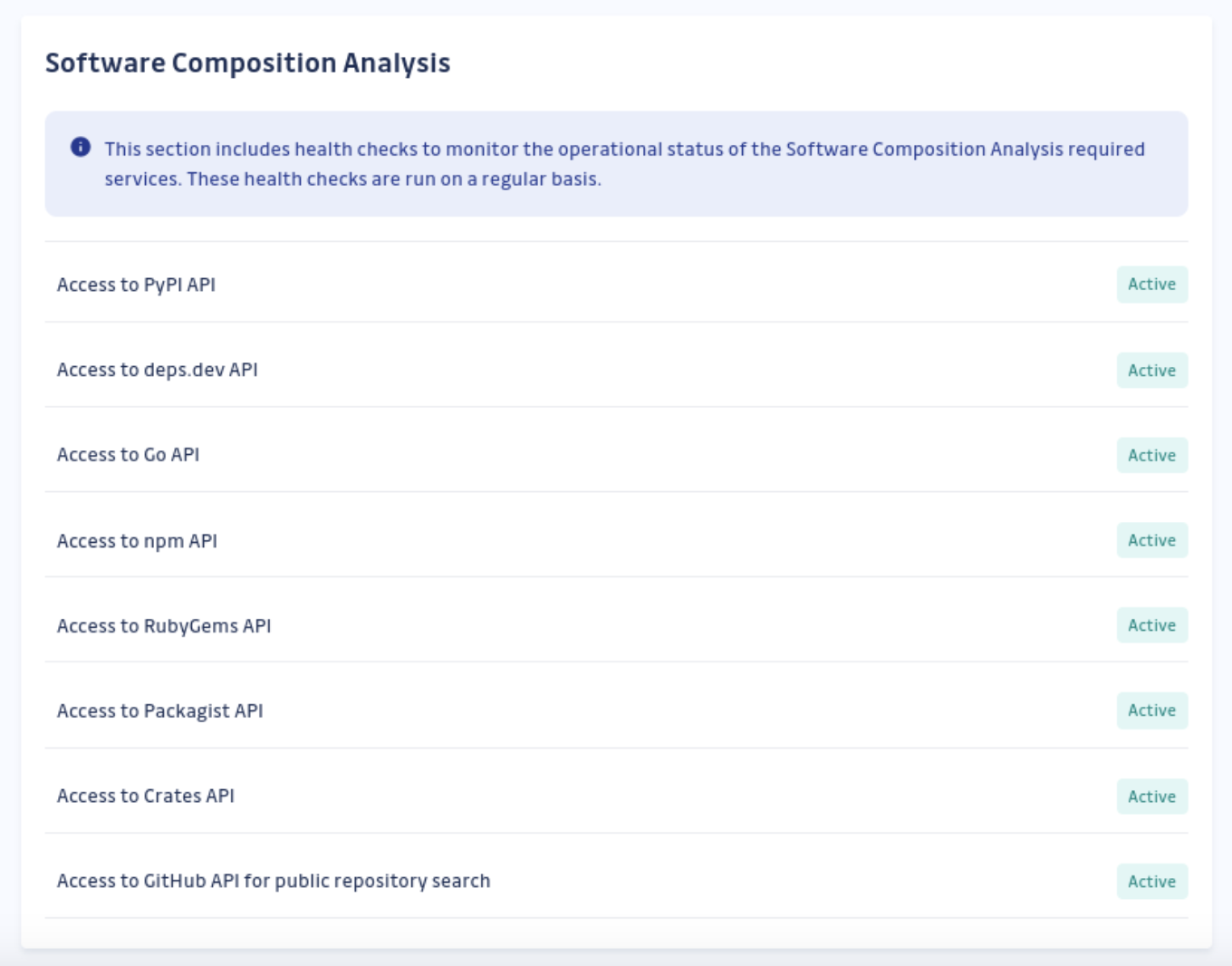
Health checks
The Health Checks page in the Admin area contains an SCA section, showing the different public package registries and vulnerability databases the solution needs to access. This helps quickly identify the status of the services required for SCA to run normally.
Network requirements
Outbound rules
To be able to gather and correlate dependencies from your sources and existing vulnerabilities, GitGuardian SCA module needs to access:
- the public package registries for each ecosystem scanned,
- as well as the Open Source Vulnerability (OSV) databases. Every outbound communication between your GitGuardian instance and these services is performed on port 443 over HTTPS.
| Port | Source | Destination | Description |
|---|---|---|---|
| 443 | All K8S nodes | registry.npmjs.org | npm JavaScript package registry |
| 443 | All K8S nodes | go.dev | Go public package registry |
| 443 | All K8S nodes | pypi.org | Python package index |
| 443 | All K8S nodes | crates.io | Rust community's Crate Registry |
| 443 | All K8S nodes | repo.packagist.org | PHP Package Repository |
| 443 | All K8S nodes | rubygems.org | Ruby community's gem hosting service |
| 443 | All K8S nodes | github.com | PHP package license fetching from GitHub |
| 443 | All K8S nodes | deps.dev | Google deps.dev open source insight database |
| 443 | All K8S nodes | osv-vulnerabilities.storage.googleapis.com | Open Source Vulnerability database |
| 443 | All K8S nodes | epss.cyentia.com | EPSS score database |