“Explore” and find more company-related secrets!
Release Date: September 26, 2025
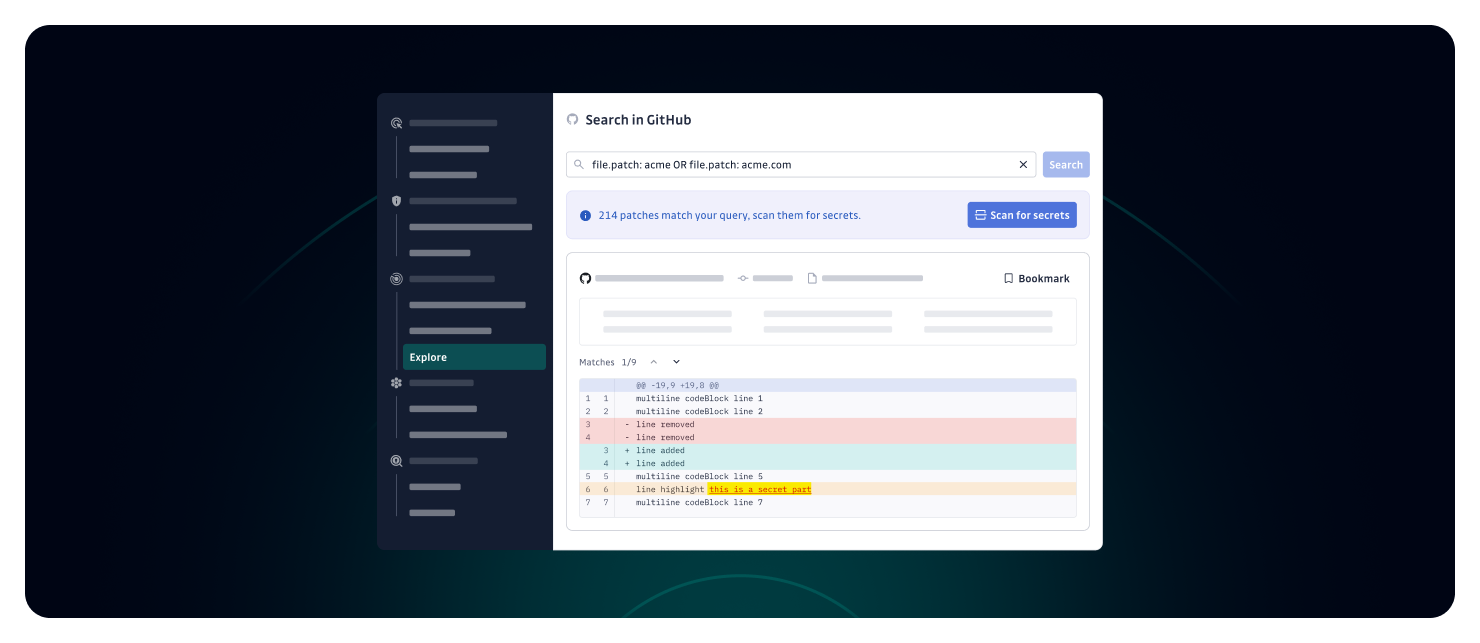
Public Monitoring's new Explore feature enables you to proactively discover secrets related to your organization that may have been leaked beyond your defined perimeter. This powerful enhancement helps you find exposures in public GitHub repositories that the perimeter-based monitoring might miss.
Explore is available exclusively for Public Monitoring customers. Contact us for availability and pricing information.
How it works:
- Company-focused search: Use targeted queries to find commits containing your domains, service names, or internal system references
- Secret detection: Scan search results using GitGuardian's detection engine
- Incident creation: Convert discovered secrets into public secret incidents
- Automated monitoring: Schedule searches for your organizational assets with automatic incident creation
Why it matters: Your secrets can leak outside your direct control - in personal repositories, contractor projects, or third-party integrations. Explore helps you discover these organizational exposures by searching for your company's specific digital footprint: domains, email patterns, service names, and infrastructure references.
Get started today: Public Monitoring customers can navigate to Public Monitoring > Explore and use the built-in search tailored for organizational security monitoring.
Learn more on Explore.
Enhancements
- Public Monitoring perimeter: Added CSV export functionality to download the list of developers.
- Secret detail: Base64 Basic Authentication token incidents now show the decoded username and password in the secret information.
- New Ignore reason: Added "Invalid Secret" as a reason when ignoring incidents where the secret was already invalid at detection time and requires no remediation.

