Install using Argo CD
Introduction
Using the GitGuardian Helm repository, you can easily install GitGuardian on your existing Kubernetes cluster with Argo CD.
Add GitGuardian Helm repository
First, you need to add the GitGuardian Helm repository to Argo CD using the following settings:
name: gitguardian
type: helm
enableOCI: 'true'
url: registry.replicated.com/gitguardian
username: <your.name@yourcompany.com>
password: <your.password>
The GitGuardian team will provide you the username and the password.
You can follow the official documentation and choose from the following methods:
Create the following Argo CD repository secret using kubectl:
You need to set the username and the password before.
cat <<EOF | kubectl apply -f -
apiVersion: v1
kind: Secret
metadata:
name: replicated-repo
namespace: argocd
labels:
argocd.argoproj.io/secret-type: repository
stringData:
name: replicated
type: helm
enableOCI: "true"
url: registry.replicated.com
username: <your.name@yourcompany.com>
password: <your.password>
EOF
You must first authenticate on your Argo CD server by using the command: argocd login <server_url>
Set your username/password and run this command:
argocd repo add registry.replicated.com \
--name replicated \
--type helm \
--enable-oci \
--username <your.name@yourcompany.com> \
--password <your.password>
Navigate to Settings/Repositories and add the GitGuardian Helm repository:
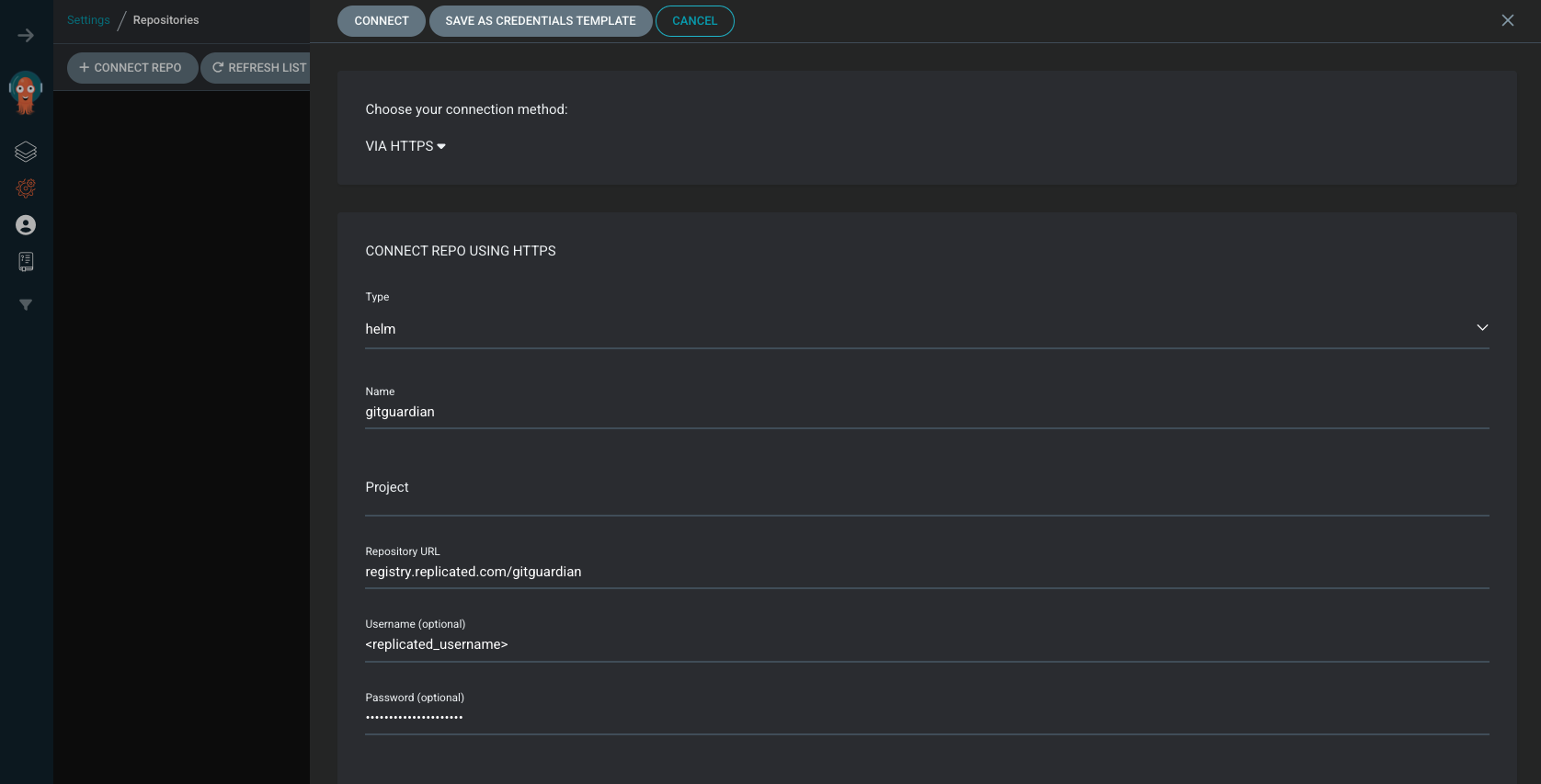
Ensure to enable OCI
Once added, you should see the GitGuardian Helm repository:
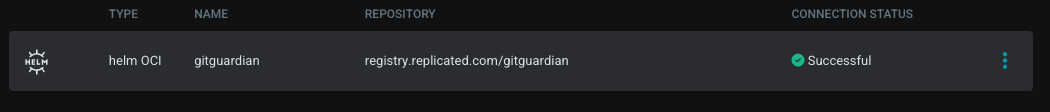
The connection status must be successful.
Configure GitGuardian Application
You can configure GitGuardian application by providing custom Helm values, follow the Helm instructions to proceed.
We highly recommend managing secrets on your own and referencing them via existingSecret Helm parameters (See Helm Secrets Management page). We also suggest visiting the Argo CD Secret Management page to efficiently manage your secrets.
Create encryption secret
When using Argo CD, you must pre-create the application encryption secret before deploying.
Generate a random key and create the secret:
- Linux / macOS
- Windows (PowerShell)
kubectl create secret generic gitguardian-encryption \
--namespace <namespace> \
--from-literal=django-secret-key="$(openssl rand -hex 32)"
$key = -join ((1..32) | ForEach-Object { '{0:x2}' -f (Get-Random -Maximum 256) })
kubectl create secret generic gitguardian-encryption `
--namespace <namespace> `
--from-literal=django-secret-key=$key
Then reference it in your values.yaml:
miscEncryption:
existingSecret: 'gitguardian-encryption'
existingSecretKeys:
djangoSecretKey: 'django-secret-key'
This secret is managed outside of Argo CD and will persist across syncs and upgrades.
Install GitGuardian Application
After creating the Helm value file values.yaml following above instructions, you can create the GitGuardian application using Argo CD CLI by running the following command:
argocd app create gitguardian \
--dest-server <cluster> \
--dest-namespace <namespace> \
--repo registry.replicated.com/gitguardian \
--helm-chart gitguardian \
--revision 2025.x.y \
--values-literal-file values.yaml \
--self-heal \
--auto-prune \
--sync-option PruneLast=true
If autoscaling is enabled, you must configure the Argo application to ignore changes made to the number of replicas for all deployments:
argocd app patch gitguardian \
--patch '{"spec": {"ignoreDifferences": [{"group": "apps", "kind": "Deployment", "jsonPointers": ["/spec/replicas"]}]}}' \
--type merge
If the MinIO bucket-init job appears with a Missing status in Argo CD, add the following annotations in your values.yaml to let Argo CD properly track the job:
loki-minio:
bucketInitJob:
annotations:
argocd.argoproj.io/hook: Sync
argocd.argoproj.io/hook-delete-policy: BeforeHookCreation
Upgrade GitGuardian Application
Prior to upgrading, ensure you back up your PostgreSQL database. For detailed instructions, refer to the Backup page.
To upgrade GitGuardian, you need first to update the Helm chart version using Argo CD CLI by running the following command:
argocd app patch gitguardian \
--patch '{"spec": { "source": { "targetRevision": "2024.x.y" } }}' \
--type merge
Sync the GitGuardian app:
argocd app sync gitguardian

