Integrate your first repositories
To get started with Internal Monitoring for secrets, you need to add an integration with a source like a Version Control System (VCS).
If you want to try GitGuardian Internal Monitoring out on a test repository, go ahead and clone our sample_secrets repo. It contains 8 unique secrets our detection engine will find during the scans.
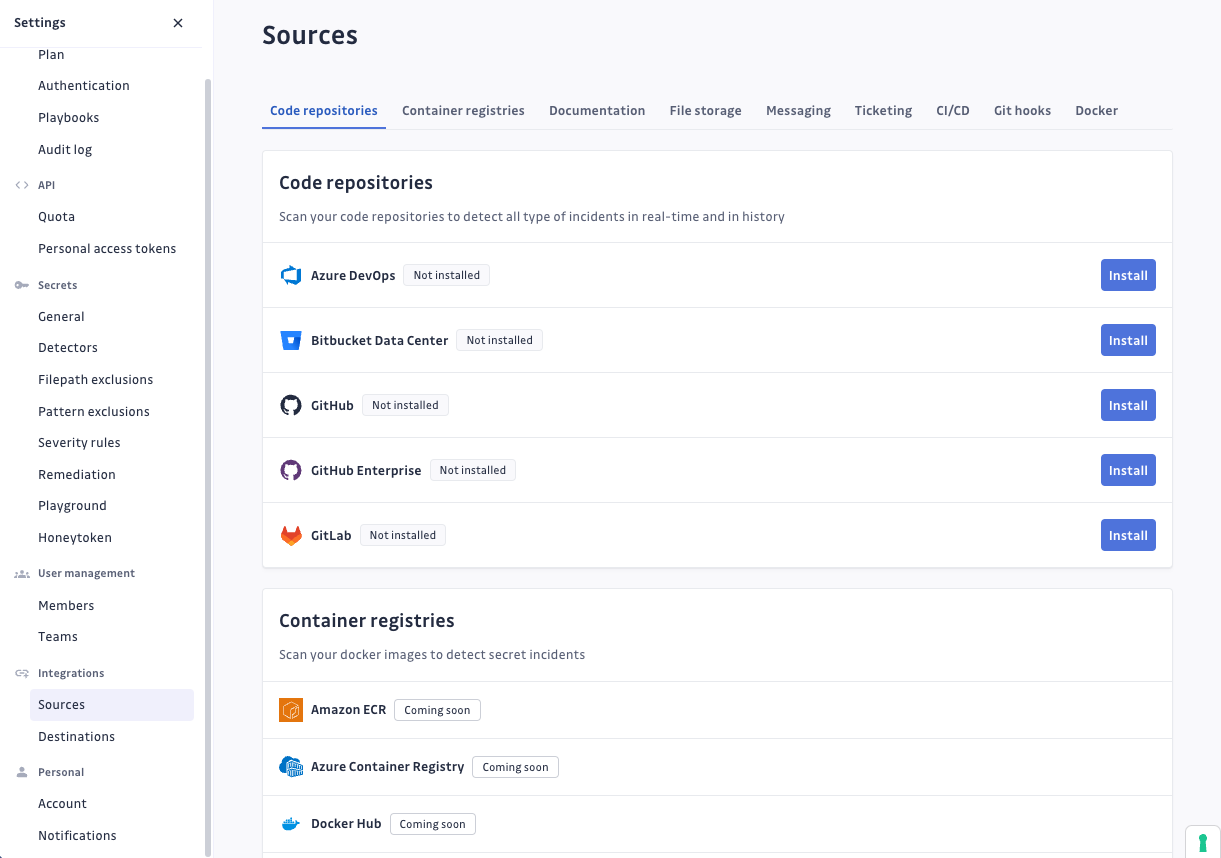
Integrate with GitHub
- From the VCS integrations page, select GitHub
- Confirm access to your GitHub account
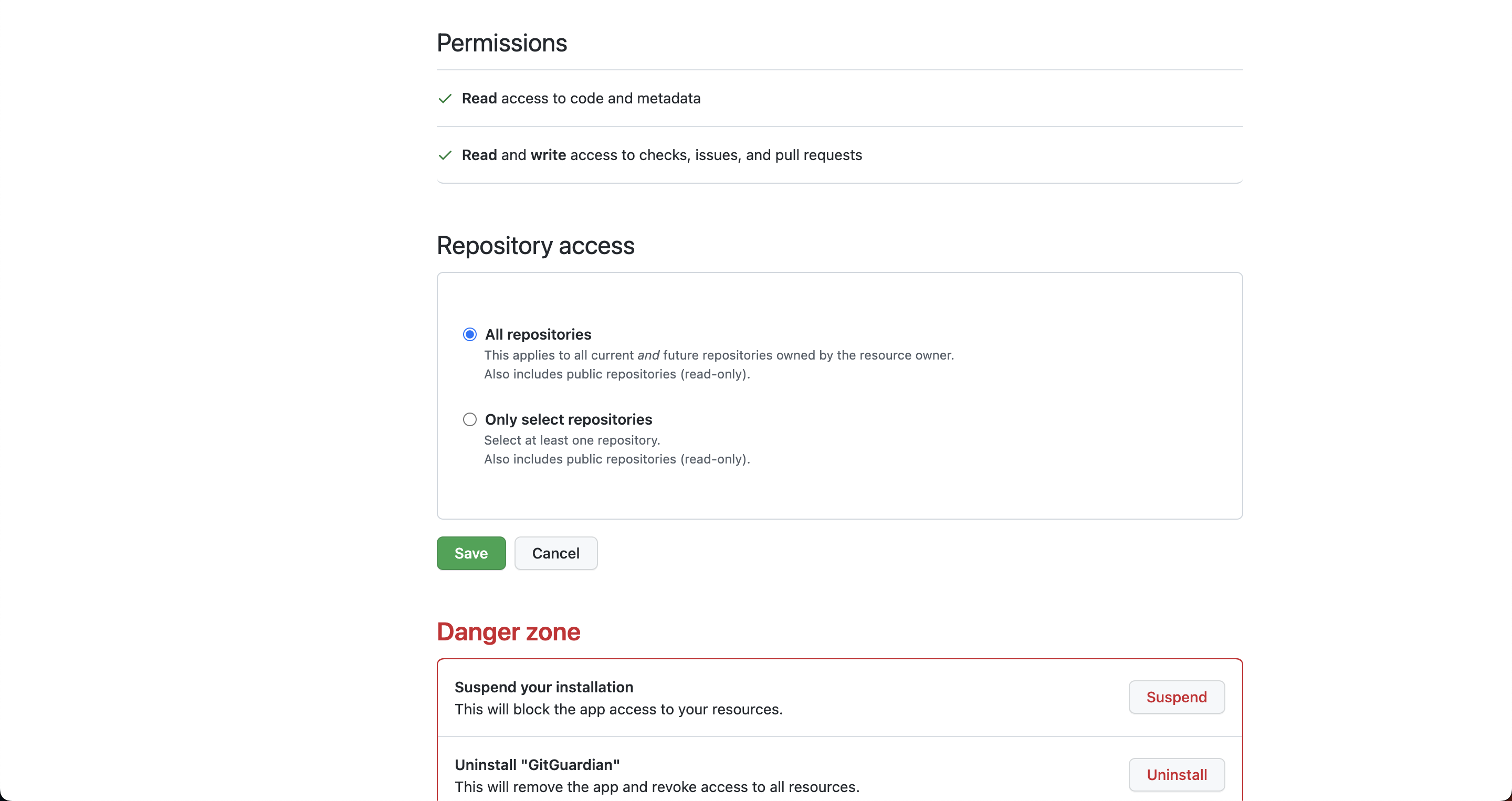
- Choose whether you want GitGuardian to monitor all your repositories or a selection of repositories. This can be changed later from your GitHub account.
- Go back to your GitGuardian dashboard to see your added user or organization and its repositories.
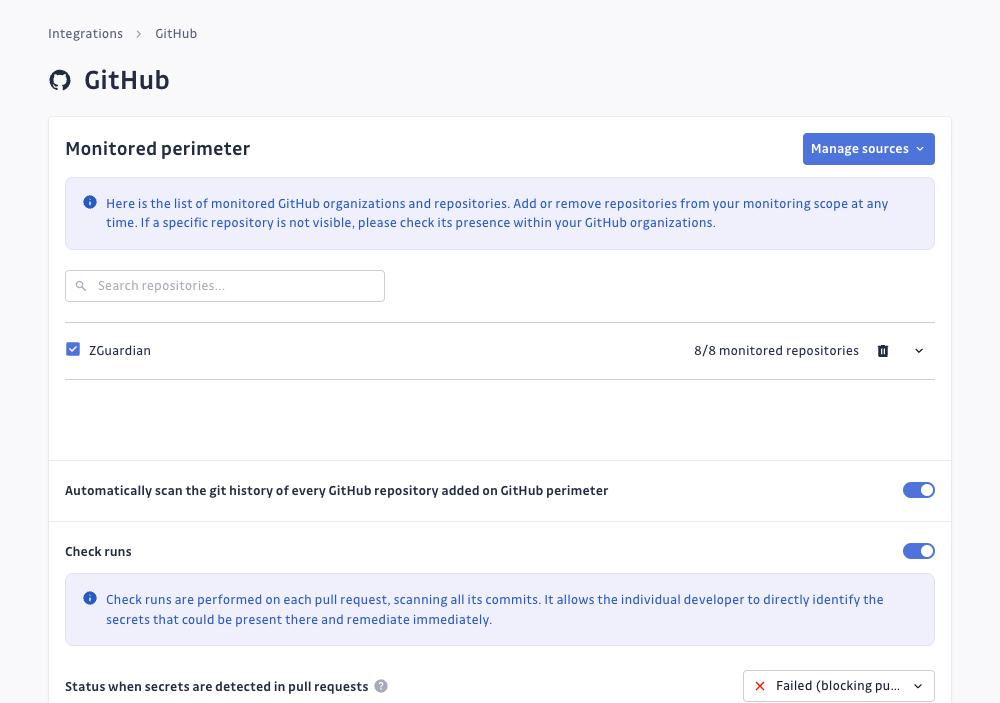
Once installed, GitGuardian will also give you the option to add or remove repositories from the monitored perimeter directly from your workspace.
Integrate with other VCS platforms
Integrate with GitLab
When integrating GitGuardian with GitLab, you can choose to monitor an entire instance or certain groups only. In both cases, you will need to generate a personal access token with admin permissions for the chosen perimeter.
Once installed, GitGuardian will also give you the option to add or remove repositories from the monitored perimeter directly from your workspace.
Step 1. Create a personal access token
- Go to your User Settings on GitLab
- View the Access Tokens section
- Choose a name (for example “gitguardian-secrets-scanning”)
- IMPORTANT: Select the API scope
If you need to, visit the GitLab documentation for more details on how to create personal access tokens.
Step 2. Configure your GitLab integration via a system hook or a group hook
There are two ways to configure your GitLab integration, using system hooks or group hooks. Now that you have your personal access token ready, follow one of these guides depending on your preference:
Integrate with Bitbucket server/data center
This integration does not support projects and repositories hosted on Bitbucket Cloud (bitbucket.org). Check out our Bitbucket Pipelines integration to keep your Bitbucket Cloud workspace secure.
Step 1. Create a personal access token
- In your Bitbucket workspace, navigate to your Bitbucket user settings (typically on your upper right hand corner, under Manage Account)
- Go to the Personal access tokens section
- Create a personal access token with a simple name such as "GitGuardian" and Read permissions on projects and Admin permissions on repositories. Set the "Automatic Expiry" option to "No".
Step 2. Configure your Bitbucket integration via a system hook or a group hook
There are two ways to configure your Bitbucket integration, at the instance-level or at the project-level. Follow one of these guides depending on your preference:

