Integrate a new Azure Container Registry source
This integration leads to an automatic full scan of your monitored repositories. This implies an initial download of your Docker images, which may incur bandwidth costs with your Cloud Provider. To reduce these costs, while minimizing the risk of false positives, we recommend you to take advantage of the Filepath exclusion feature by adding this suggestion of filepaths to exclude from scanning.
Setting up and configuring this integration is limited to users with an Owner or Manager access level. Azure Container Registry installation is only open to workspaces under the Business plan. However, you can install and test secret detection in Azure Container Registry with a 30-day trial. Any secret incidents detected during the trial will remain accessible in your incident dashboard.
GitGuardian integrates natively with Azure Container Registry via a Token that you can create from your Azure Container Registry instance. Note that GitGuardian only has read access to your repositories.
Setup your Azure Container Registry integration
You can install GitGuardian on multiple Azure Container Registry instances to monitor your repositories.
-
Make sure you're logged as an administrator in your Azure Portal
-
Browse your Container Registries and select the one you want to integrate
-
Go to the Overview section
-
Copy the Login server
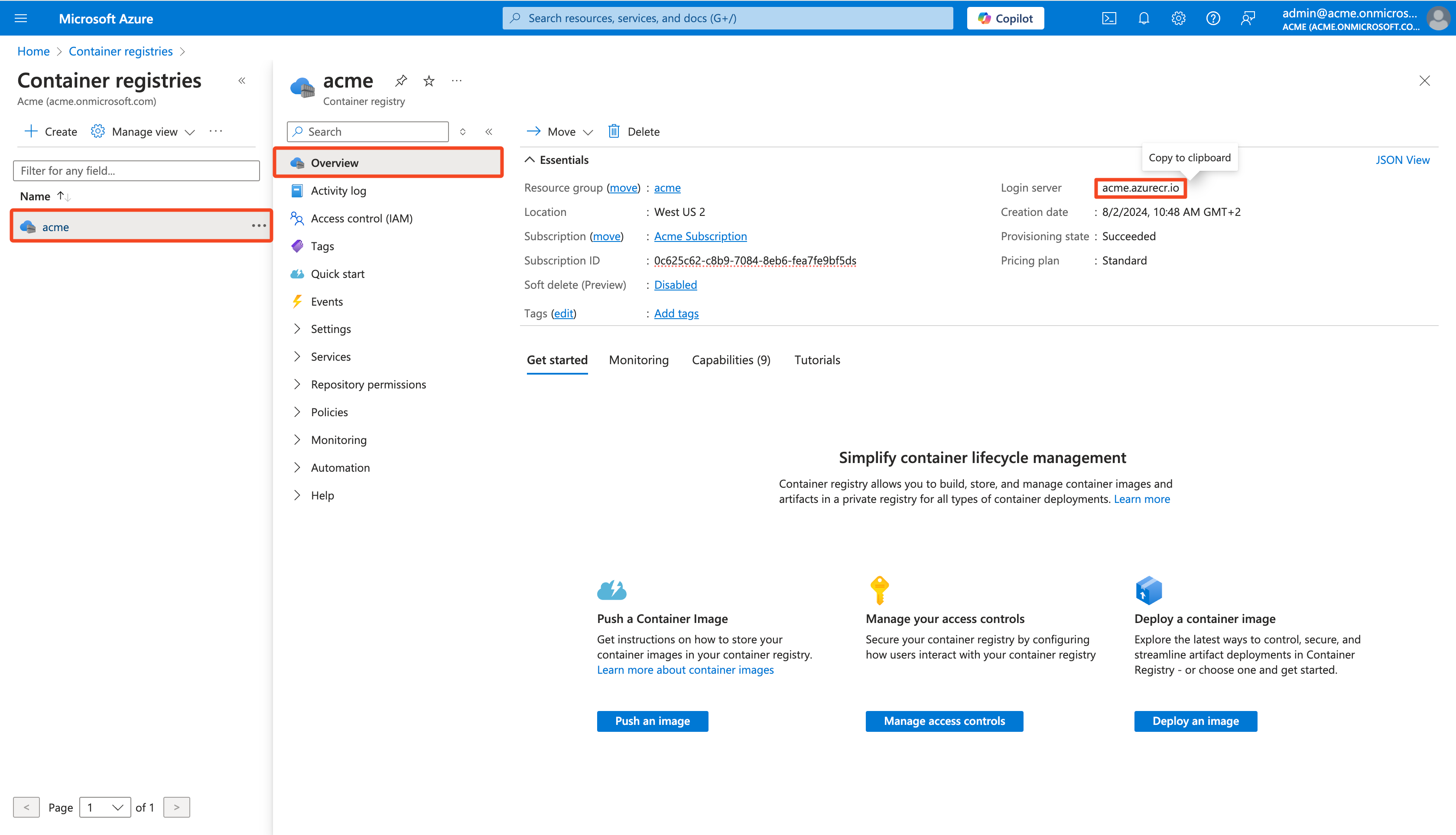
-
Go to the Repository permissions > Tokens section
-
Click Add to create a new token
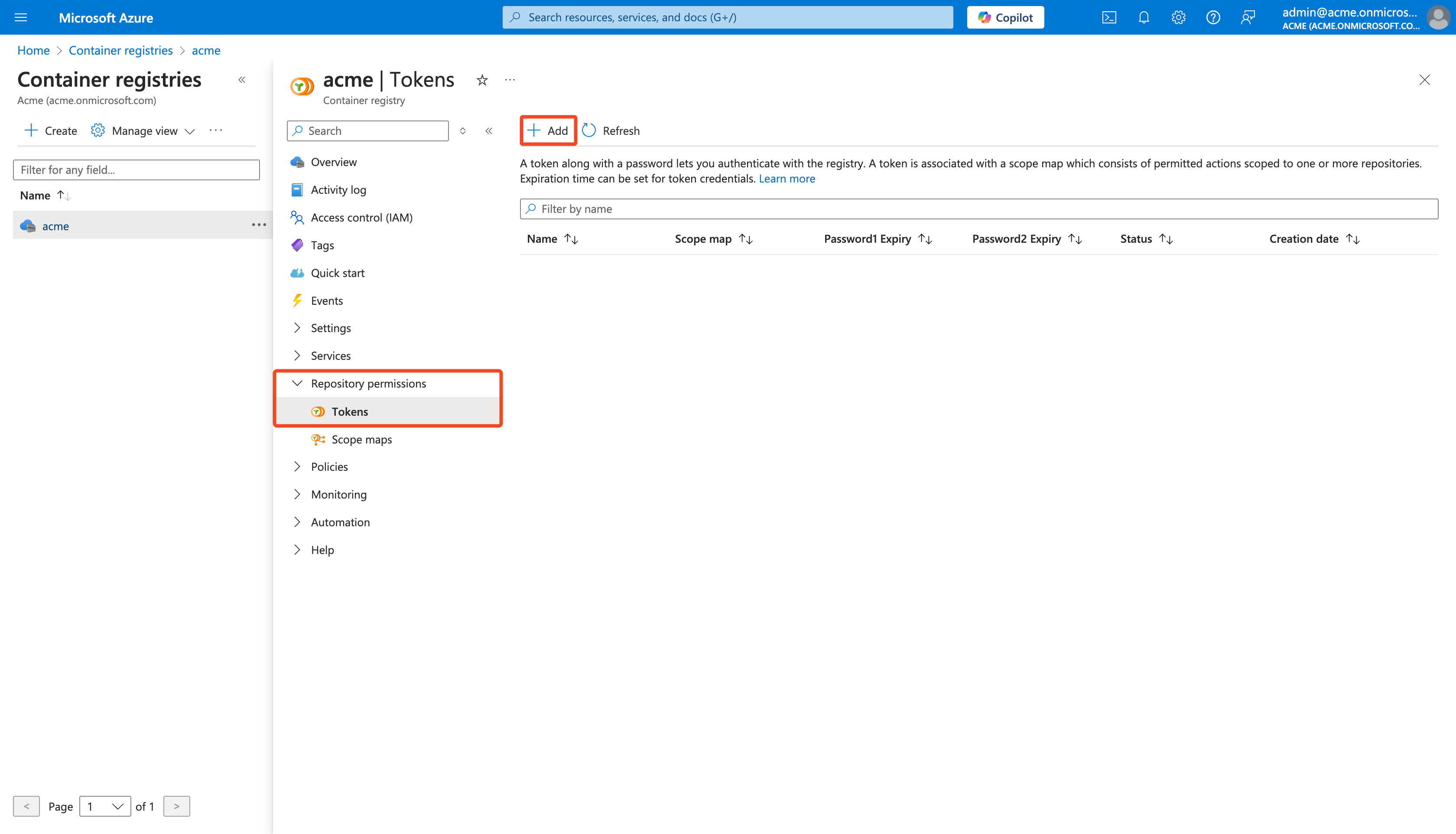
-
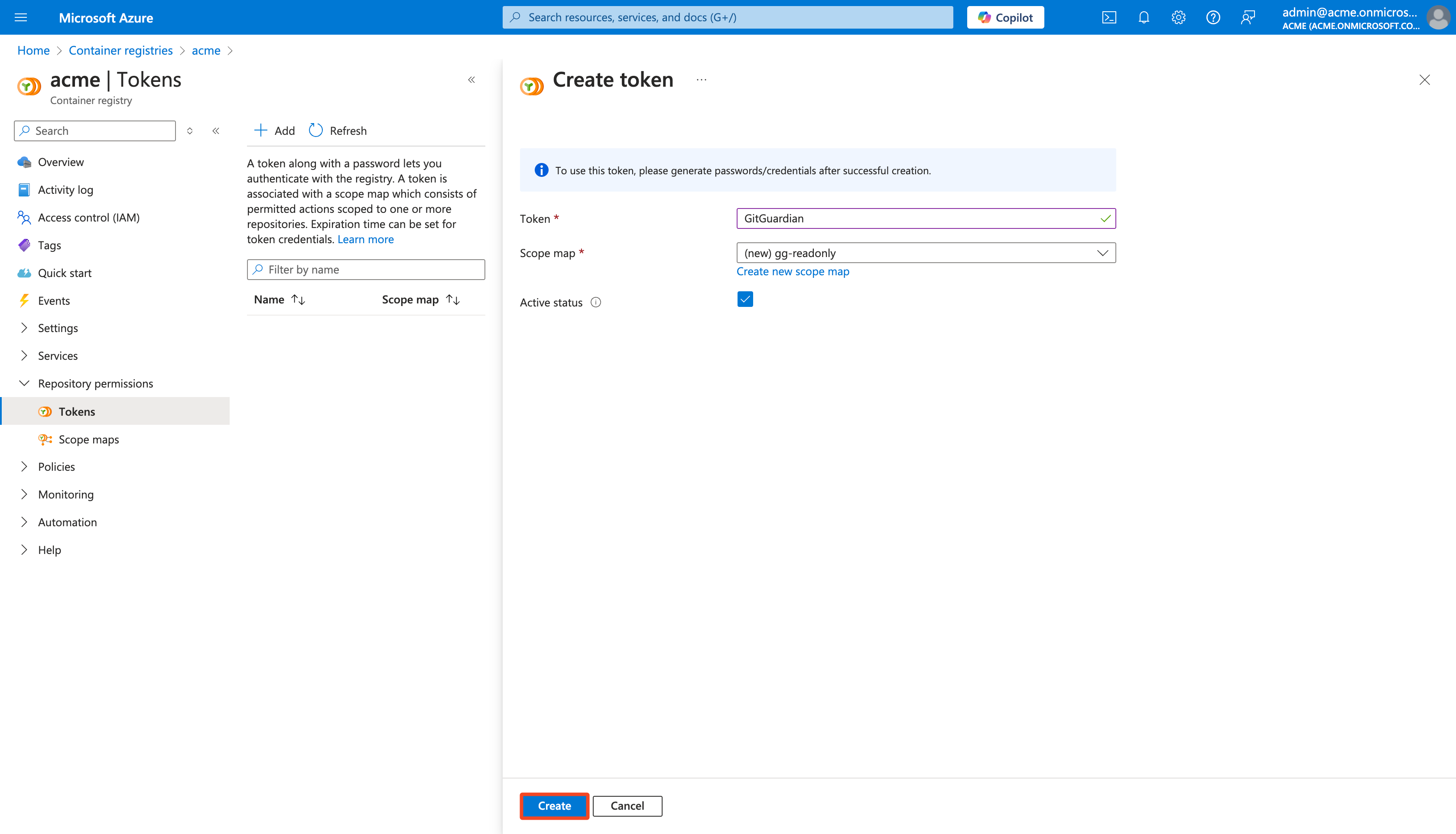
Provide a Token name:
GitGuardian -
Click Create new scope map
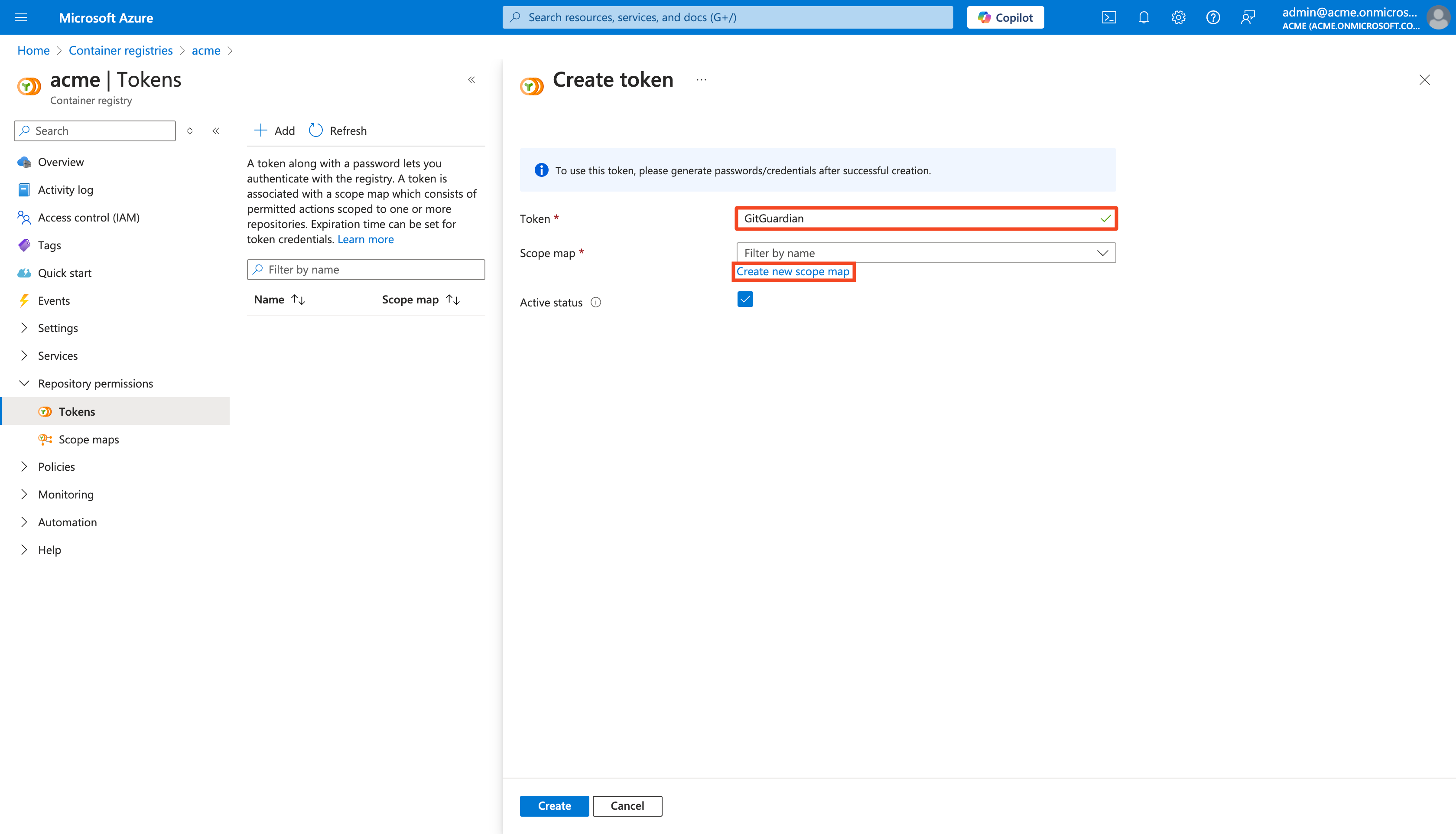
-
Name the Scope map (e.g.:
gg-readonly) -
Type
*in Repository to select them all -
Select
content/readandmetadata/readas Permissions -
Click Create to create the new scope map
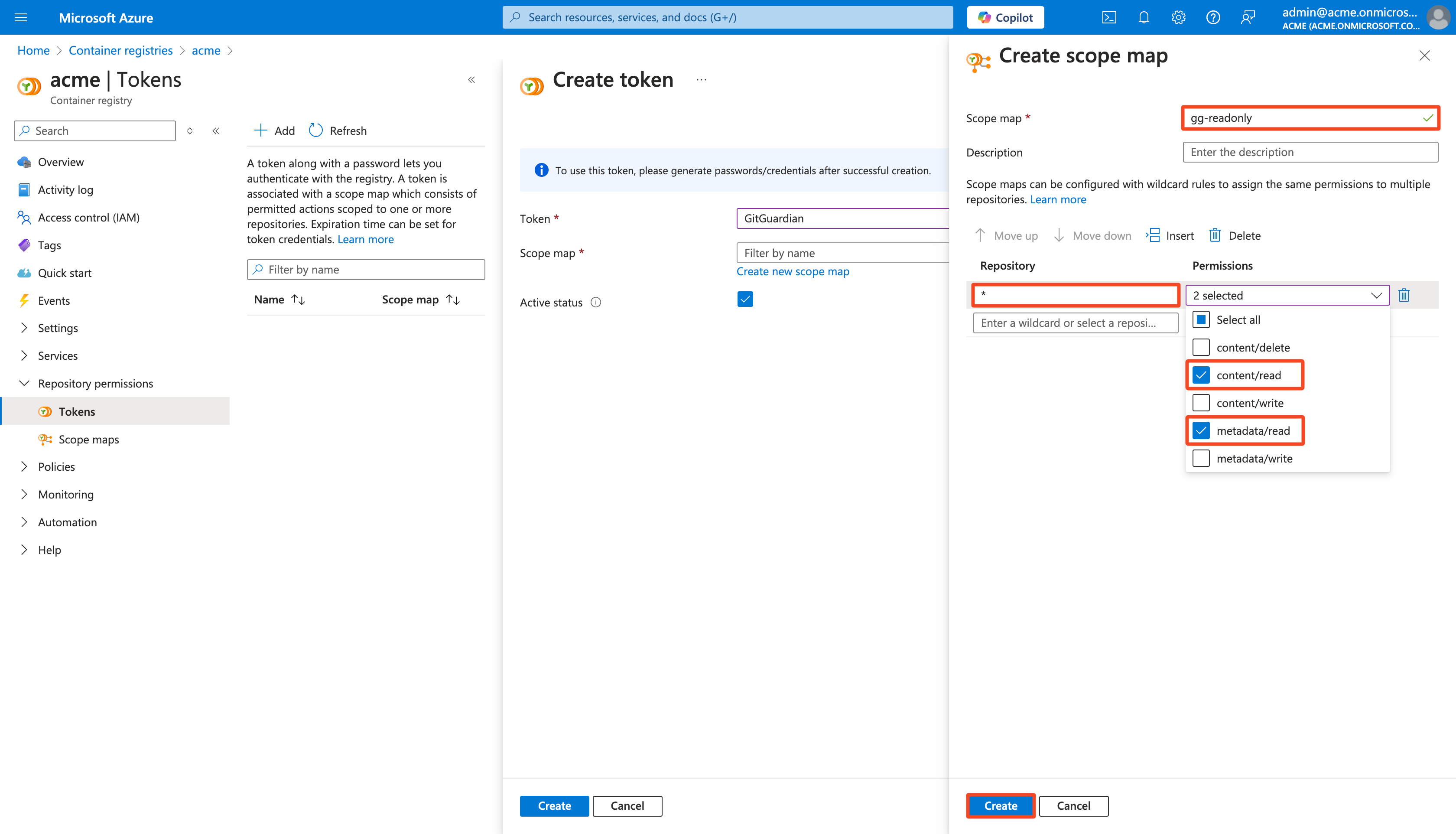
-
Click Create to create the new token
-
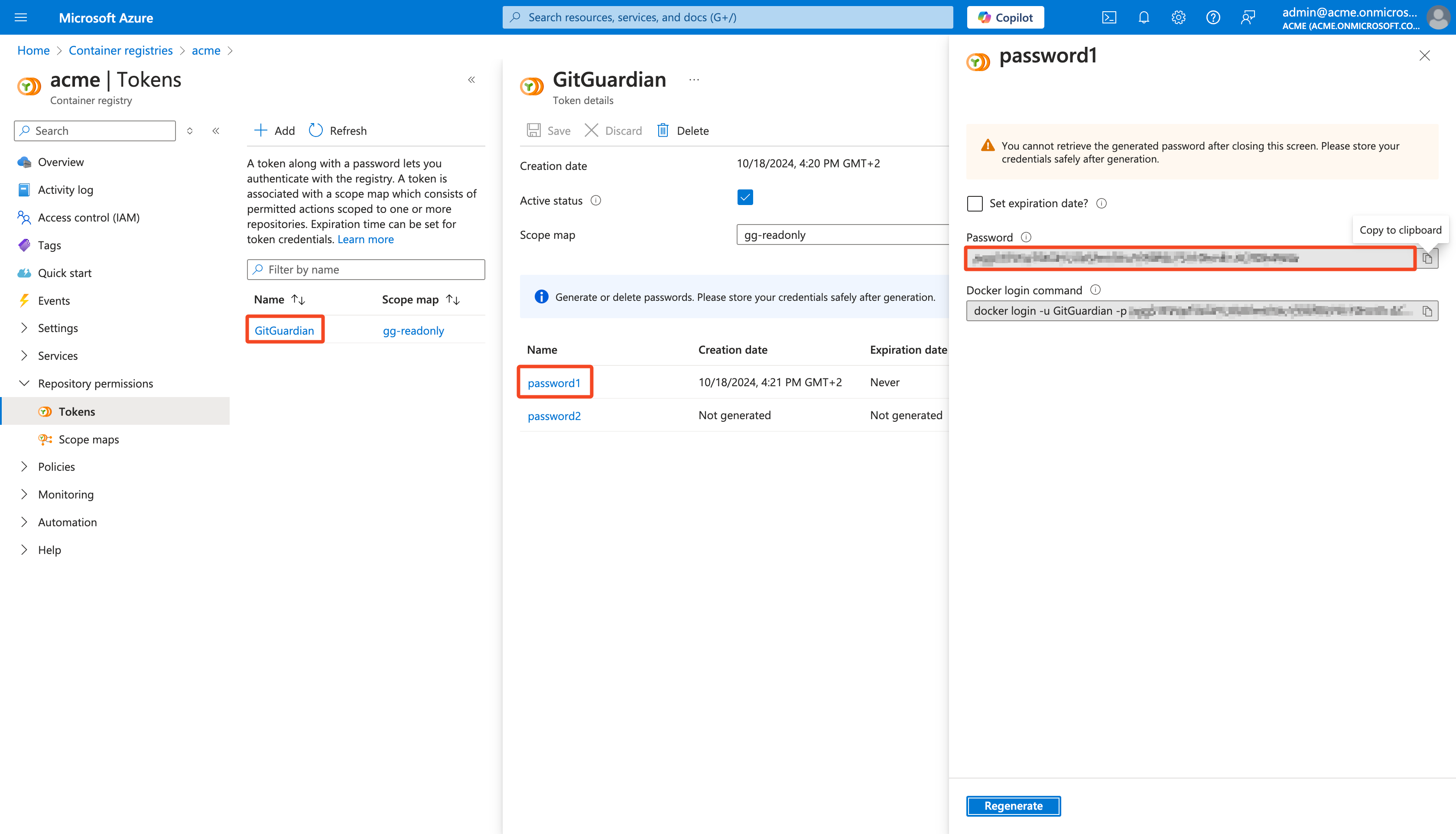
Select newly created Token
-
Click password1 (You have 2 passwords by default)
-
Click Generate to generate a new password
-
Copy the Password
-
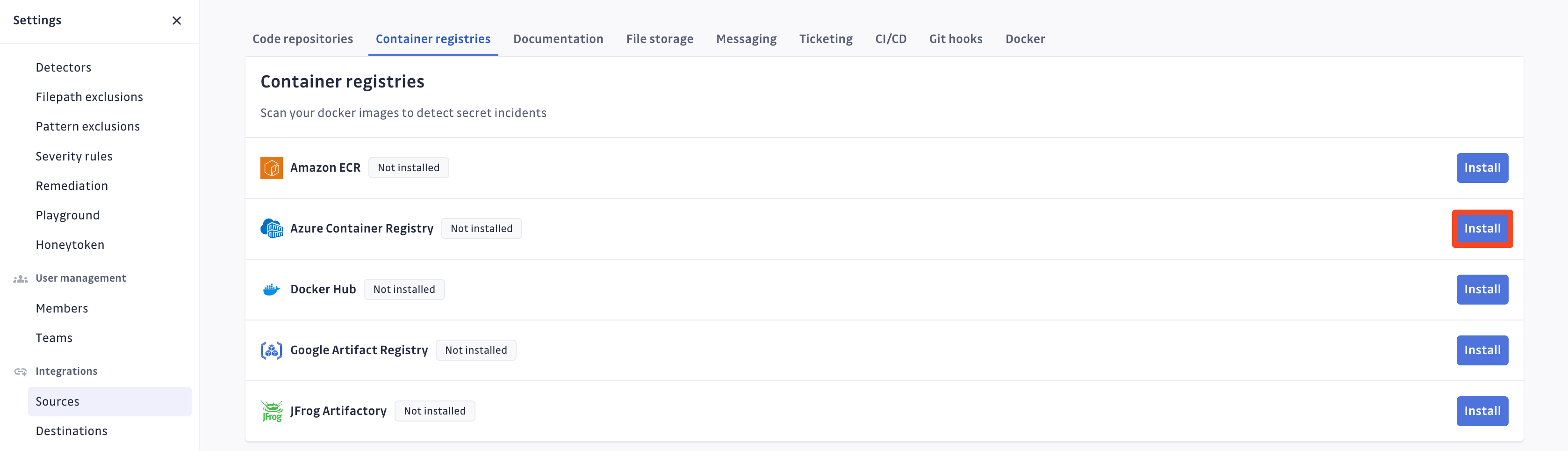
In the GitGuardian platform, navigate to the Sources integration page
-
Click Install next to Azure Container Registry in the Container registries section
-
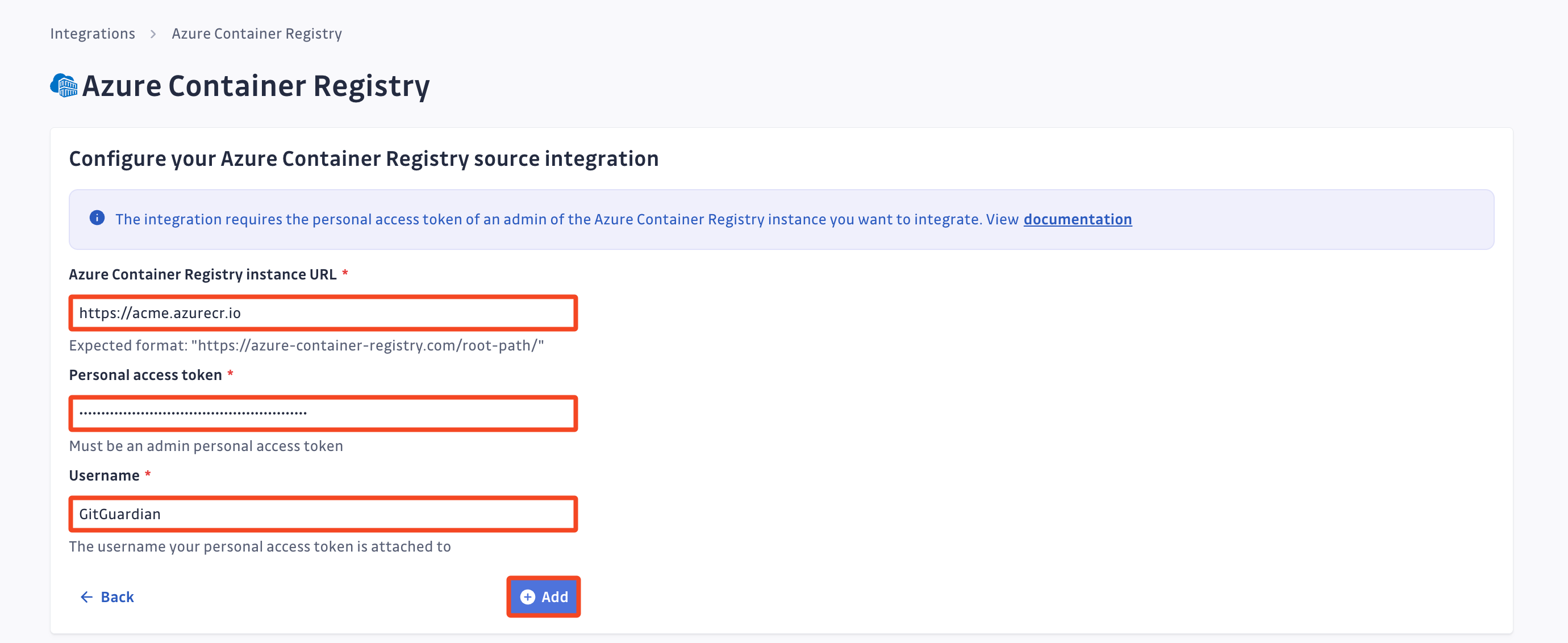
Click Install on the Azure Container Registry integration page
-
Paste your Login server (4) in the Azure Container Registry instance URL field (Complete with
https://at the beginning of the URL if missing) -
Paste your Password (13) in the Personal Access Token field
-
Paste your Token name (7) in the Username field
-
Click Add
-
Customize your monitored perimeter:
- Monitor specific Azure Container Registry repositories (Recommended)
- No repositories are monitored by default, you will have to select them manually.
- Newly created repositories will not be monitored by default. You can adjust this setting at any time.
- Recommended to optimize your bandwidth costs.
- Monitor the entire Azure Container Registry instance
- All repositories are monitored by default with a full historical scan automatically triggered.
- Newly created repositories will be monitored by default. You can adjust this setting at any time.
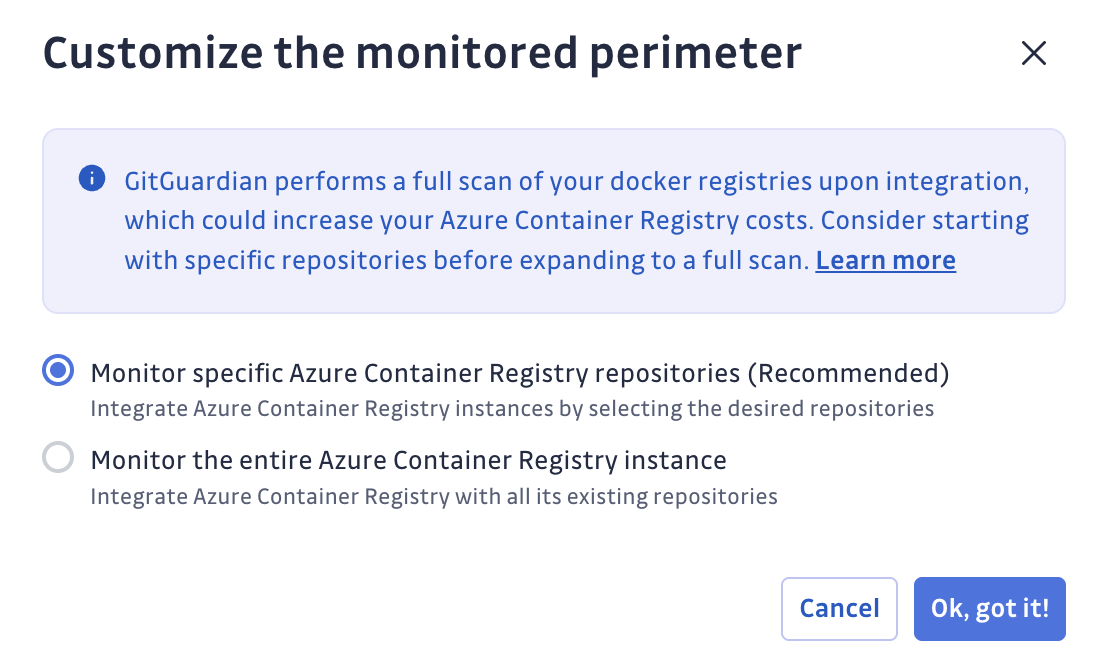
- Monitor specific Azure Container Registry repositories (Recommended)
That's it! Your Azure Container Registry instance is now installed, and GitGuardian is monitoring all Docker images of your selected repositories for secrets.
Customize your monitored perimeter
To customize the monitored repositories, navigate to your Azure Container Registry settings.
- Select/Unselect repositories to include or exclude them from monitoring
- Confirm by clicking Update monitored perimeter
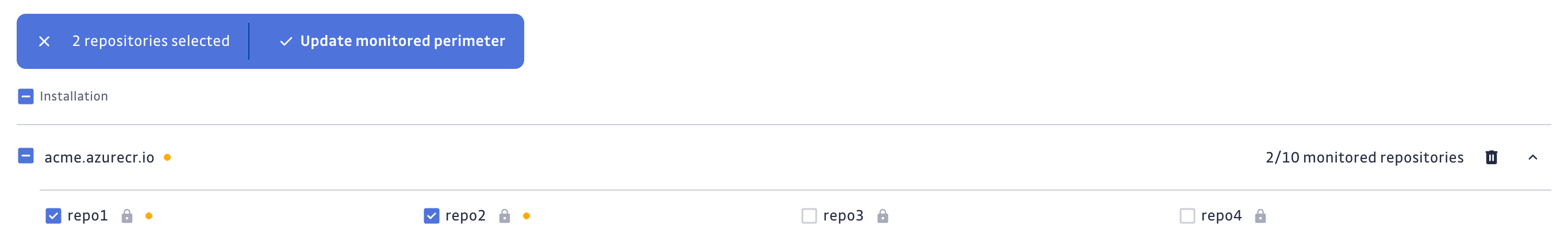
Automatic repository monitoring
You can enable or disable the automatic addition of newly created repositories to your monitored perimeter by switching the option in your Azure Container Registry settings.

Uninstall your Azure Container Registry instance
To uninstall an Azure Container Registry instance:
- In the GitGuardian platform, navigate to the Sources integration page
- Click Edit next to Azure Container Registry in the Container registries section
- Click the bin icon next to the Azure Container Registry instance to uninstall
- Confirm by clicking Yes, uninstall in the confirmation modal
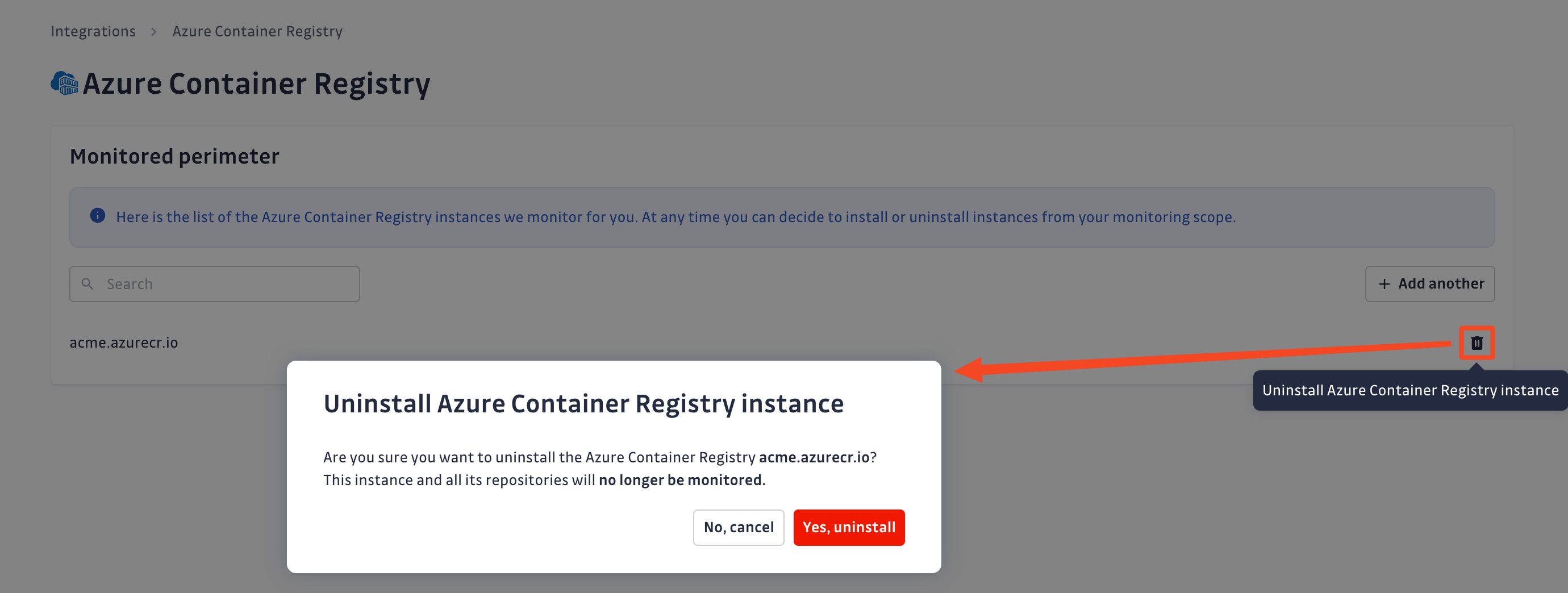
That's it! Your Azure Container Registry instance is now uninstalled.
Excluded paths
GitGuardian automatically excludes files from scanning if their paths contain any of these regular expressions:
/__pypackages__/
/\.venv/
/\.tox/
/site-packages/
/venv/
distutils/command/register.py
python.*/awscli/examples/
python.*/dulwich/(tests|contrib/test_)
python.*/hgext/bugzilla.py
python.*/mercurial/util.py
python.*/test/certdata/
python.*/urllib/request\.py
python.*/pygments/lexers/
/cryptography.+/tests/.+(fixtures|test)_.+.py
/python.+pygpgme.+/tests/
botocore/data/.+/(examples|service)-.+.json
usr(/local)?/lib/python.+/dist-packages
/libevent.+/info/test/test/
/conda-.+-py.+/info/test/tests.+/test_.+\.py
/python[^/]+/test/
/man/man5/kdc\.conf\.5
erlang.*(inets|ssl).*/examples/
/gems/.*httpclient.*/(test|sample)/
/gems/.*faraday.*/
/vendor/bundle/
/\.gem/
/(g|G)o/src/cmd/go/internal/.*_test.go
/(g|G)o/src/cmd/go/internal/.*/testdata/
/(g|G)o/src/cmd/go/testdata/
/(g|G)o/src/crypto/x509/platform_root_key.pem
/(G|g)o/src/crypto/tls/.*_test.go
/(g|G)o/src/net/(url|http)/.*_test.go
src/github.com/DataDog/datadog-agent/.*test.*.go
google/internal/.*_test.go
golang.org.*oauth2@.*/.*.go
/flutter/.*/packages/flutter_tools/test/data/
/flutter/.*/examples/image_list/lib
/\.pub-cache
etc/ssl/private/ssl-cert-snakeoil\.key
perl.*Cwd.pm
ansible/.*/tests/(integration|unit)/
ansible/.*/test/awx
ansible/collections/ansible_collections/.*/plugins/
/curl/.*/(tests|docs|lib/url.c)
/doc/wget.+/NEWS
dist/awscli/examples/
usr(/local)?/lib/aws-cli/examples/
/google-cloud-sdk/(lib|platform)/
\.git/modules/third[-_]?party/
\.git/modules/external/
/\.npm/_cacache
/node_modules/
/\.parcel-cache/
/\.yarn/cache/
/\.m2/
/\.ivy2/cache/
/\.mix/
/\.hex/
/composer/cache/
/\.nuget/packages/
/libgpg-error/errorref\.txt
/Homebrew/Library/Taps/
/tcl[^/]+/http-.+.tm
Limitations
This integration is currently in beta and has the following limitations:
- Scan Frequency: Scans occur once a day. It may take several hours to detect newly leaked secrets.
For GitGuardian Self-Hosted instances, scan frequency can be configured in the Admin Area.- Time interval unit: seconds
- Default value: 86400 (1 day)
- Minimum value: 1800 (30 minutes)
- Team Perimeter: Customization of a team perimeter with Azure Container Registry repositories is not supported. Users must be in All-incidents team to view and access Azure Container Registry incidents.
- Source Visibility: The visibility of repositories is not determined. All repositories are considered
privatein both the UI and API. - Presence Check: The presence check feature is not supported. All occurrences are considered
presentin both the UI and API. - Occurrence Previews: Previews of occurrences are not supported.
Privacy
Country-specific laws and regulations may require you to inform your users that your repositories are being scanned for secrets. Here is a suggestion for a message you may want to use:
As part of our internal information security process, the company scans its repositories for potential secrets leaks using GitGuardian. All data collected will be processed for the purpose of detecting potential leaks. To find out more about how we manage your personal data and to exercise your rights, please refer to our employee/partner privacy notice. Please note that only repositories relating to the company’s activity and business may be monitored and that users shall refrain from sharing personal or sensitive data not relevant to the repository’s purpose.

