Ownership - Assign Accountability for Non-Human Identities
Release Date: February 11, 2026
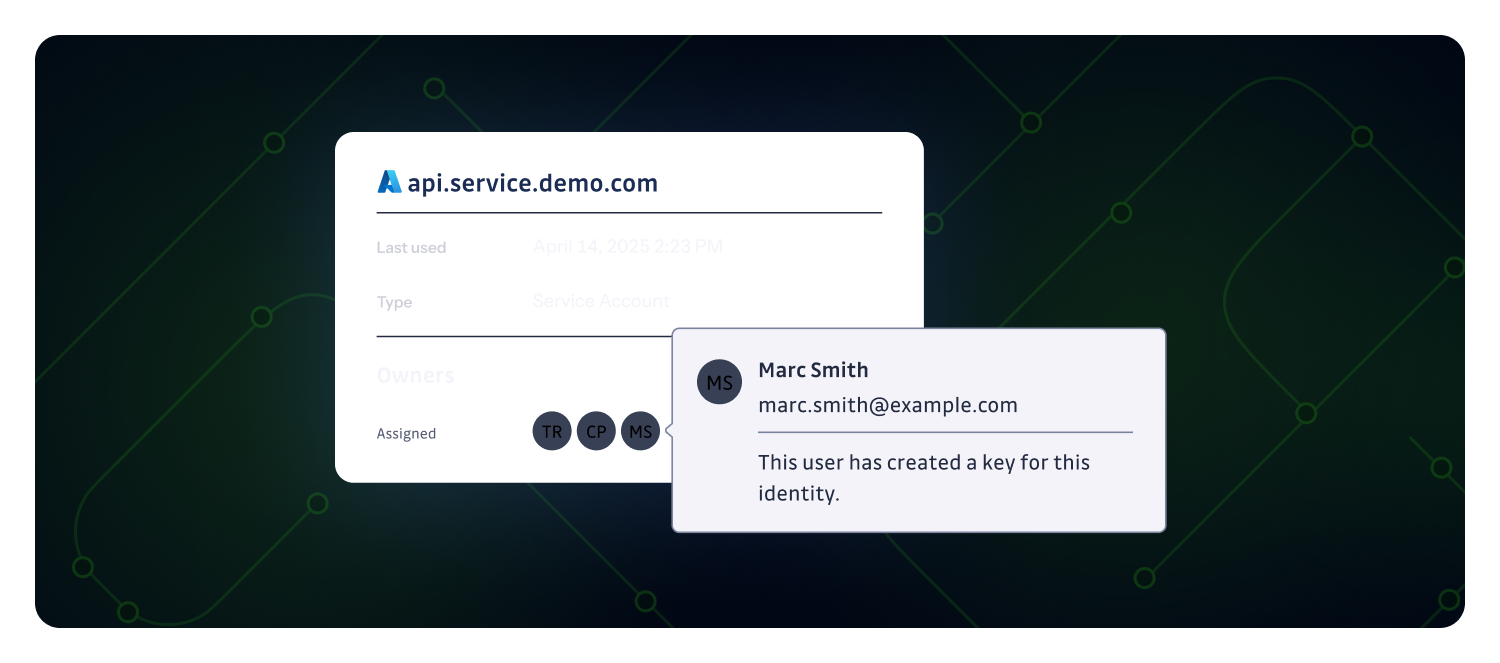
We're introducing Ownership in NHI Governance: you can now assign and track who is responsible for each Non-Human Identity across your inventory. Ownership helps close the accountability gap for machine identities, speed up remediation when secrets are exposed, and align with compliance expectations.
What does this mean for you?
- Suggested owners: GitGuardian automatically suggests owners using data from your integrated sources and from secret incidents.
- Manual control: Add, edit, or remove owners at any time from an NHI's detail view.
- Inventory at a glance: An Owner column in the NHI inventory shows who is responsible for each identity.
- Workspace members and external users: Owners can be workspace members or external users identified by email.
Why is it important?
NHIs outnumber human identities by orders of magnitude, yet accountability for machine identities is usually unclear. Without ownership, remediation slows down, orphaned accounts go unaddressed, and incident response suffers when secrets are exposed or misconfigured. Ownership gives you:
- Faster remediation – Know who to contact when an NHI is compromised or needs rotation.
- Fewer orphaned accounts – Assign responsibility so every identity has someone accountable.
- Stronger compliance – Meet audit and regulatory expectations (e.g. PCI-DSS, SOC 2, HIPAA) that require clear accountability for sensitive resources.
- Better triage – Filter and prioritize by owner (e.g. "identities with no owner" or "owned by my team") to focus efforts where they matter most.
Get started
Open NHI Governance → Identities to see the Owner column and filter. Open any NHI to view or edit owners in the Owners section. Learn more about Ownership
This feature is available to NHI Governance paying customers.
Enhancements
- Incidents: The risk score column is now included in CSV exports for both public and private incidents.
- ggshield: Secrets with multiple incidents (when using "By secret per source" grouping) are now correctly ignored in scans if a related incident exists and is closed, preventing CI pipelines from blocking unnecessarily.
Fixes
- Validity Checks: Secrets marked as invalid are now re-checked periodically, so their status can update to valid when they become usable again.
- Analytics: Commit date in hover tooltips now matches the actual timeline data.
- Developer in the Loop: Duplicate feedback submissions are now prevented by disabling the submit button after click and applying a cooldown period.
- SCIM: Email notifications for user and team sync operations (onboarding, offboarding, team membership changes) are now off by default. A new setting in the identity provider section lets you opt in to these notifications when desired.

