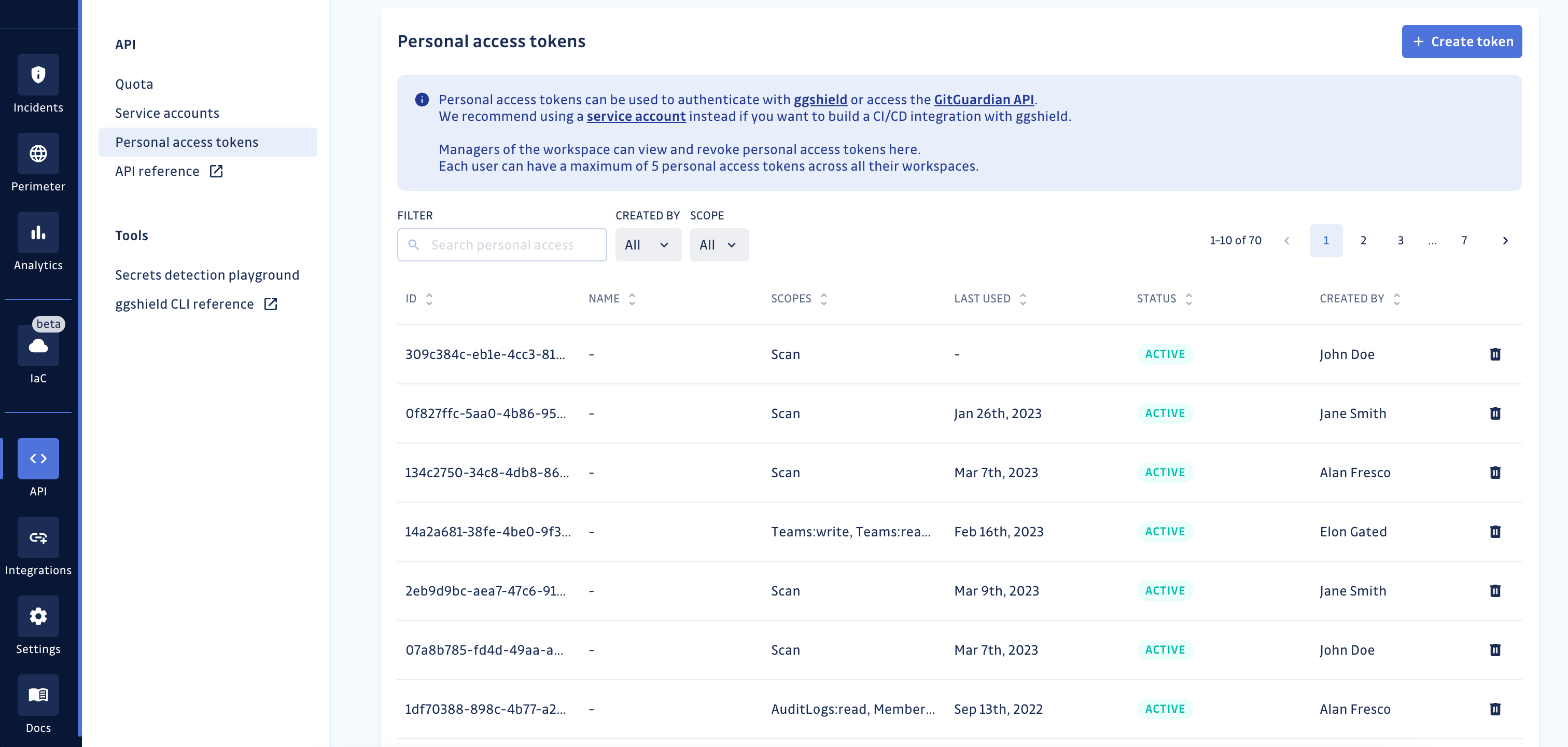
Personal access tokens
Prelude
Personal access tokens are used to authenticate calls to the GitGuardian API. They are intended to be used by developers on their local workstations to scan for secrets with the help of ggshield (in pre-commit or pre-push git hooks).
Creating a personal access token
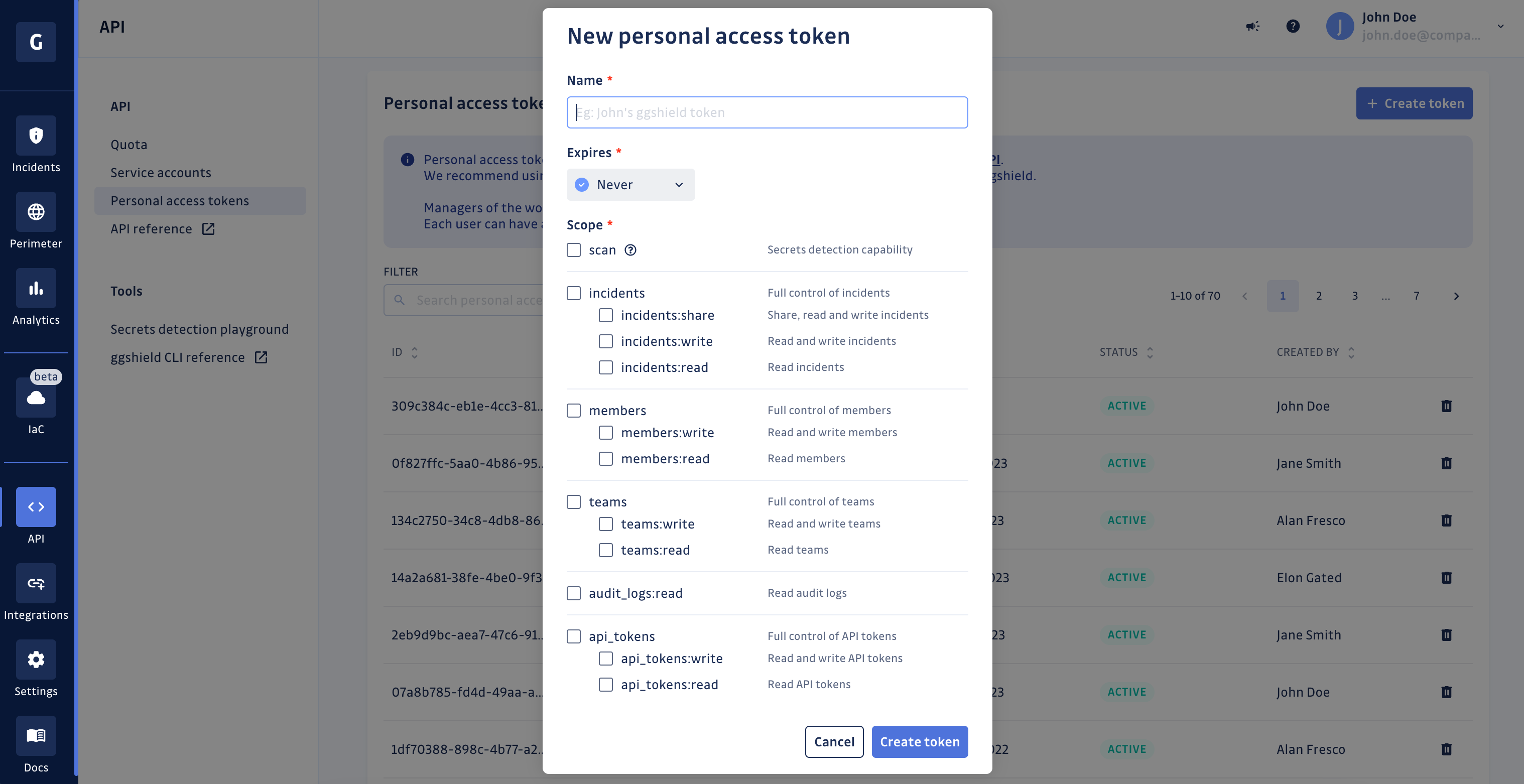
- Go to the Personal access tokens page in the API section of your workspace. Click on
Create token - Name your key according to its use-case (for example
<Git Hook Name>-<Environment or Machine>) - Set an expiry date for your token (in 1 week, 1 month, 3 months, 6 months, 1 year, or never). If you set an expiry date, you will receive an email to notify you 5 days before expiration.
- Click on
Create token
Make sure you copy the token, it will no longer be visible to you in the future.
Additional thoughts
- A user provisioning a personal access token with any data scope will allow them to only retrieve resources following what they have access to via the UI.
- Each user is allowed 5 personal access tokens in total.
- A personal access token is tied to the user who created it. If the user is deleted, their personal access tokens are also deleted. This is especially useful for deprovisioning purposes in a large organization.
- If you are a member of more than one workspace, you will need to specify which workspace your personal access token is attached to.
Managing personal access tokens
In the Business plan, workspace Managers can administrate the personal access tokens issued for their GitGuardian workspace. They can view, filter, and revoke personal access tokens of all workspace members directly from the table.