Install on an Embedded cluster (kURL)
Introduction
⚠️ Use the new Embedded Installation unless instructed otherwise.
GitGuardian can be installed with an embedded Kubernetes distribution packaged with it and supports deployment on bare metal, private, or public clouds.
This installation uses KOTS, a kubectl plugin and KOTS Admin Console to help manage Kubernetes Off-The-Shelf software.
Before starting the installation, ensure to review the system and network requirements, and download your license.
Installation
Embedded cluster
To start the installation, run the following command on your host as root. This command
will run for 10-20 minutes, putting in a screen or a tmux session can prevent
an interruption due to a loss of connection.
sudo -i
curl -sSL https://kurl.sh/gitguardian | bash
If prompted to select from multiple network interfaces, opt for the one connected to your private network.
This will install a single node-managed Kubernetes cluster with everything it needs to run the GitGuardian application.
Once the installation is completed, instructions will appear on how to access the KOTS Admin Console. Use provided IP address on port 8800.
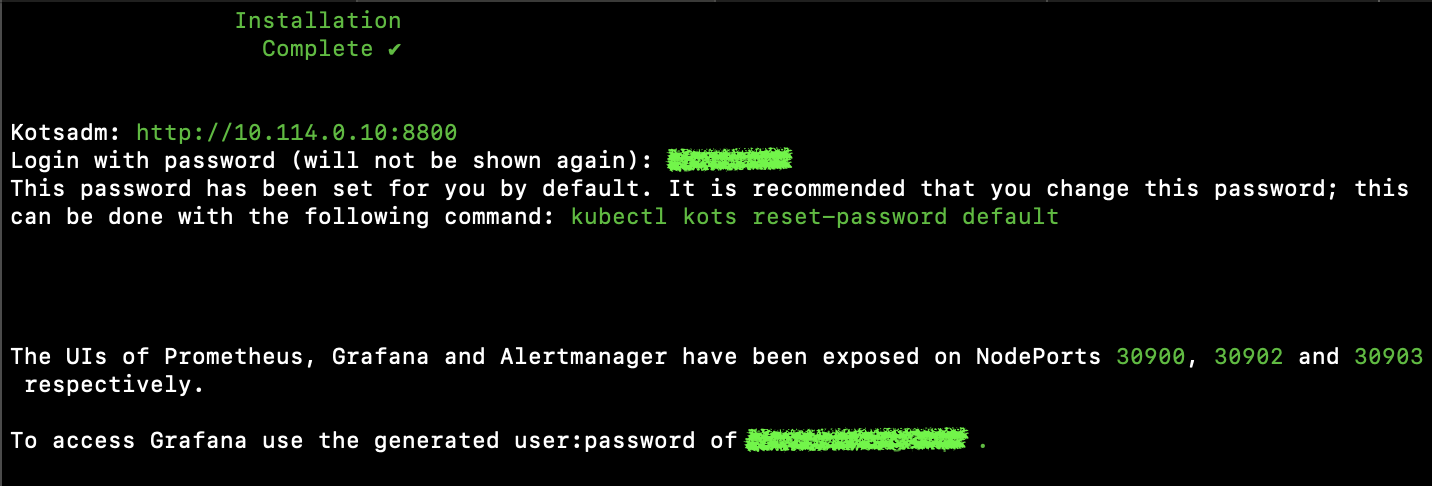
Save this information, especially passwords, they will be useful later.
Application
With the embedded Kubernetes cluster now set up, let's move on to installing the GitGuardian application.
- Access the KOTS Admin Console at
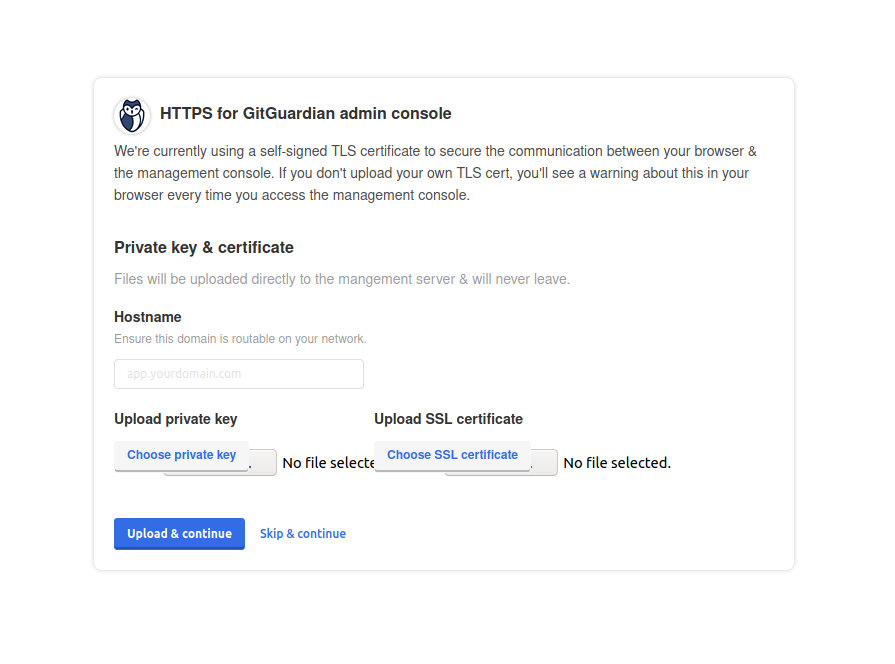
https://<ip_address>:8800and configure TLS. You have the option to upload your TLS certificates or use self-signed ones.
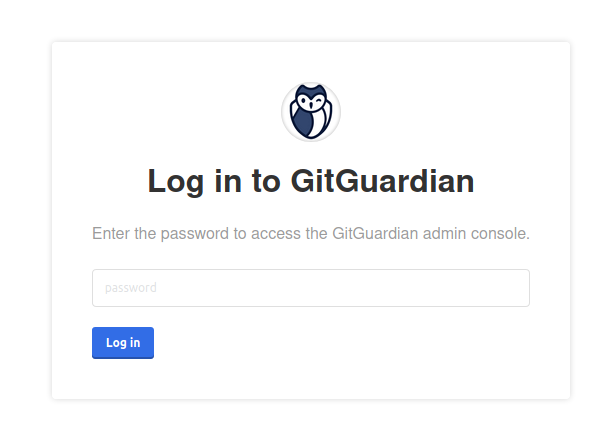
- Enter the password provided at the end of the cluster installation.
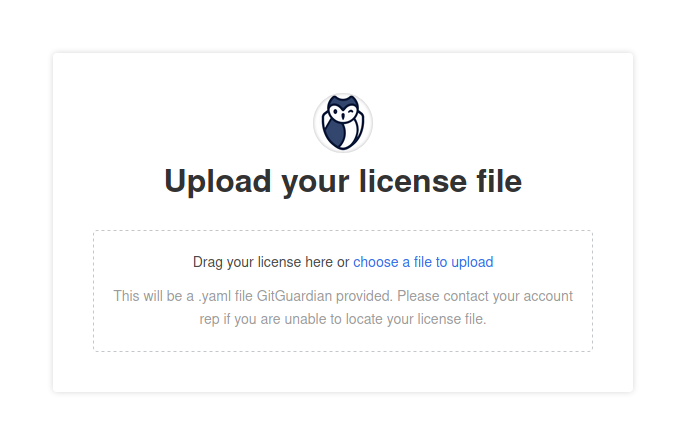
- Upload the license downloaded on the portal. Refer to the download your license page.
-
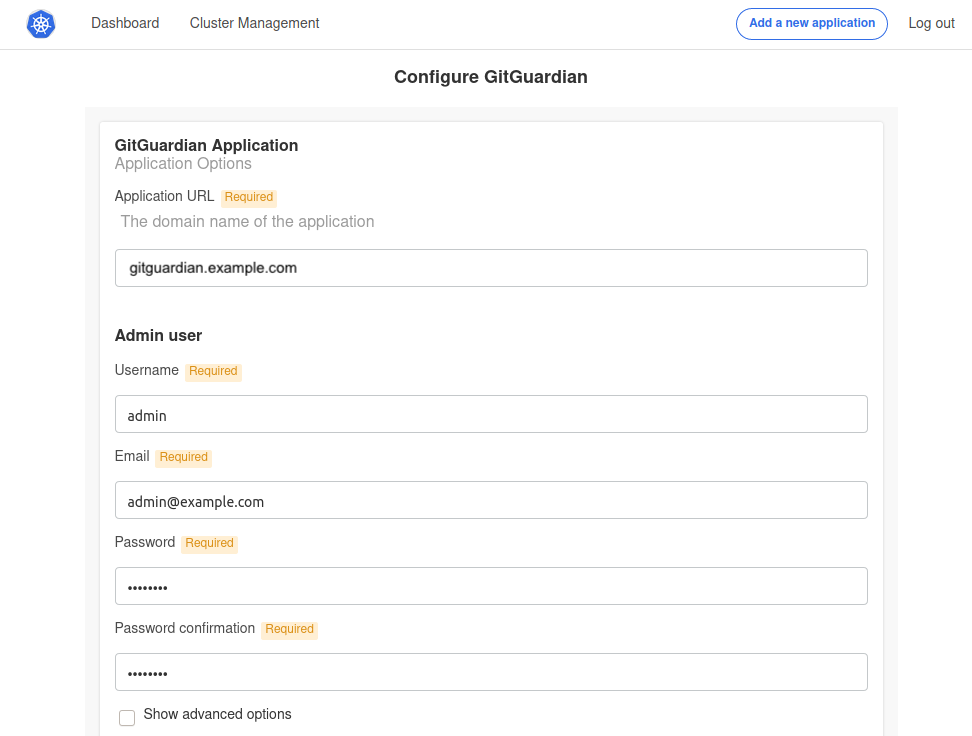
Configure the application by completing all the required fields:
- Application Hostname: Enter the Fully Qualified Domain Name (FQDN) for the GitGuardian application.
- Admin User Fields: These fields are used to create the first GitGuardian user. You'll need to change the password upon the first login.
Additional configuration options include:
- Scaling: Adjust the number of replicas for each application component. For more details, visit the Scaling page.
- Prometheus: Activate an exporter for Prometheus.
- TLS Certificate: This is for the GitGuardian Application. You can either use auto-generated self-signed certificates or upload your own. For self-signed or private CA certificates, disable SSL verification for the GitHub webhook. Learn more on the Configure TLS certificates page.
- Custom Certificate Authority: Provide a custom CA if necessary.
- HTTP(s) Proxy: Refer to the proxy section if needed.
- Databases/Datastores: Choose between using embedded PostgreSQL/Redis or an external one. For more information, see Configure your database.
- Load balancer considerations: To use the embedded cluster behind a load balancer, please read Configure your instance to work behind a load balancer.
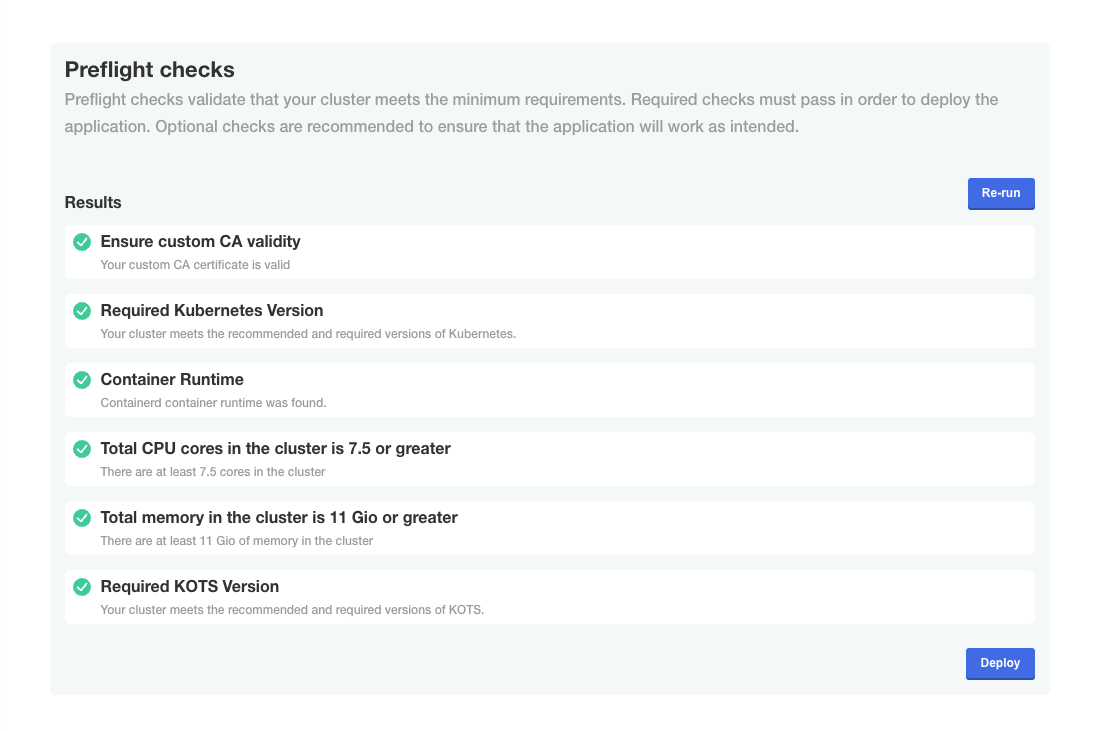
- Check if preflight checks pass.
Preflight checks are critical for a successful installation. The following rules apply:
- ❌ Preflight Check Failures: If preflight checks fail, the installation must not continue until the targeted environment meets all requirements. Please reach out to our support team if needed.
- ⚠️ Preflight Check Warnings: If preflight checks return warnings, the installation can proceed, but it is recommended that you address these warnings to comply with our recommendations.
- Launch
The first installation of the GitGuardian application requires a few minutes to create all database objects. Once the process is completed, you will be able to log in to the dashboard using the administrator user you defined.
Save the Data Encryption Key
GitGuardian encrypts all sensitive information in the database using an encryption key (aka Django Secret Key). In case of disaster recovery, this key will be needed to restore your data.
You should save it and keep it in a secure location. Use the following command to display the key:
kubectl get secrets gim-secrets -o jsonpath='{.data.DJANGO_SECRET_KEY}' | base64 -d
If needed, specify the Kubernetes namespace with --namespace (default namespace is used if not specified).
Network and storage configuration
Configuring proxy settings
If a proxy is required for outgoing access to the internet, please create a
patch.yaml:
apiVersion: 'cluster.kurl.sh/v1beta1'
kind: 'Installer'
metadata:
name: 'patch'
spec:
kurl:
proxyAddress: http://<IP>:<PORT>
noProxy: false
And run the installer with -installer-spec-file=patch.yaml as root:
sudo -i
curl -sSL https://kurl.sh/gitguardian | bash -s installer-spec-file=patch.yaml
Managing disk space
The kURL Embedded cluster will create a MinIO Persistent
Volume mounted on /mnt/data. You can use a specific disk for this volume and,
in this case, it must have at least 200GB of free space.
The kURL installer will look for the existence of the /var directory as well
as all the core directories mentioned in its documentation.
Otherwise, the root storage should not be partitioned. You can read more about the disk space requirements in the kURL documentation.
Note that if your disk is not a SCSI device, you will need to patch the install script following these guidelines:
- Create a YAML file and add the following parameters (this is an example for a
nvmedevice):
kind: Installer
metadata:
name: patch
spec:
rook:
blockDeviceFilter: nvme1n[0-1]
- Run the install script with that patch as root:
sudo -i
curl -sSL https://kurl.sh/gitguardian | bash -s installer-spec-file=[path of the above YAML patch file]
Troubleshooting
If you encounter issues during the installation process, you can generate a support bundle for the GitGuardian team to diagnose and resolve problems more efficiently. See the support bundle documentation for detailed instructions.

