Overview
Description
The secret scan command is the entry point to secrets detection using ggshield.
ggshield secret scan [OPTIONS] <SUBCOMMAND> [ARGS]...
Options
It supports a few options that can be used to adapt the output behavior.
--json: output results in JSON [default:false]--show-secrets: show secrets in plaintext instead of hiding them.--exit-zero: always return a 0 (non-error) status code, even if incidents are found. The env varGITGUARDIAN_EXIT_ZEROcan also be used to set this option.-v,--verbose: verbose display mode.-o,--output <PATH>: route ggshield output to file.-b,--banlist-detector <TEXT>: exclude results from a detector.--exclude <PATH>: do not scan paths that match the specified glob-like patterns.--ignore-known-secrets: ignore secrets already detected in post-receive and therefore known by your GitGuardian dashboard. [default: False]
We strongly recommend that you do not use this option in CI mode (ggshield secret scan ci) as race conditions will affect detection.
ggshield global options
-h,--help: display detailed help
Subcommands
The command can be used with several subcommands depending on the data that needs to be scanned.
- ggshield secret scan archive
- ggshield secret scan ci
- ggshield secret scan commit-range
- ggshield secret scan docker
- ggshield secret scan docset
- ggshield secret scan path
- ggshield secret scan pre-commit
- ggshield secret scan pre-push
- ggshield secret scan pre-receive
- ggshield secret scan pypi
- ggshield secret scan repo
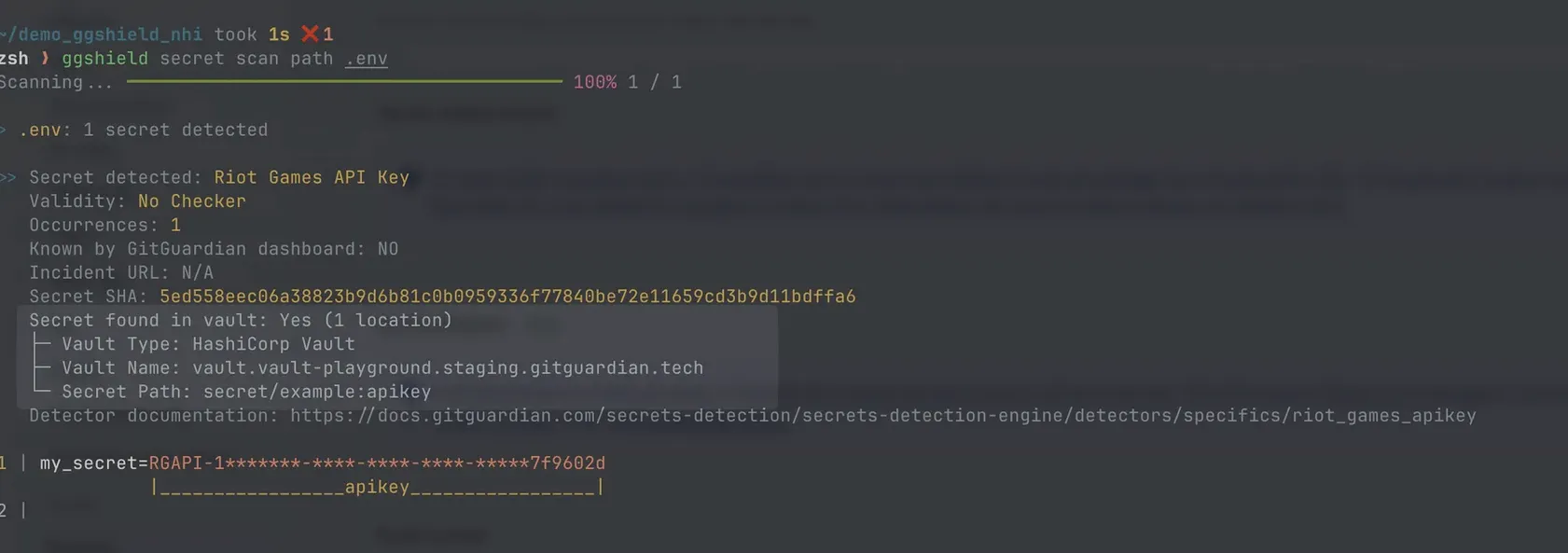
Vault Path Disclosure
When ggshield detects a secret stored in one of your integrated vaults, it can display the precise vault location to help developers remediate leaks faster. How it works: during a scan, ggshield checks your configured vaults (e.g., HashiCorp Vault, AWS Secrets Manager, Azure Key Vault) and, if a match is found, shows:
- Vault name: which secrets manager holds the secret
- Secret path: the exact vault location
- Environment type: production paths first, then staging and development
To enable it, navigate to Settings → General → Show vault path in ggshield