Integrate Slack
Monitor Slack workspaces for exposed secrets in channel messages, and team discussions.
Why Monitor Slack?
Slack serves as the central hub for team collaboration where developers frequently share code snippets, configuration examples, and troubleshooting outputs in real-time discussions. These casual conversations often contain accidentally copied API keys, database credentials, and debug information with embedded secrets, creating immediate security risks that spread across channels and persist in chat history.
Capabilities
| Feature | Support | Details |
|---|---|---|
| Historical Scanning | ✅ (Manual Trigger) | Analyze existing messages and chat history |
| Real-time Detection | ✅ (Supported) | Instant detection via Slack Events API |
| Monitored Perimeter | ✅ (Supported) | Select public channels to monitor - private channels require app invitation |
| Team Perimeter | ⏳ (Coming Soon) | Users must be in the "All-incidents" team to access incidents |
| Presence Check | ❌ (Not Supported) | All occurrences considered present |
| Direct Messages | ✅ (Upon Consent) | When explicitly authorized by user |
| File Attachments | ✅ (Beta) | File attachments dropped in channels/messages are supported |
| Interactive Message | ✅ (Beta) | Users receive threaded interactive message when a secret is surfaced |
What we scan:
- Public and private channel messages
- Direct messages (when explicitly authorized)
- Thread discussions and replies
Plan requirements: Available for GitGuardian Business and Enterprise plans. Try it for free with a 30-day trial - any detected incidents remain accessible after the trial ends.
Detector coverage: To minimize false positives, Generic High Entropy Secret and Generic Password are disabled. All other detectors are enabled.
Setup GitGuardian for Slack Integration on GitGuardian SaaS
Prerequisites:
- Owner or Manager account on your GitGuardian Dashboard
- Slack Workspace Owner permissions (if app restrictions are enabled)
GitGuardian natively integrates with Slack via the GitGuardian or GitGuardian EU application on Slack Marketplace. The GitGuardian app for Slack has read-only access to your channels.
You can refer to the Slack documentation for more information on managing apps.
You can install GitGuardian on multiple Slack workspaces to start monitoring for secret leaks.
- Make sure you're logged in to the Slack workspace you want to install
- On the GitGuardian platform, navigate to the Sources integration page
- Click Install next to Slack in the Messaging section
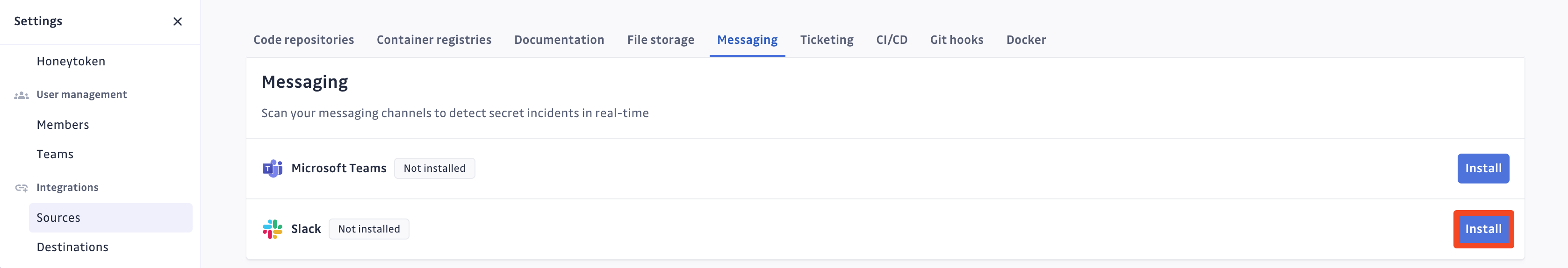
- Click Install on the Slack integration page
- Select the Slack workspace you want to add
- Click Allow to grant the permissions requested by GitGuardian
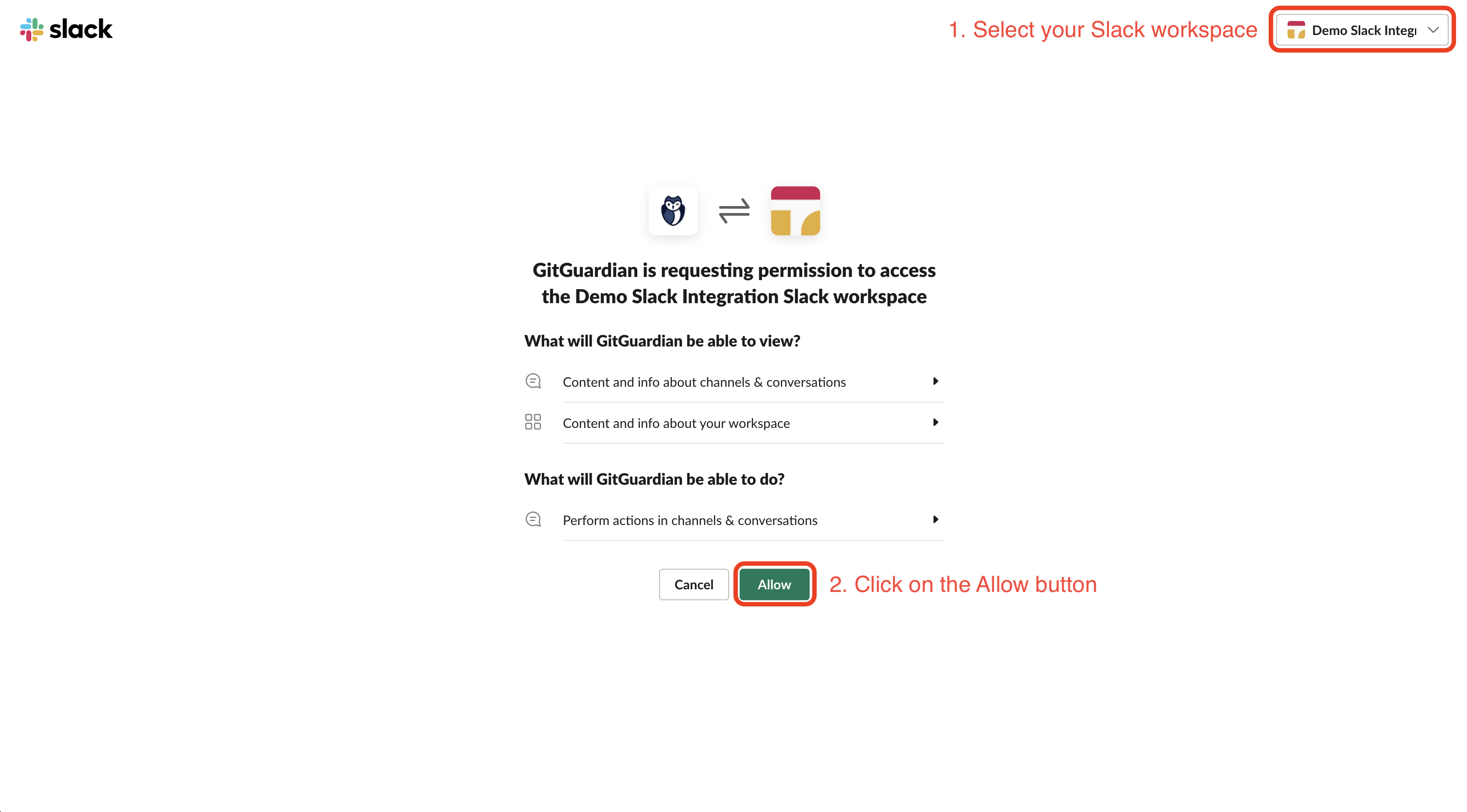
That's it! Our GitGuardian app is now automatically joining all your public channels and will monitor new messages in these channels. You can also invite the GitGuardian app to private channels to monitor these channels as well.
Integration with GitGuardian Self-Hosted
We recommend using dedicated workers for this integration. For more detailed information on scaling and configuration, please visit our scaling page.
If you are using a self-hosted GitGuardian instance, you must first create and configure a dedicated App on your Slack workspace so that you own the entire data stream. GitGuardian handles it for you programmatically via the creation of your app with a manifest file. This will ensure that your app is appropriately created, with all the necessary permissions.
No action needed on your side, the app will automatically request the following Bot Token Scopes: channels:history, channels:join, channels:read, groups:history, groups:read, team:read, users:read, users:read.email, files:read, chat:write, im:write, reactions:read, reactions:write
1. Create an app on your Slack workspace
If you are a GitGuardian Manager and you have the permissions to create an app on your Slack workspace
- Navigate to the Slack integration page
- Click Configure app on Slack Marketplace from your GitGuardian dashboard
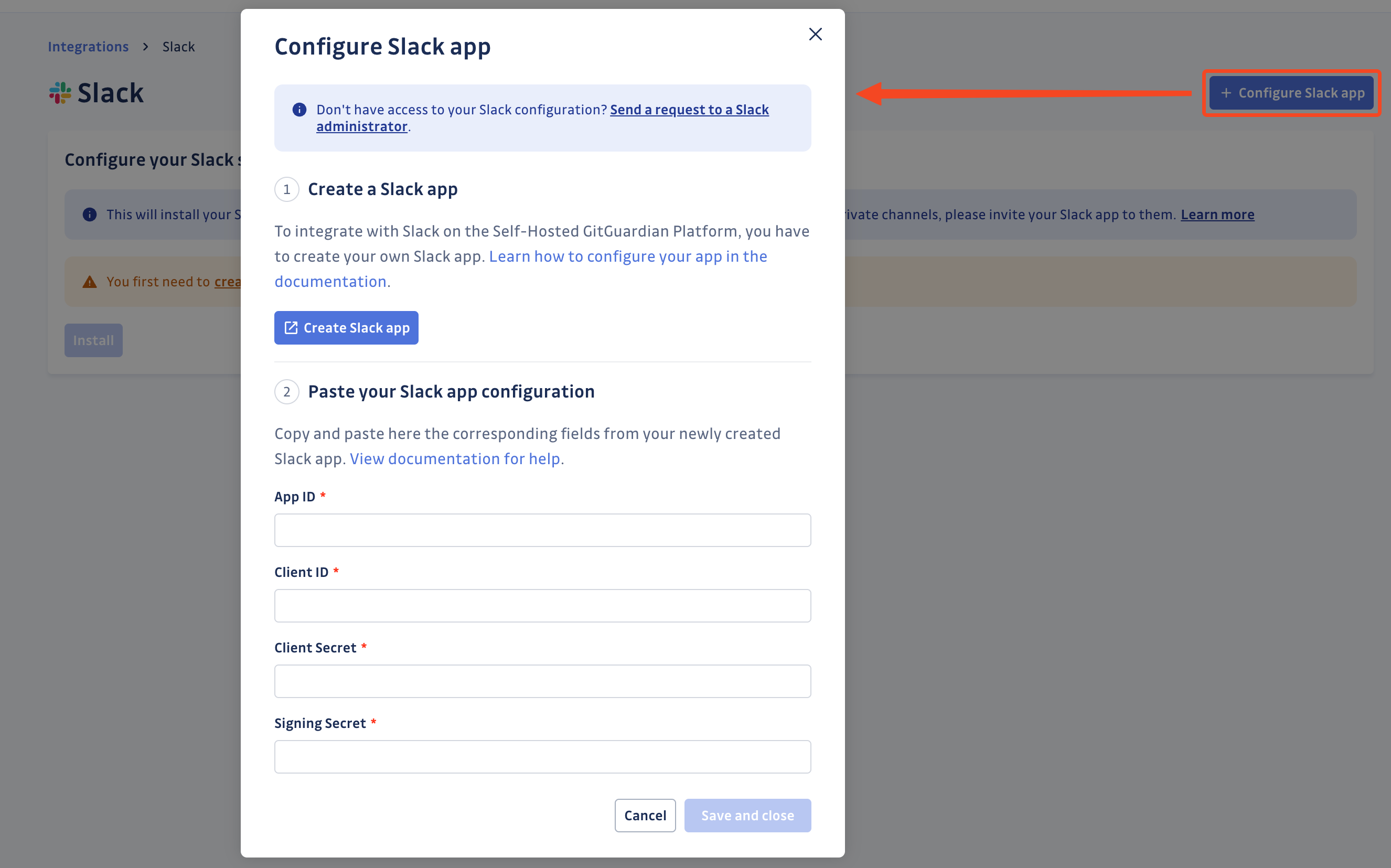
- Click Create app on your Slack workspace from the modal
This will automatically redirect you to your Slack workspace applications, with a dialog modal opened
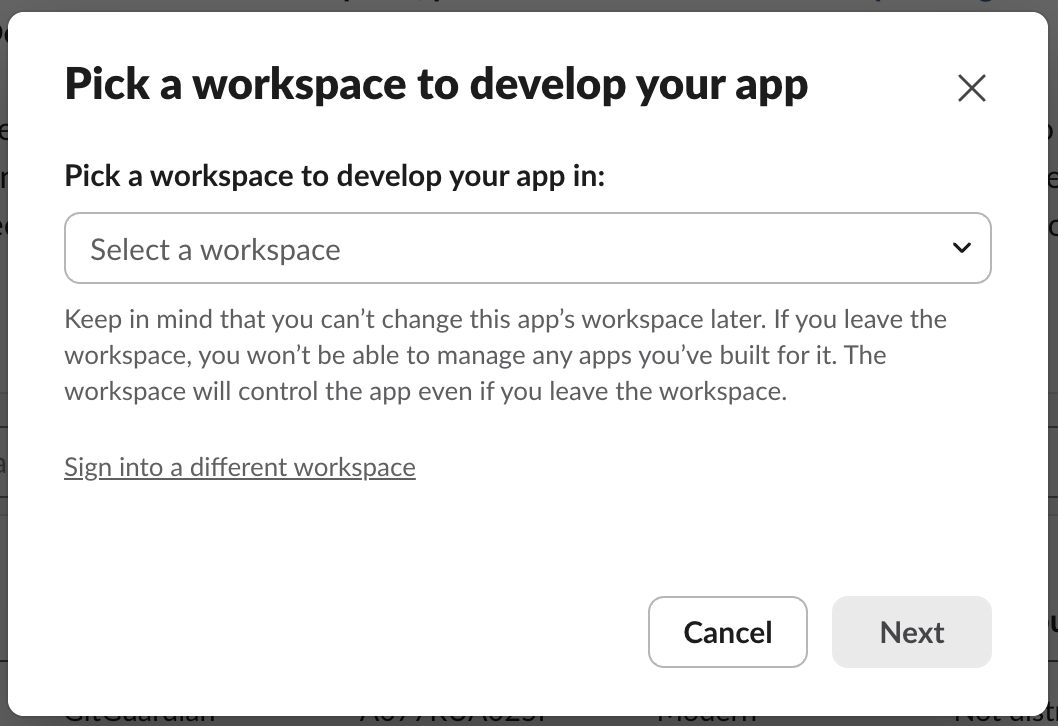
- Select the Slack workspace you would like to monitor with GitGuardian
- Click Next
- You may review details, scopes and configurations set for the app on Slack Marketplace
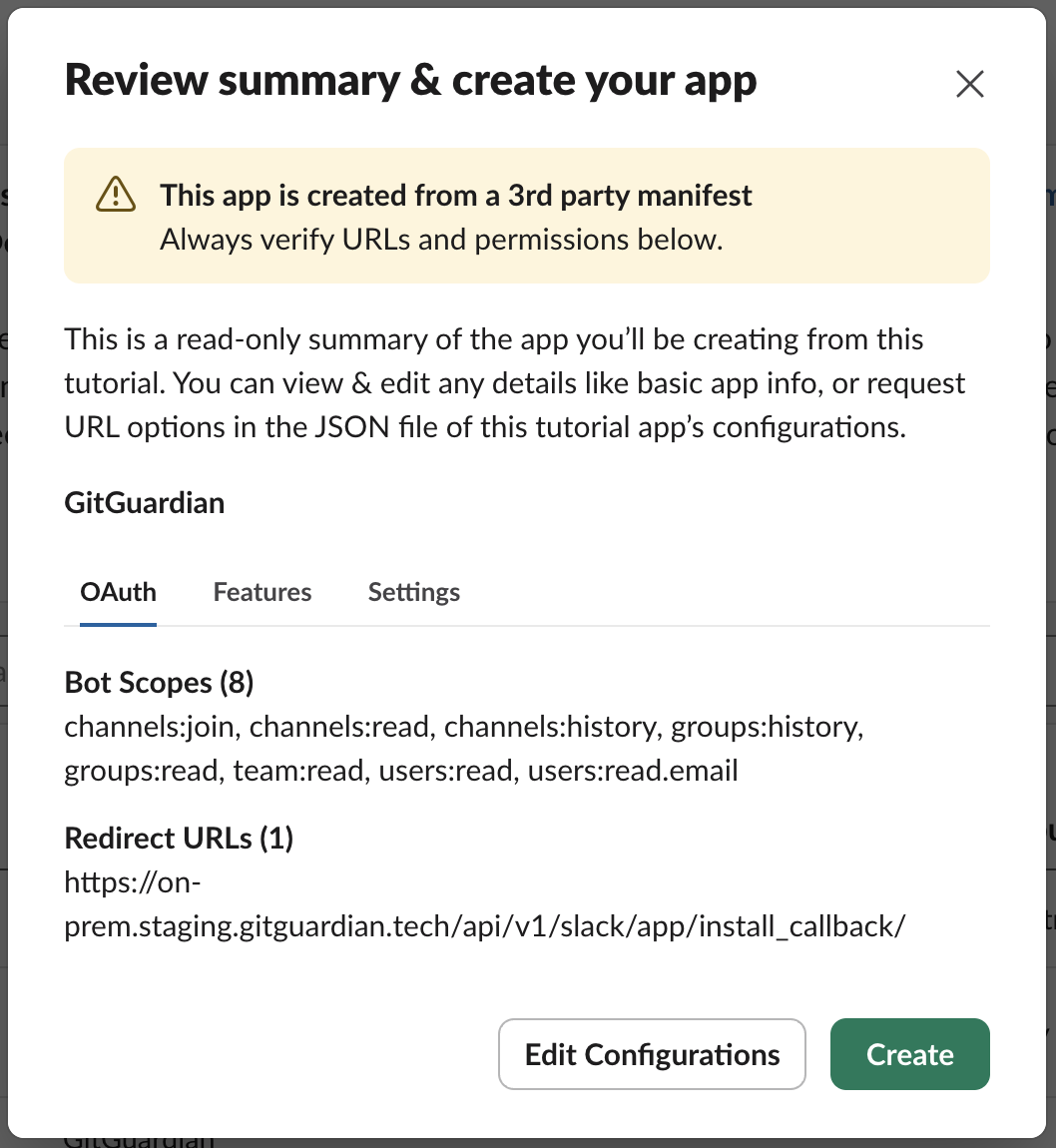
- Click Create
- Go to Settings > Basic Information > App Credentials section
- Get your App Credentials (
App ID,Client ID,Client Secret,Signing Secret) that will be required for the pairing of the app with your GitGuardian workspace
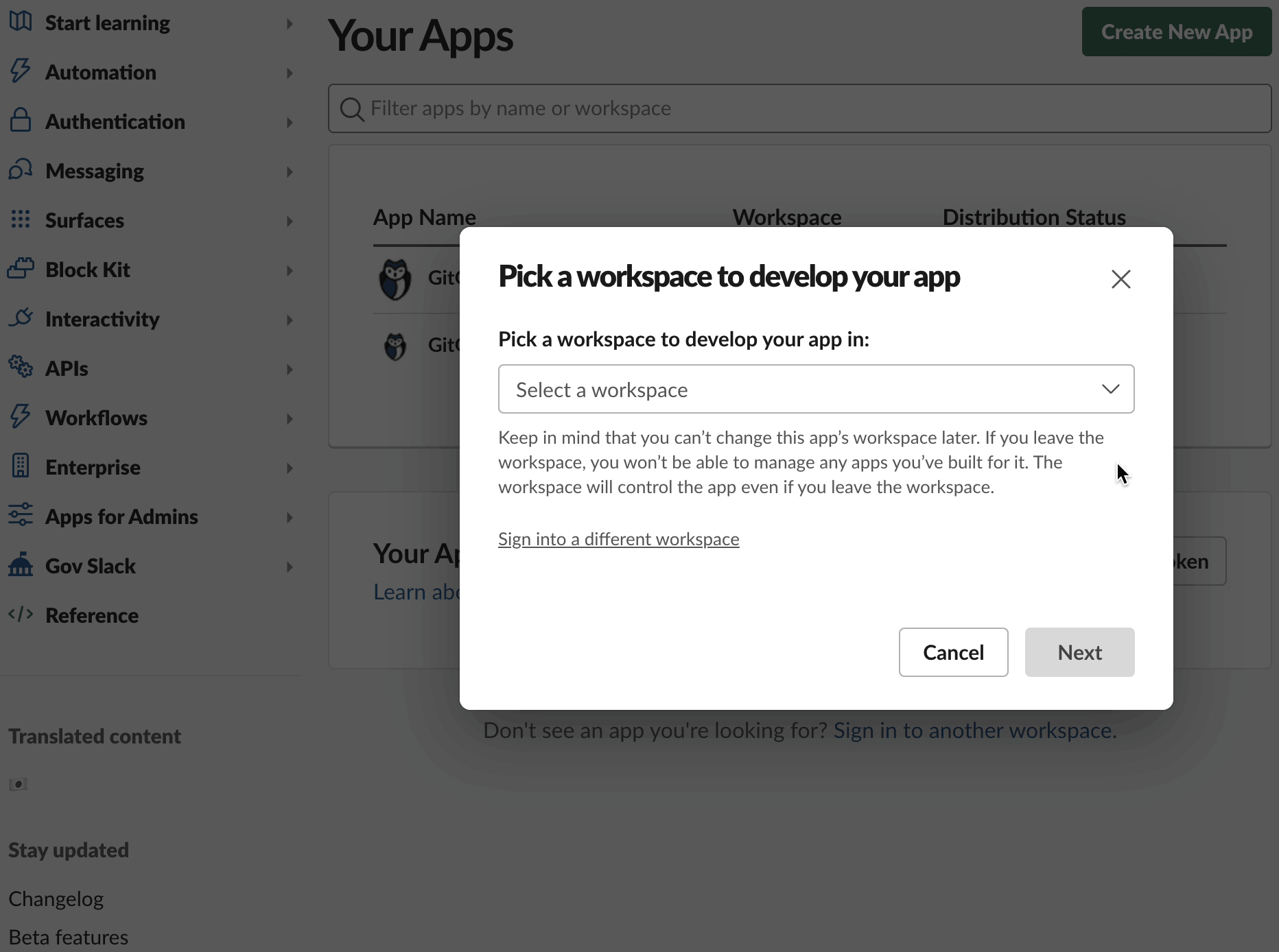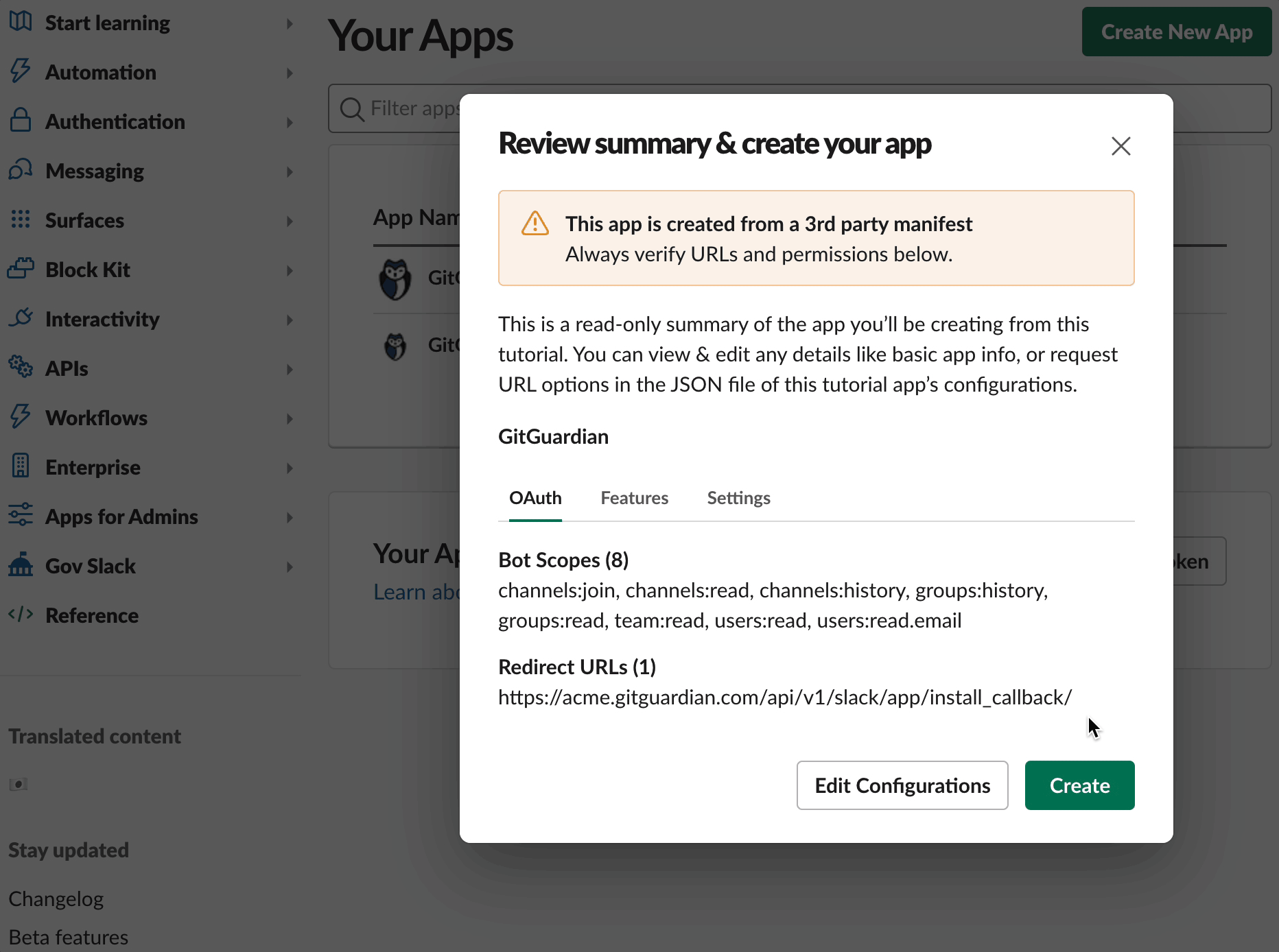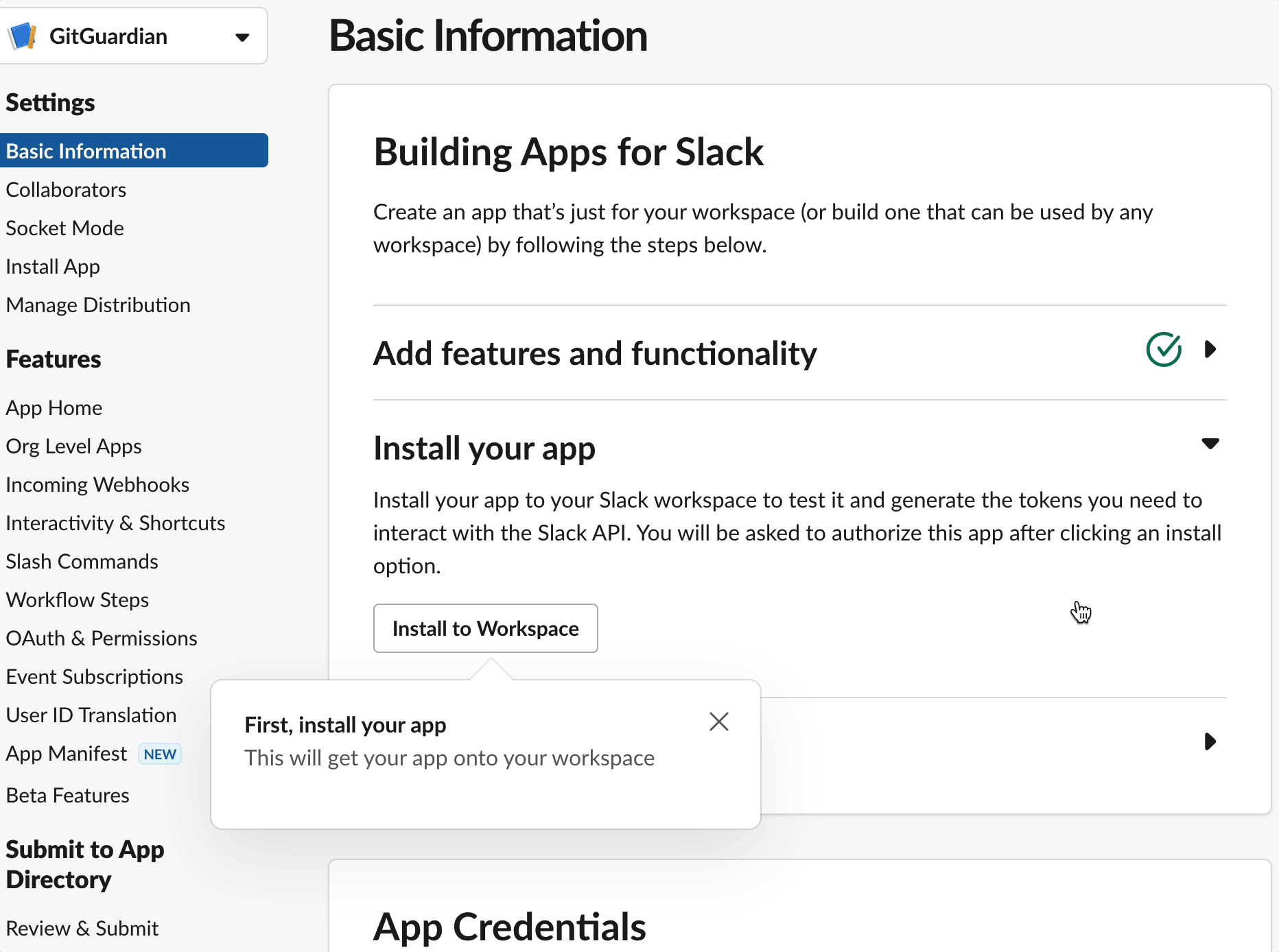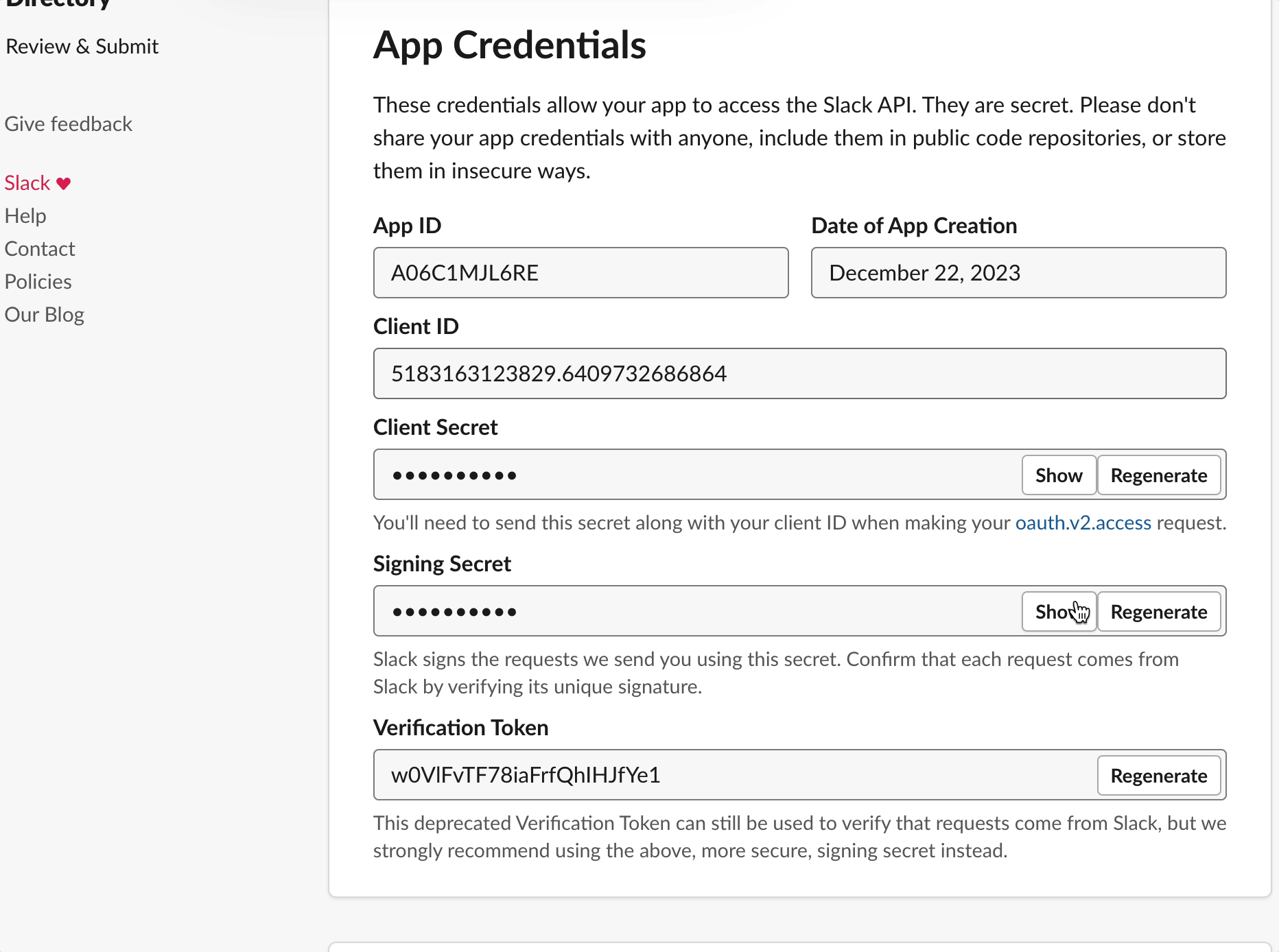
That's it! Your app on Slack Marketplace has been created and you can now pair your app on Slack Marketplace with your GitGuardian Platform.
If you are a GitGuardian Manager but you don't have the permissions to create an app on Slack Marketplace
If you don't have the right to create an app on your Slack workspace, please ask your Slack administrator to do it for you. You can easily forward a request with this procedure:
- Navigate to the Slack integration page
- Click Configure app on your Slack workspace

- Click the Send a request to a Slack administrator link to easily forward your request
- They should in turn provide you with the credentials to proceed with the pairing of the app on your Slack workspace with your GitGuardian Platform.
If you are not a GitGuardian Manager but you received a request to create an app on your Slack Workspace
You received a request to create a new an app on your Slack Workspace so you can use GitGuardian to scan your Slack workspace for secrets.
- Go to the App creation page
- Select the Slack workspace on which you will create a new app on your Slack Workspace
- Click Next
- Click Edit Configurations
- Edit the redirect_url and request_url in the manifest to fit with the GitGuardian self-hosted instance URL:
- redirect_url:
- replace:
https://dashboard.gitguardian.com/api/v1/slack/app/install_callback/ - with:
https://<gitguardian.acme.com>/api/v1/slack/app/install_callback/
- replace:
- request_url:
- replace:
https://dashboard.gitguardian.com/api/v1/receiver/slack/ - with:
https://<gitguardian.acme.com>/api/v1/receiver/slack/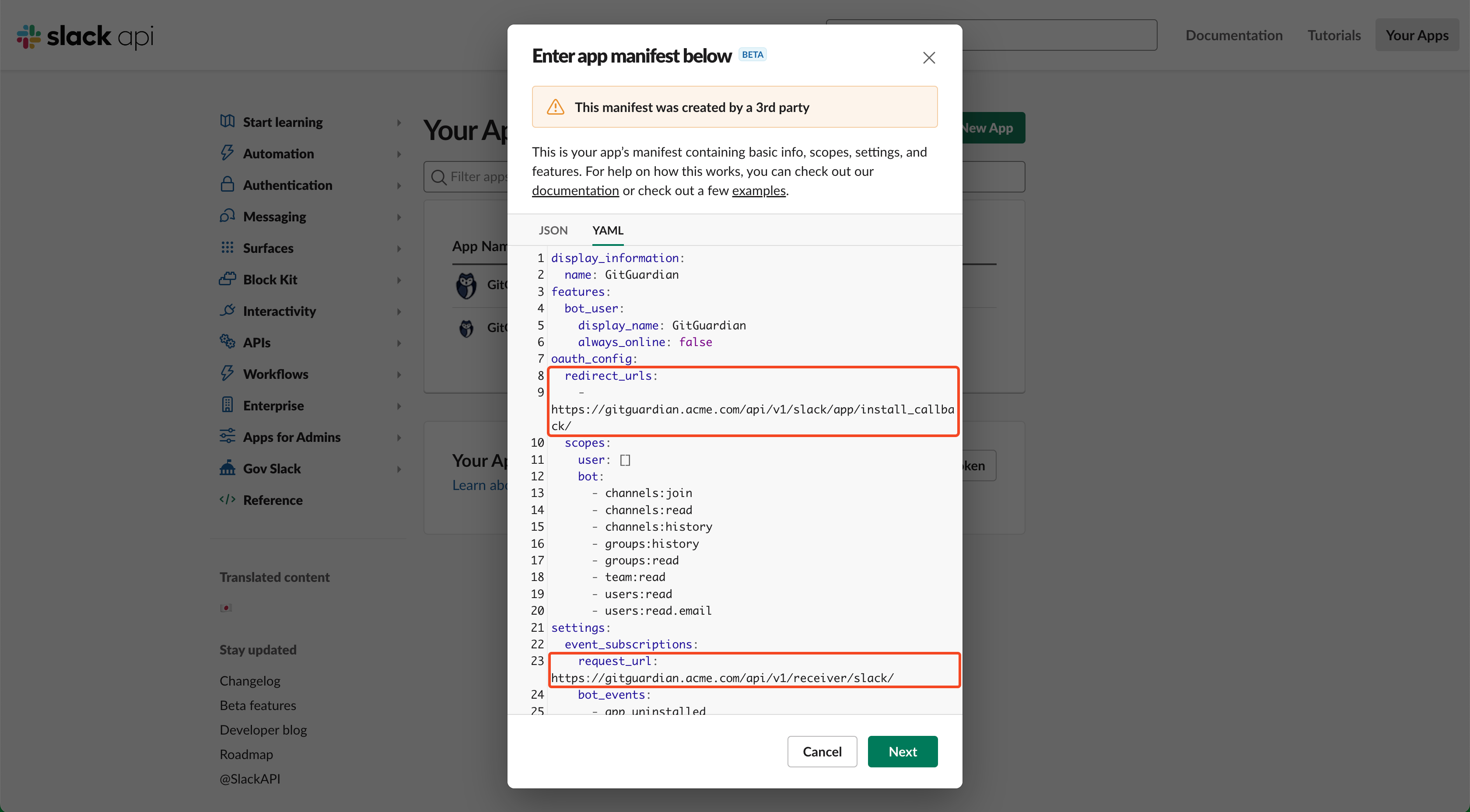
- replace:
- redirect_url:
- Click Next
- Click Create
- Go to Settings > Basic Information > App Credentials section
- Return the App Credentials to your requester in the secure way of your choice (
App ID,Client ID,Client Secret,Signing Secret)
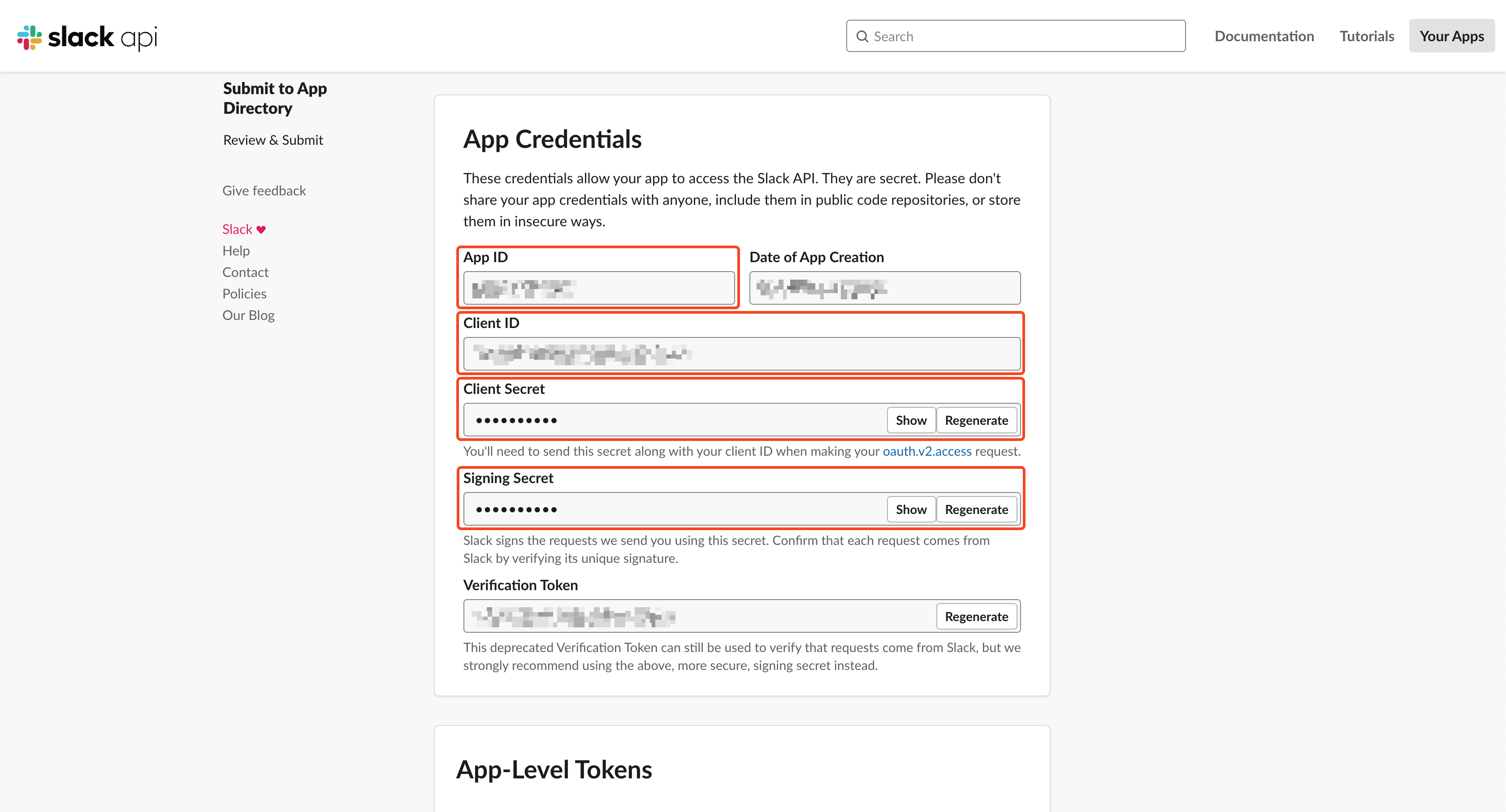
That's it! Your app has been created, and the requester will be able to declare its configuration in the GitGuardian platform.
The Historical Scan feature for Slack workspaces can be affected by Slack API rate limits on *:history scopes.
Please contact your Slack Account Manager for more information.
2. Pair the app on your Slack Workspace with your GitGuardian Platform
- Fill-in the Slack configuration modal opened from your GitGuardian dashboard, with your app credentials (
App ID,Client ID,Client Secret,Signing Secret)
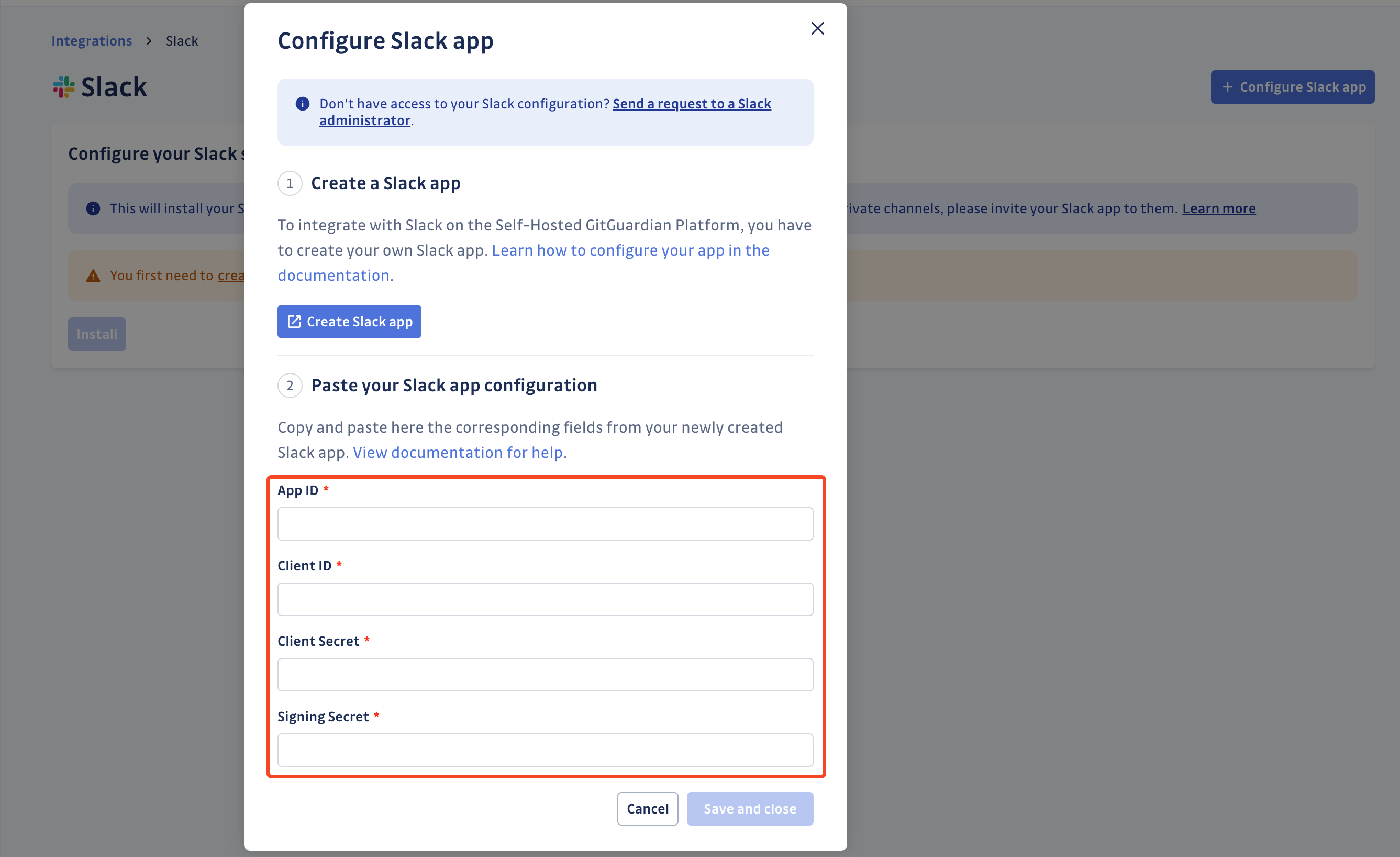
- Click Save and close
Your app is now paired, you now need to finish the installation to start covering your channels.
3. Finish the installation
You can install GitGuardian on multiple Slack workspaces to start monitoring for secret leaks.
- Make sure you're logged in to the Slack workspace you want to install
- On the GitGuardian platform, navigate to the Sources integration page
- Click Install next to Slack in the Messaging section

- Click Install on the Slack integration page
- Select the Slack workspace you want to add
- Click Allow to grant the permissions requested by GitGuardian

That's it! Our GitGuardian app is now automatically joining all your public channels and will monitor new messages in these channels. You can also invite the GitGuardian app to private channels to monitor these channels as well.
Understanding scanning capabilities
Historical scanning
Uncover your secret debt: When you first integrate this source, GitGuardian performs a comprehensive scan of your entire content history, based on your customized perimeter. This reveals secrets that may have been exposed weeks, months, or even years ago - helping you address your existing security debt.
Real-time scanning
Catch new exposures instantly: Once integrated, GitGuardian continuously monitors your content through event-based detection. Any new or modified content containing secrets are detected immediately, allowing you to respond quickly to new exposures.
Extend your coverage to private channels
By default, GitGuardian only scans public channels. We do not access private channels without your consent.
You can also monitor your private channels with the Slack integration. To do so, simply invite our GitGuardian app into the desired private Slack channels:
- Navigate to the private Slack channel of your choice
- Go to the Integrations tab of your channel settings
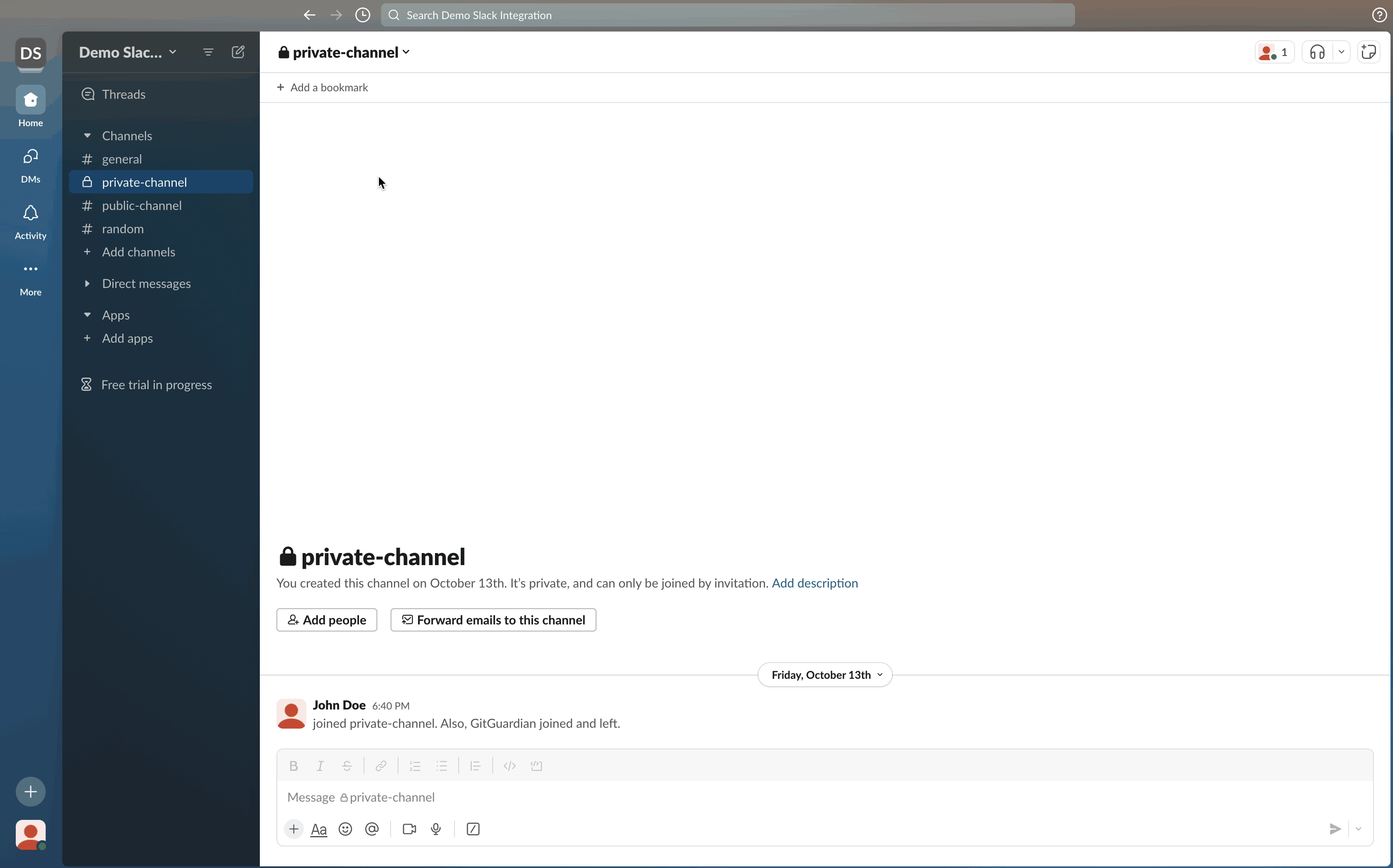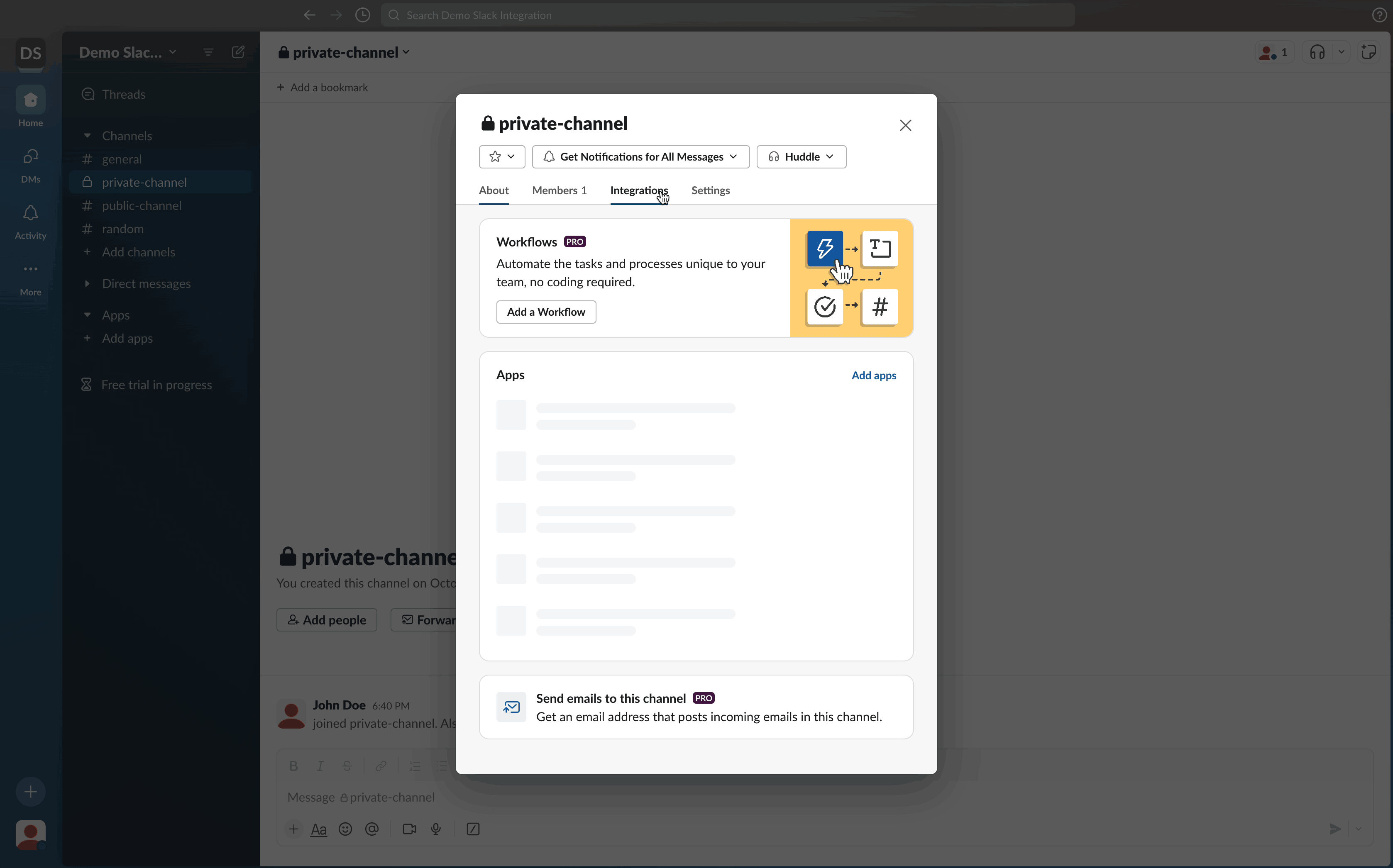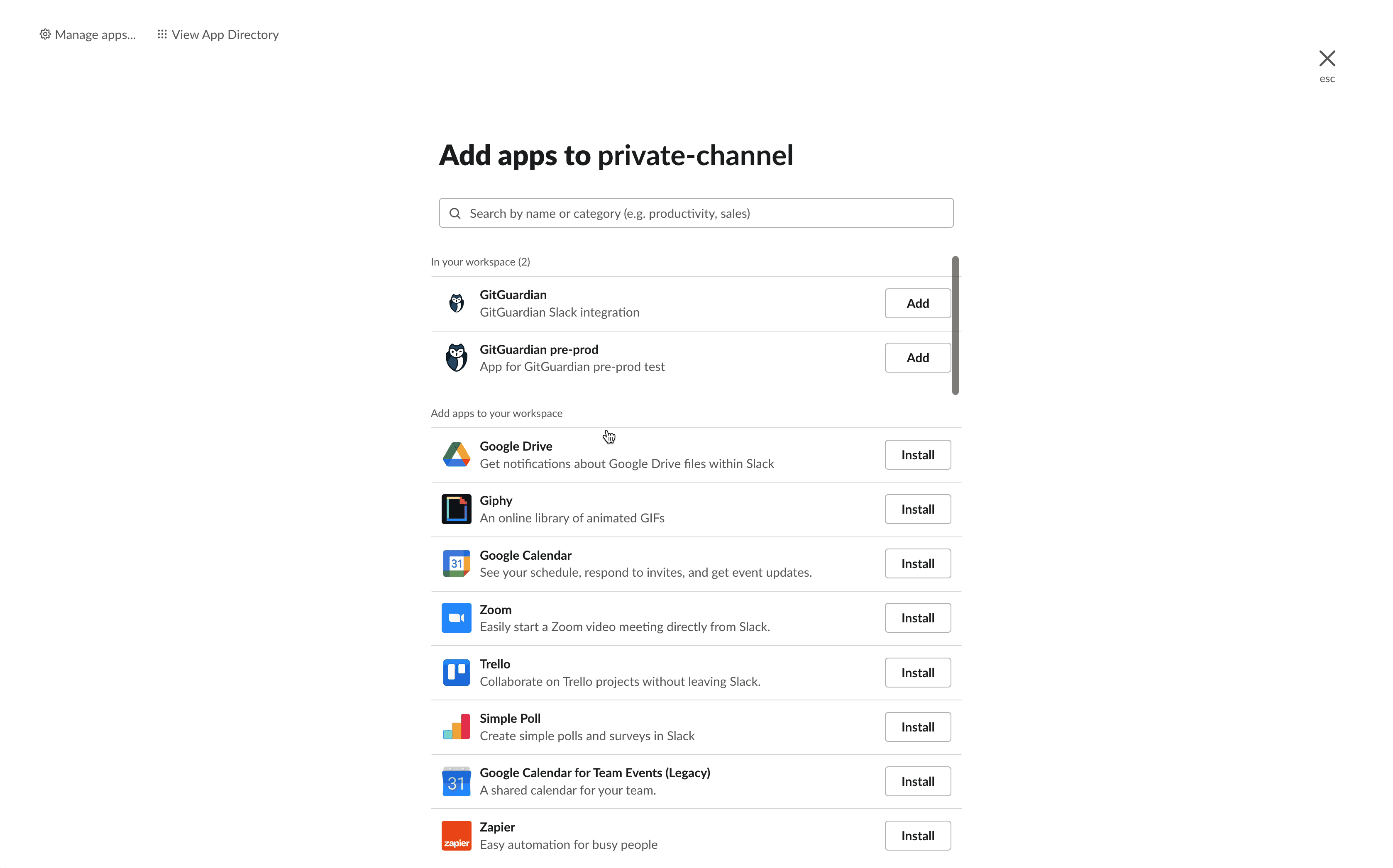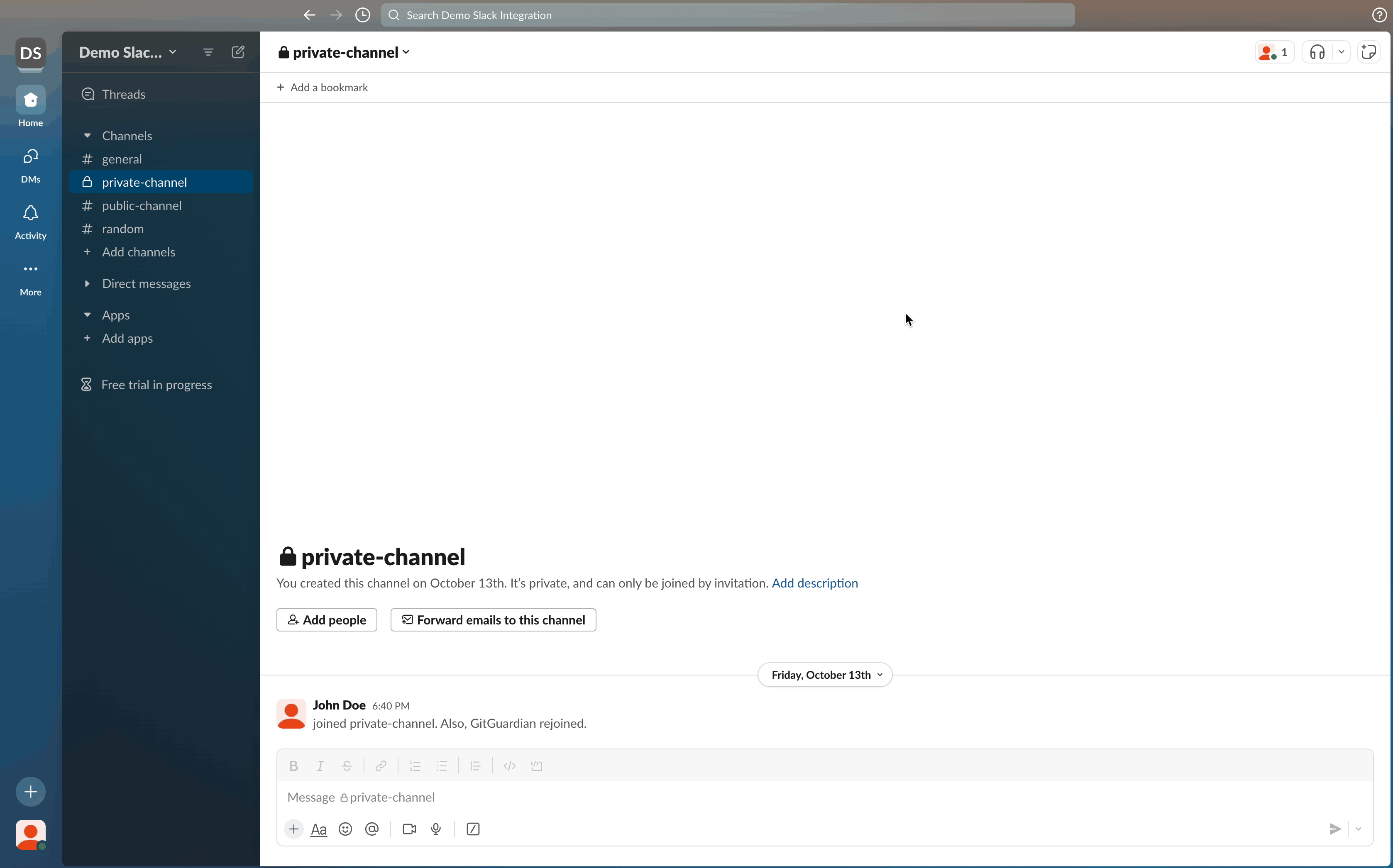
- Click Add an App
- Click Add next to the GitGuardian app
That's it! Our GitGuardian app is now invited to your private channel and ready for monitoring.
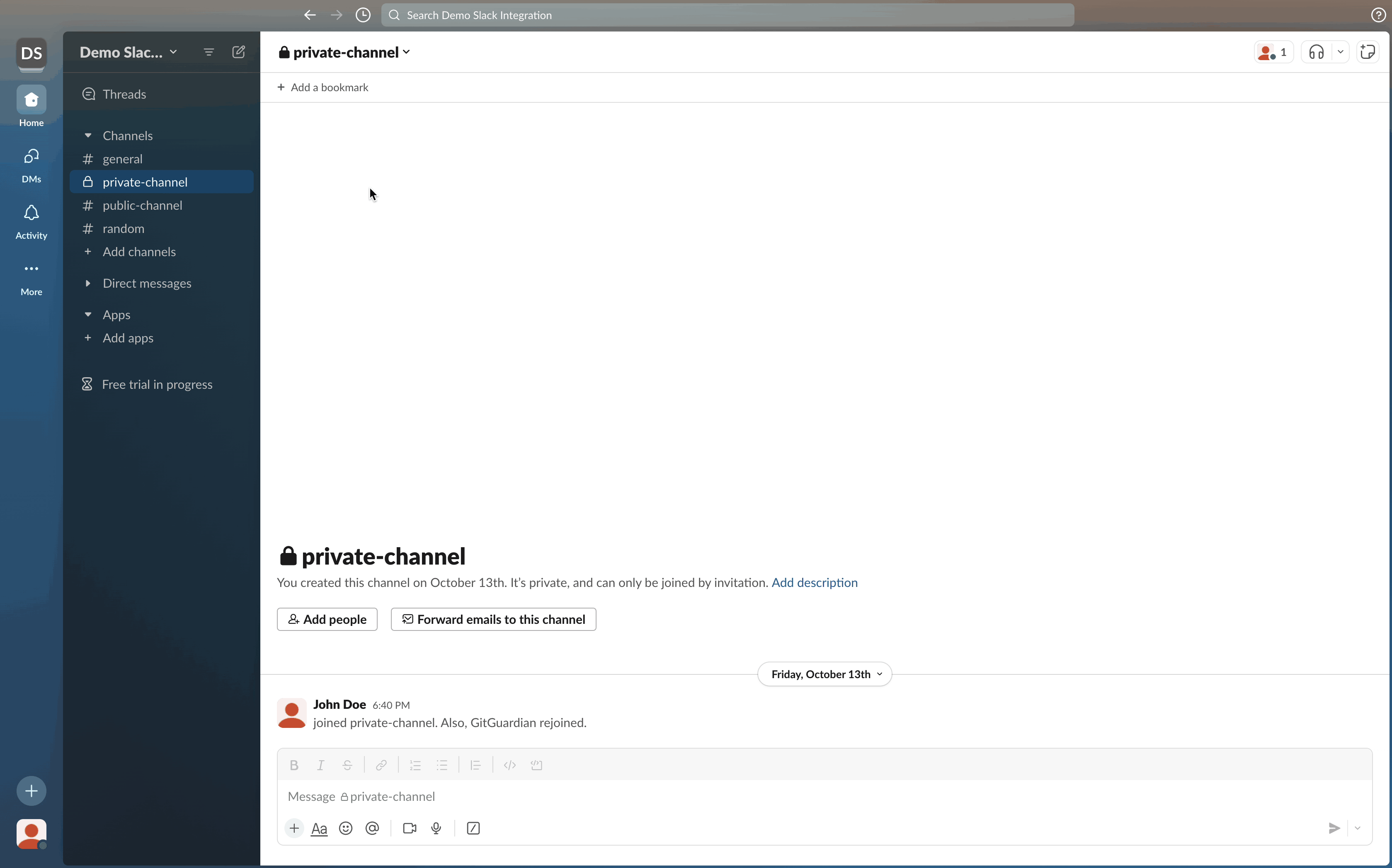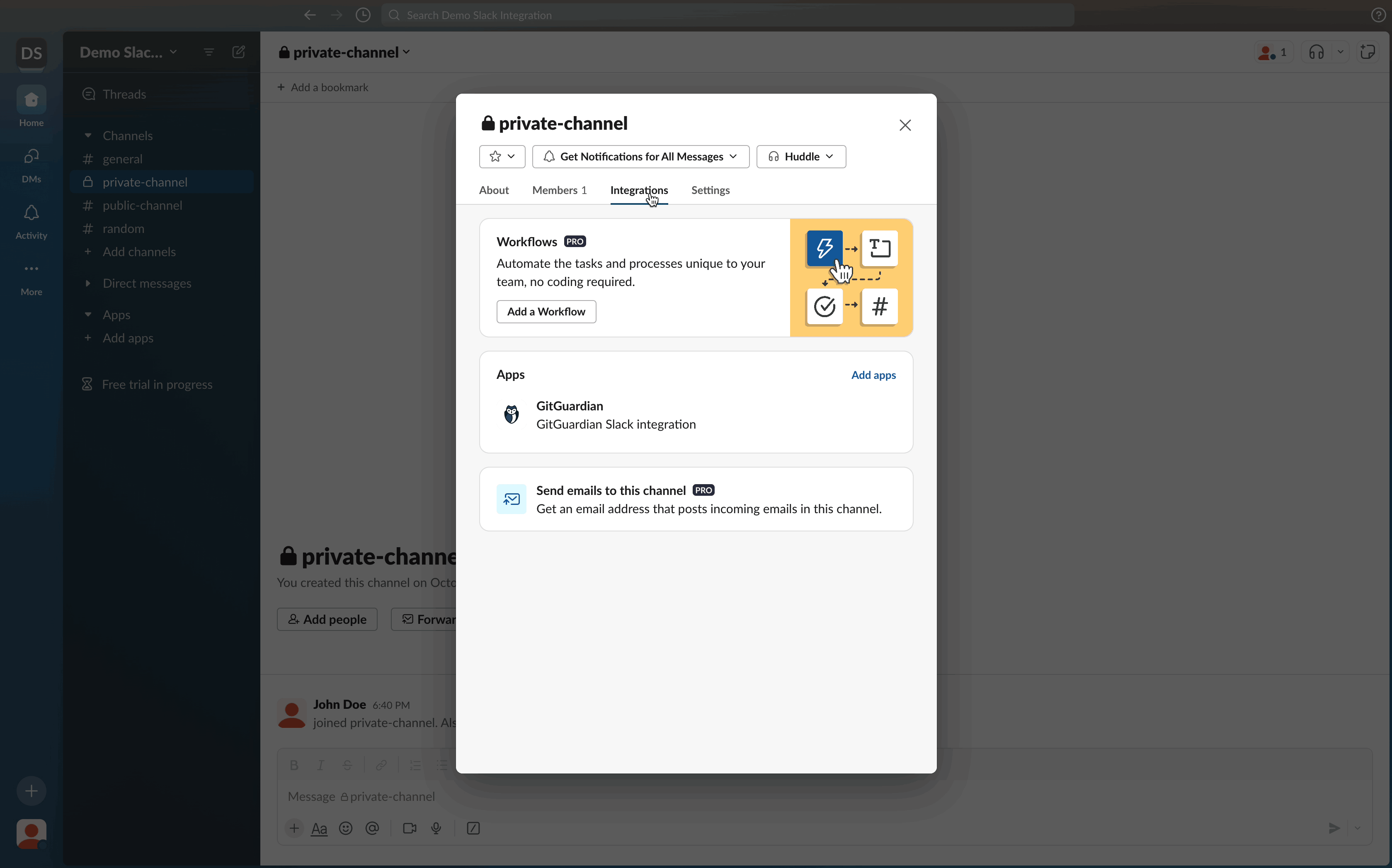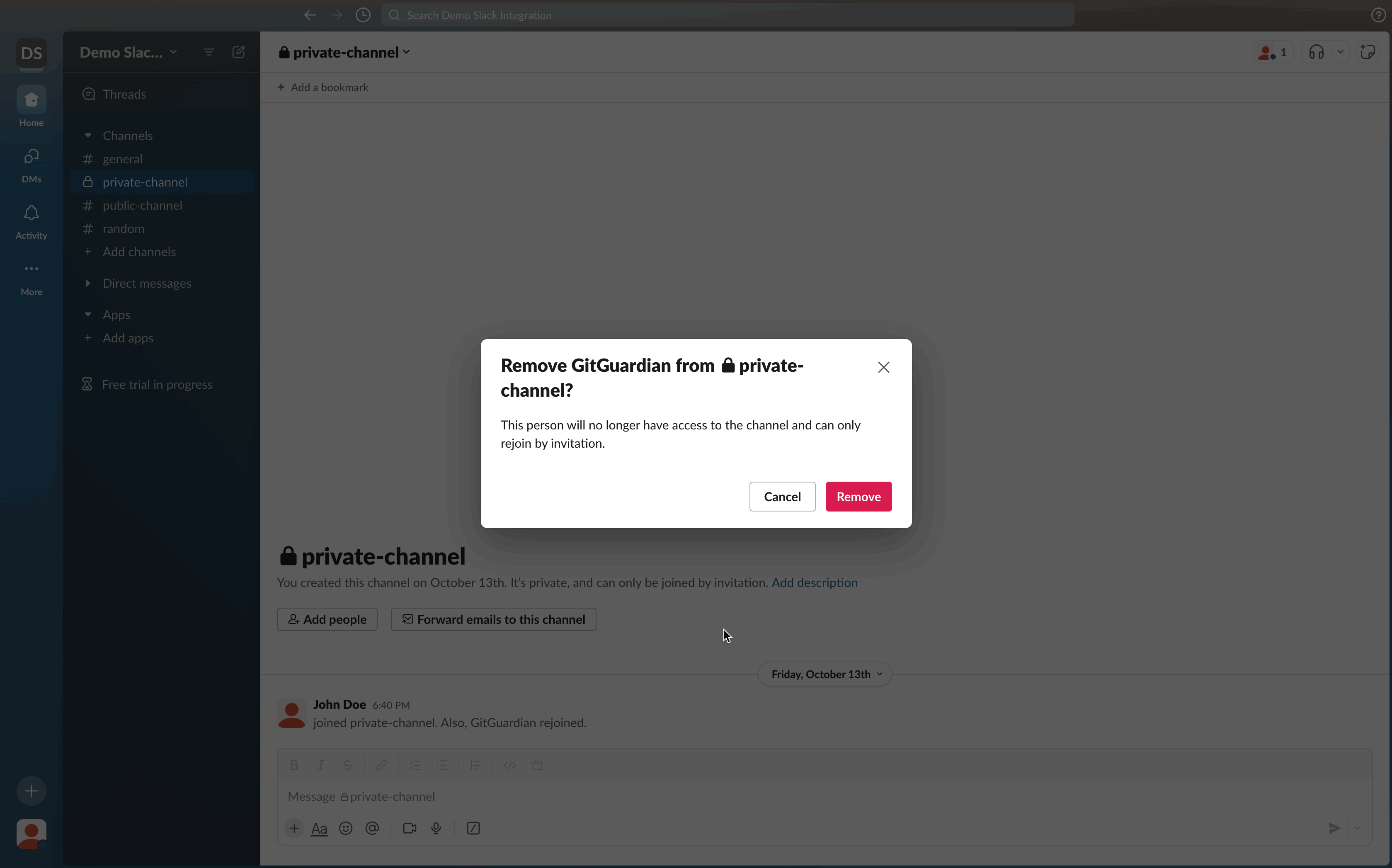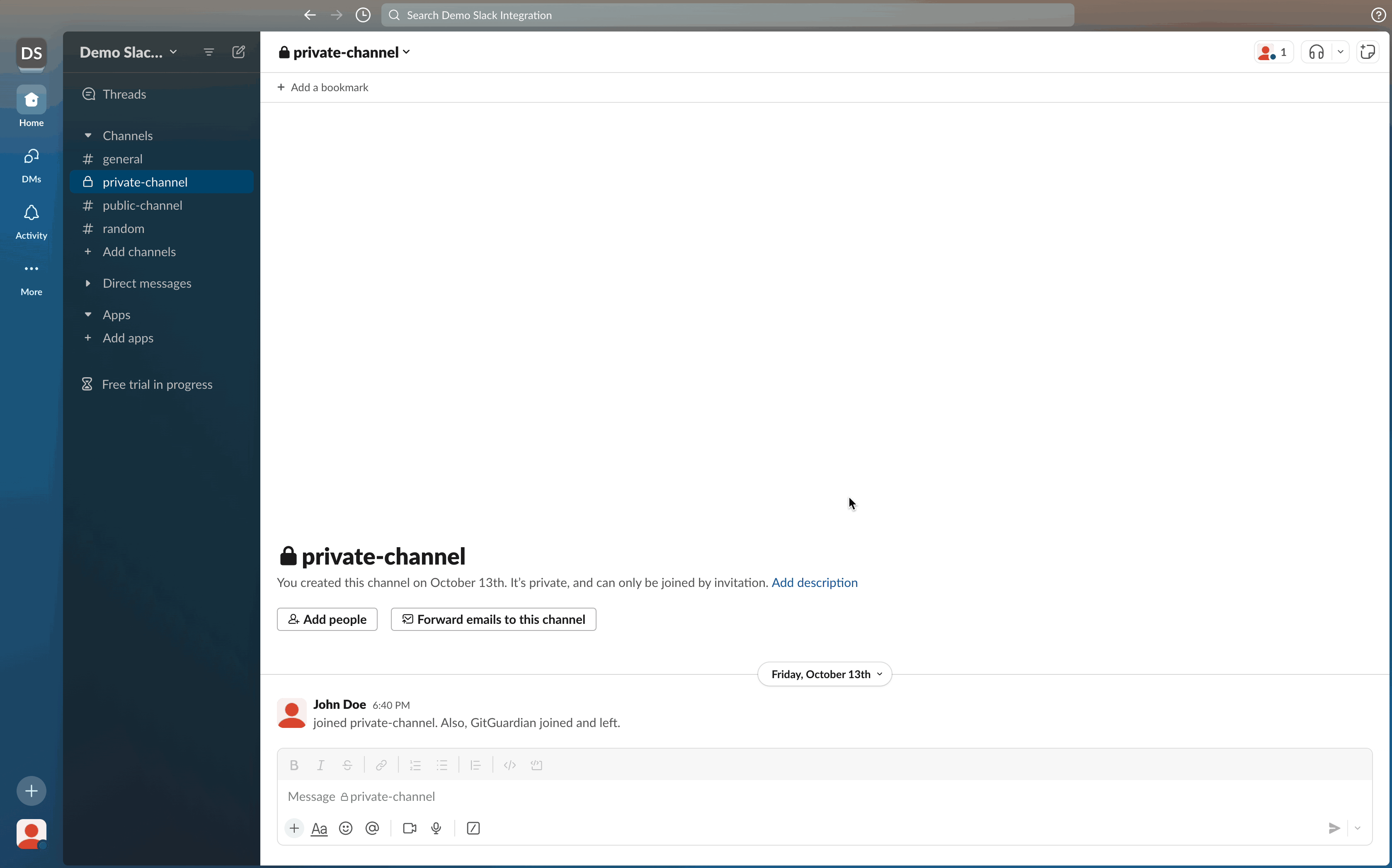
To remove the GitGuardian app from a private Slack channel:
- Navigate to the private Slack channel of your choice
- Go to the Integrations tab of your channel settings
- Click the GitGuardian app
- Select Remove this app from #channel
- Confirm by clicking Remove
That's it! Our GitGuardian app is now removed from your private channel and secret detection is disabled.
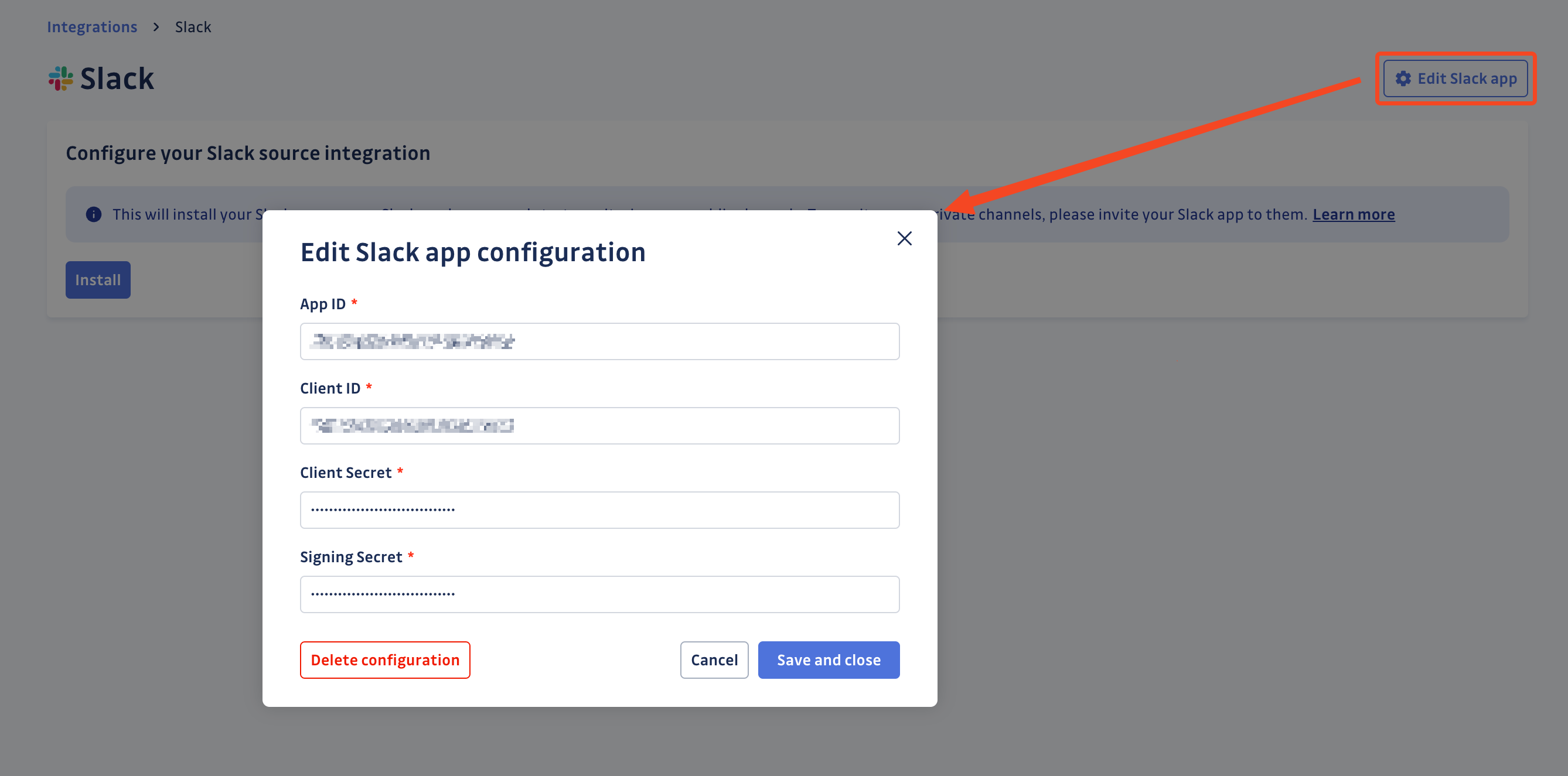
Edit the GitGuardian app on your Slack workspace configuration
In case you need to edit the GitGuardian app on your Slack workspace configuration, due to an error when declaring your credentials or due to a secret rotation, you can do so as follows:
- Click Edit app
- Update your app credentials
- Click Save and close
Delete your GitGuardian app on your Slack workspace configuration
In case you need to delete your GitGuardian app on your Slack workspace configuration, you can do so as follows:
- Click Edit app
- Click Delete configuration
- Confirm by clicking Delete configuration in the confirmation modal
Deleting your GitGuardian app on your Slack workspace configuration will uninstall all your Slack integrations. However, all your existing incidents detected on Slack will remain available on your dashboard. Note that deleting the GitGuardian app on your Slack workspace configuration will only delete the configuration, not the app. If you want to delete your GitGuardian app on your Slack workspace, you must do so from your Slack workspace.
Uninstall your Slack workspace from GitGuardian Platform
To uninstall a Slack workspace:
- In the GitGuardian platform, navigate to the Sources integration page
- Click Edit next to Slack in the Messaging section
- Click the bin icon next to the Slack workspace to uninstall
- Confirm by clicking Uninstall in the confirmation modal
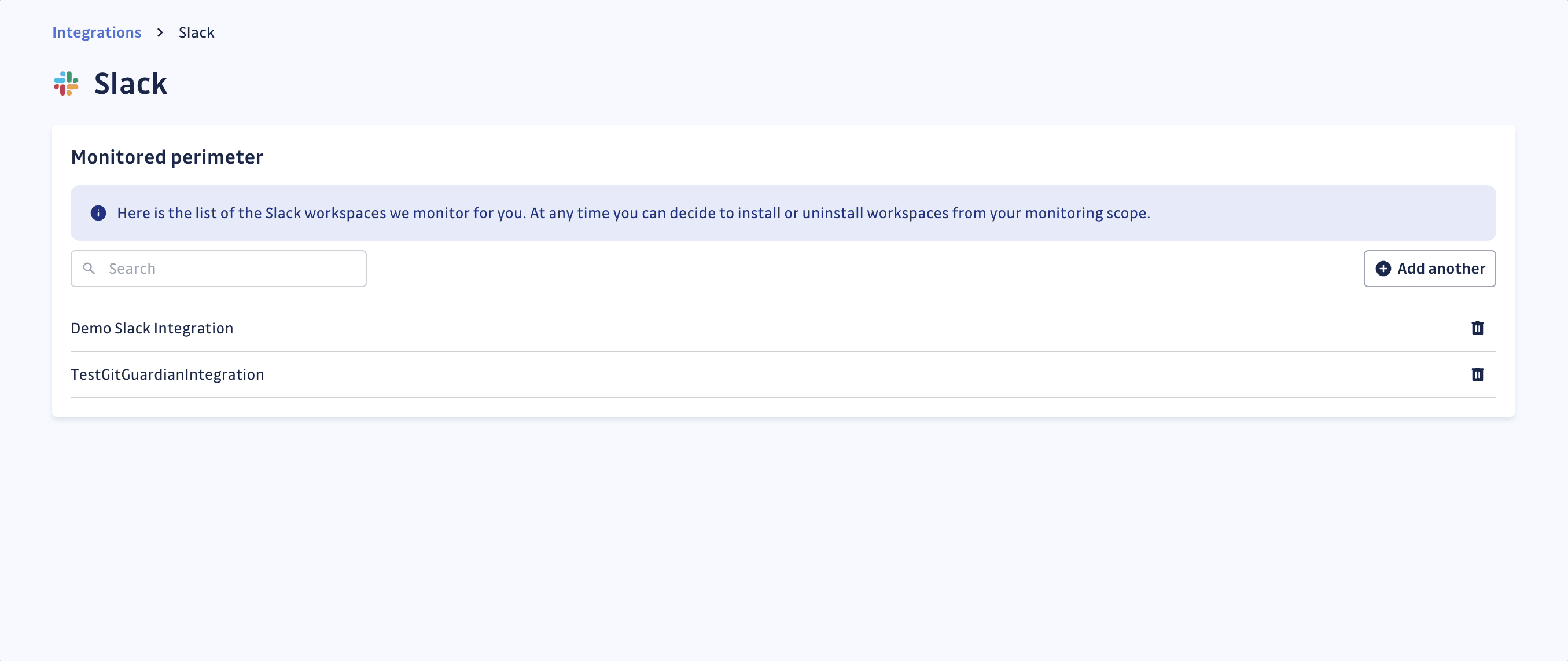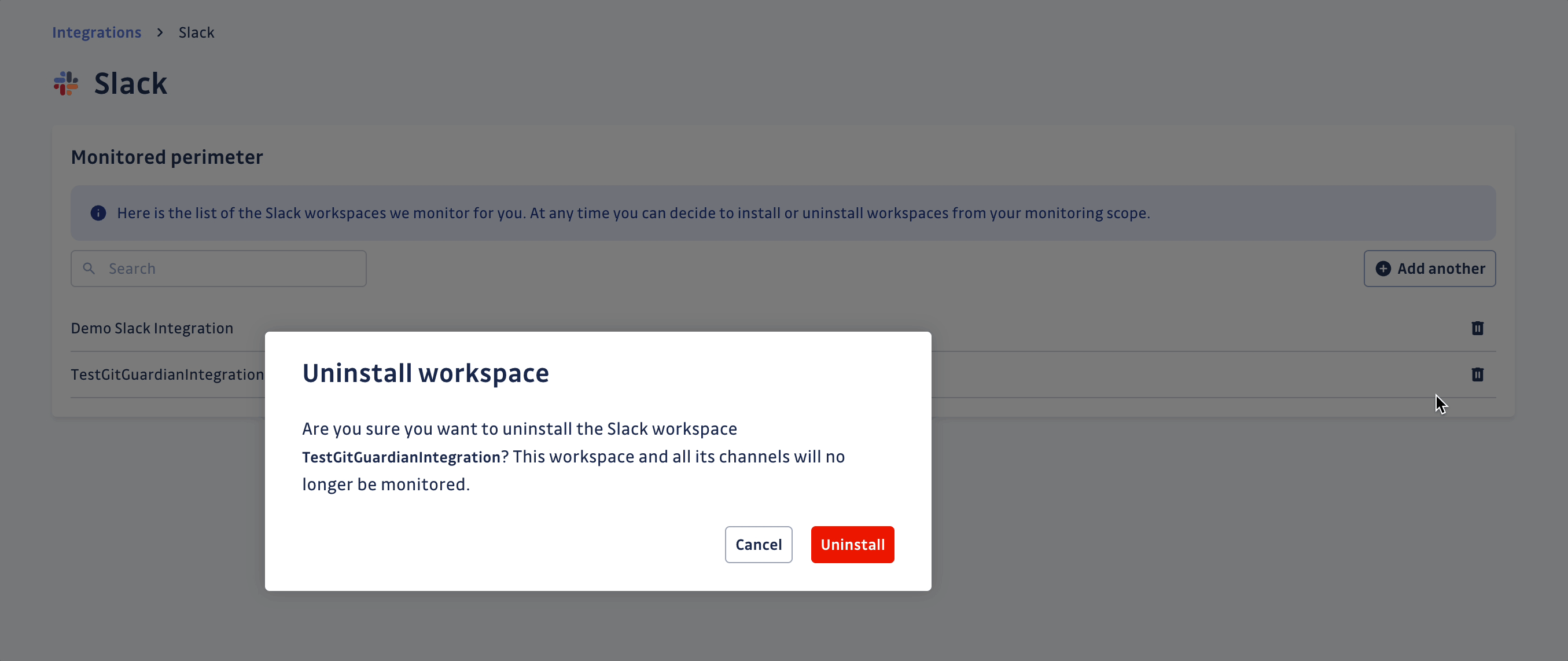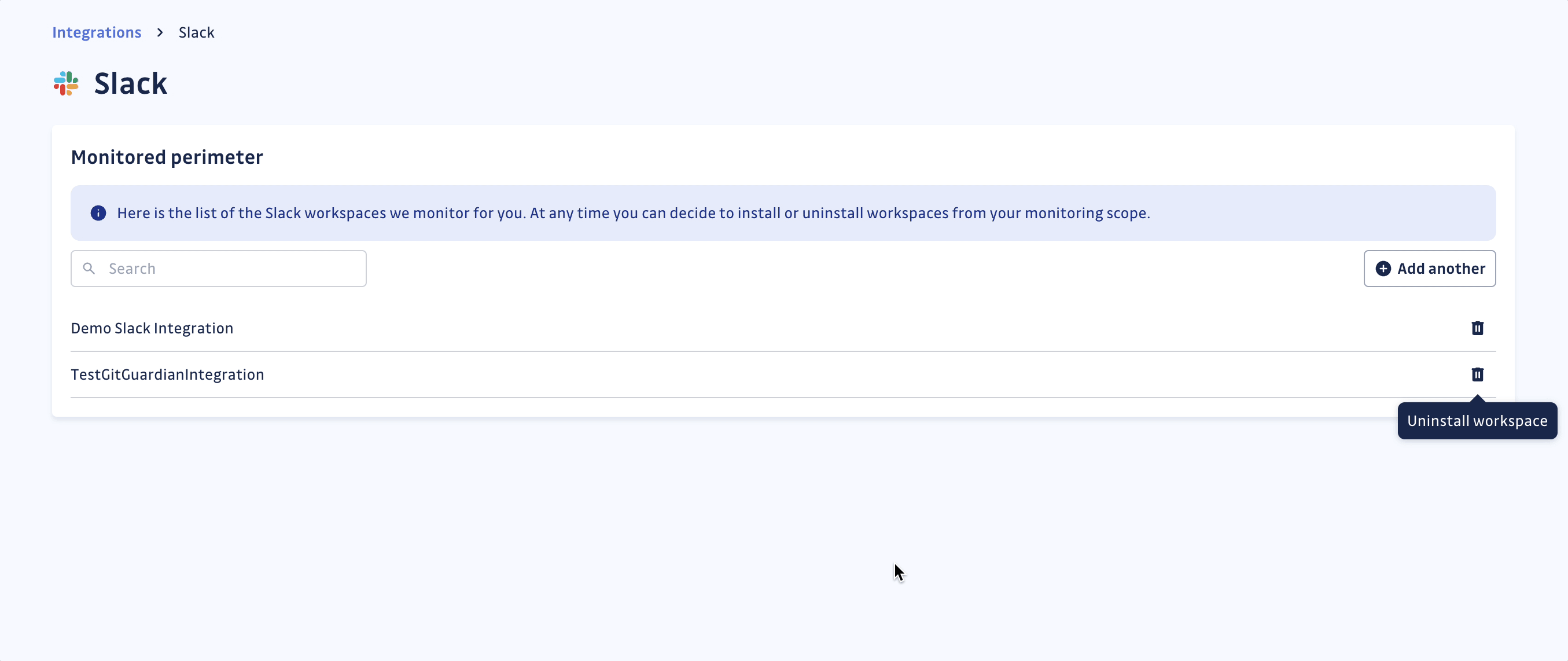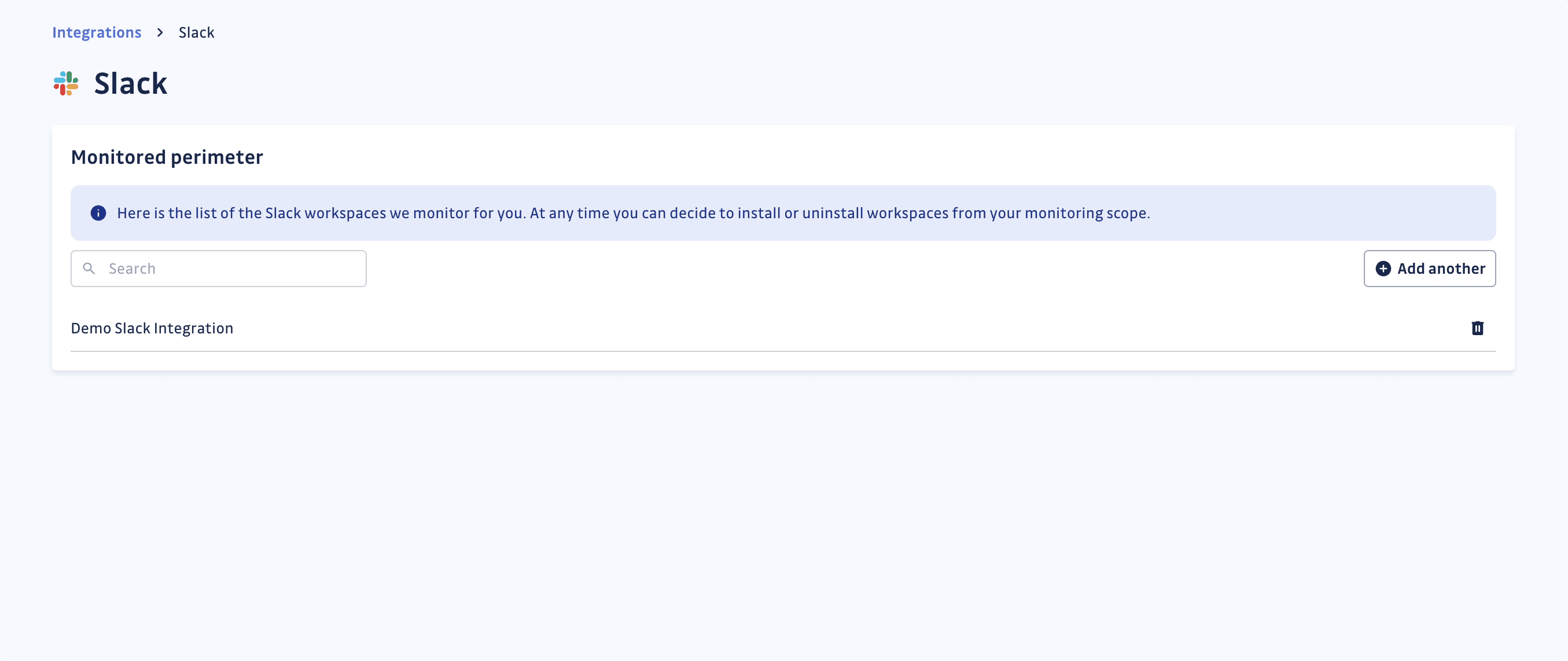
That's it! Your Slack workspace is now uninstalled from GitGuardian Platform.
Slack Interactive Messages
When GitGuardian detects a secret in a Slack message, it automatically sends a threaded response to the original message with interactive actions. This allows users to quickly review and remediate incidents directly within Slack.
How it works
When a secret is detected in a Slack message:
- GitGuardian sends a threaded response in the original Slack thread, reducing channel noise and preserving context.
- The message includes information about the detected secret and provides quick actions.
- Users can ignore the incident directly from Slack using the interactive button.
GitGuardian only triggers one message per incident per thread. Subsequent occurrences of the same secret in the same thread will not generate additional messages.
User identification and permissions
GitGuardian uses the email address associated with the Slack user to find the corresponding user in the GitGuardian application. This matched user must have the appropriate permissions to perform actions on incidents.
- To ignore an incident from Slack, the user must have the Ignore incidents permission in GitGuardian.
- If a user does not have the necessary permissions, they will see an error message when attempting to ignore an incident.
Interactive message types
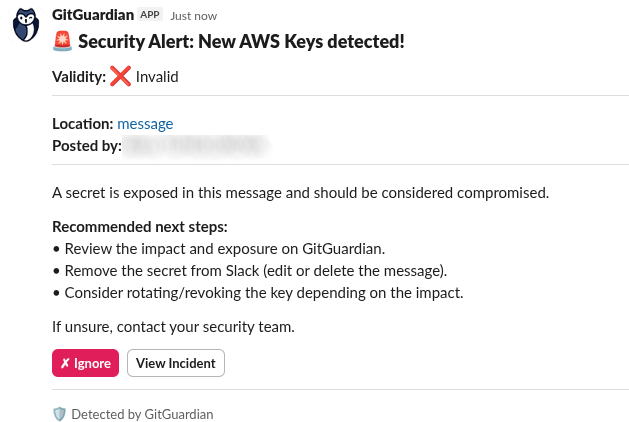
Secret detected
When a secret is detected, GitGuardian posts a threaded message containing:
- Detector Type: The type of secret detected (e.g., AWS Access Key, GitHub Token)
- Validity: Whether the secret is valid or invalid (✅ Valid, ❌ Invalid)
- Location: Link to the original message
- Posted by: The author who posted the secret
Available actions:
- View Incident: Opens the incident detail page in GitGuardian
- Ignore: Ignores the incident with the reason "This is a low risk secret"
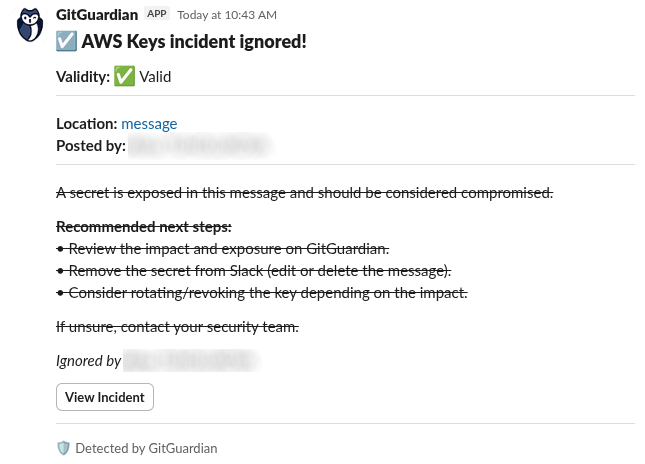
Incident ignored
When an incident is ignored via the Slack interactive message, the original message is updated to reflect the new status:
- Shows the incident has been ignored
- Displays who resolved the incident
- Removes the action buttons
Synchronization with GitGuardian Dashboard
The synchronization between Slack and GitGuardian dashboard is one-way for actions performed in GitGuardian:
- Slack → GitGuardian: When an incident is ignored through the Slack interactive message, it will be reflected in the GitGuardian dashboard.
- GitGuardian → Slack: When an incident is resolved or ignored from the GitGuardian dashboard, the Slack interactive message will NOT be updated and no new message will be sent.
Error scenarios
App reinstallation required
If the installation was done before the 27th of January 2026, you will need reinstall Slack integration and accept the newly added scope chat:write.
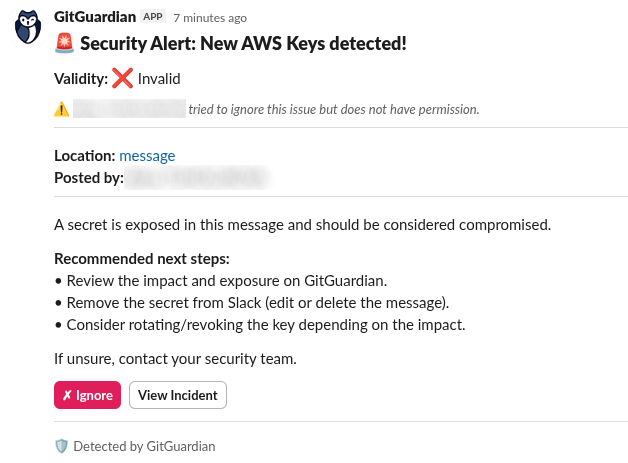
Insufficient permissions
If a user attempts to ignore an incident but does not have the required permissions in GitGuardian, they will see an error message indicating they do not have permission to perform this action.
Privacy and compliance
Data handling
GitGuardian processes your data solely to detect exposed secrets:
- Read-only access: We never require write access unless scoped to creating webhooks to receive and process real-time events
- Minimal data retention: We store only data and metadata necessary for incident management
- Encryption: All data in transit and at rest is encrypted
- Compliance: We follow the same data protection standards as our other integrations
Regional considerations
GitGuardian hosts its services in two AWS regions: eu-central-1 (Frankfurt) and us-west-2 (Oregon). Ensure your GitGuardian deployment region aligns with your data residency requirements. Contact support if you need guidance on compliance with local regulations.
App permissions
The specific permissions used by our applications are listed on the corresponding Slack Marketplace pages:
User notification
Country-specific laws and regulations may require you to inform your Slack users that your channels are being scanned for secrets. Here is a suggestion for a message you may want to use:
As part of our internal information security process, the company scans the Slack channels for potential secrets leaks using GitGuardian. All data collected will be processed for the purpose of detecting potential leaks. To find out more about how we manage your personal data and to exercise your rights, please refer to our employee/partner privacy notice.
Please note that only channels relating to the company's activity and business may be monitored and that users shall refrain from sharing personal or sensitive data not relevant to the channel's purpose.

