Explore
Explore enables you to proactively search for secrets that may have been leaked in public GitHub repositories related to your organization. By expanding your secret detection beyond your defined perimeter, Explore helps you discover exposures that traditional perimeter-based monitoring might miss.
Explore is designed to help you find secrets related to your company's infrastructure, domains, and technologies. Focus your searches on company-specific terms for the most relevant and actionable results.
How Explore works
Explore allows you to search through public GitHub commits and patches using sophisticated query capabilities, then scan the results for secrets using GitGuardian's detection engine.
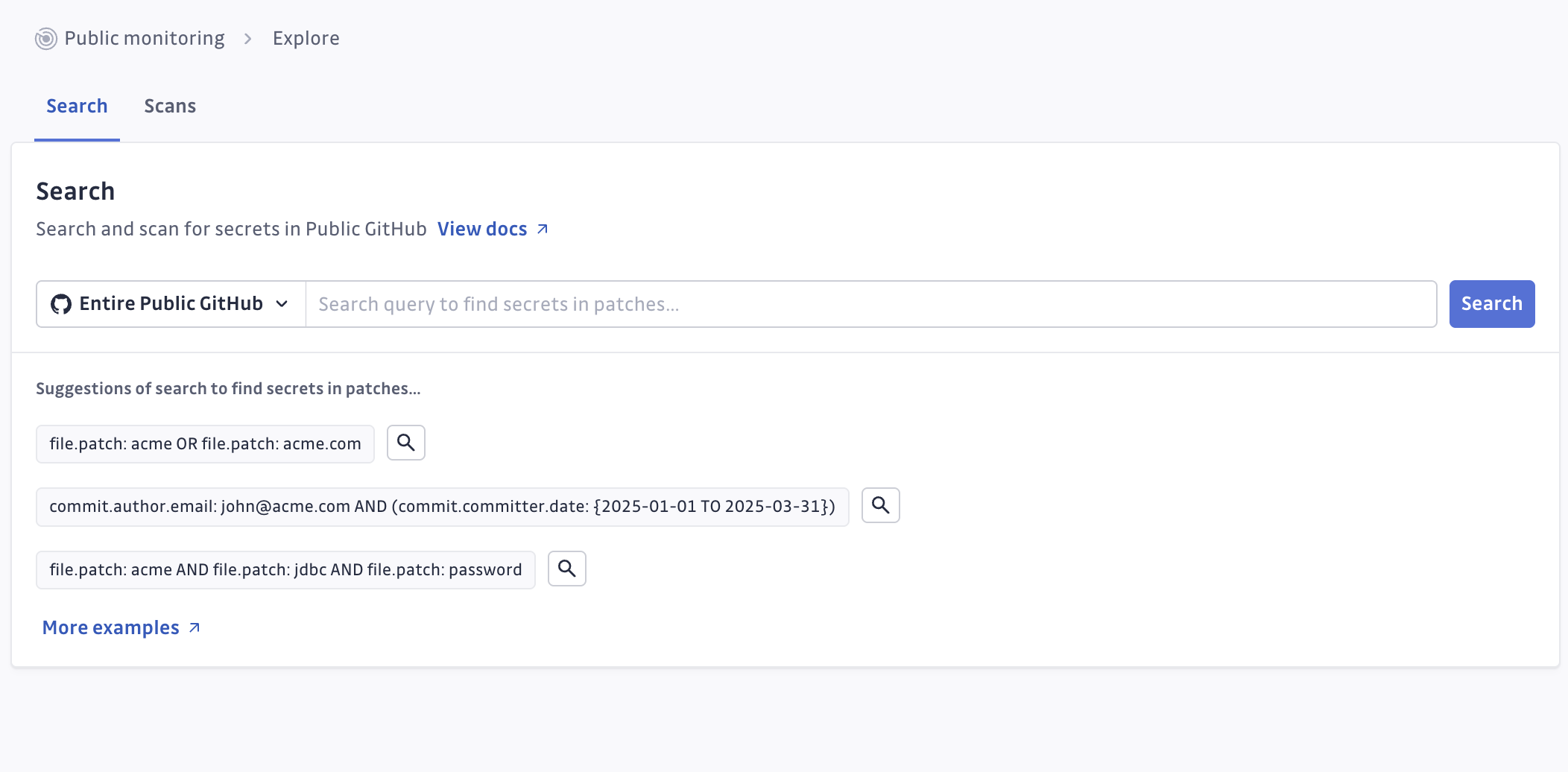
1. Search for relevant commits
Use targeted search queries to find public commits that might contain secrets related to your organization:
- Search for your company domains, API endpoints, or infrastructure
- Look for commits from current or former employees
- Find references to your internal systems or technologies
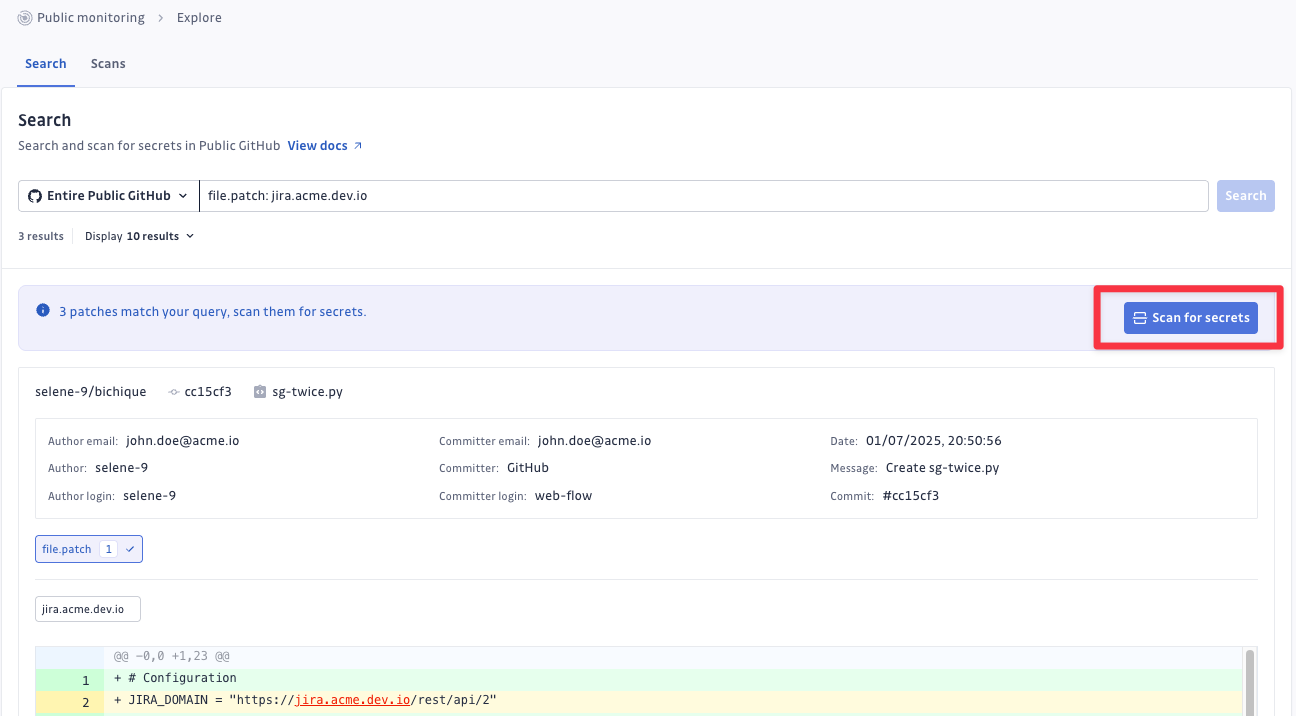
2. Scan results for secrets
Once you've identified potentially relevant commits, scan them for actual secrets, using GitGuardian's comprehensive detector library.
3. Create incidents and monitor
Transform discovered secrets into actionable security incidents:
- Create public secret incidents directly from scan results
- Set up automated incident creation with scheduled scans
- Track and remediate exposures through your standard incident workflow
Getting started and best practices
-
Use company-specific searches: Focus on terms directly related to your organization (domains, infrastructure, technologies) rather than generic keywords. This ensures relevant, actionable results and stays within the 10,000 result limit required for scanning.
-
Scan results: Use the search interface to find relevant commits, then scan the results to identify actual secret exposures
-
Create incidents: Convert findings into trackable security incidents through your standard workflow
-
Set up monitoring: Schedule regular scans for critical search queries to maintain ongoing monitoring
-
Regular review: Monitor the quality of results and refine queries to reduce false positives and improve detection effectiveness
Next steps
- Learn the search syntax for building effective queries
- Understand how to scan and monitor search results

