Support bundle
We are here to assist you and welcome your feedback on our features. Feel free to reach out at support@gitguardian.com. Additionally, you can submit any ideas or feature requests directly on our Product Portal.
Generate a support bundle
Helm-based installation
For Helm-based installations, the KOTS Admin Console isn't available. Instead, you'll need to use a client-side utility, packaged as a kubectl plugin and distributed via the Krew package manager.
To generate a support bundle:
- Install the Krew plugin.
- Install the support-bundle utility:
kubectl krew install support-bundle. - Run:
kubectl support-bundle --load-cluster-specs --namespace <namespace>.
This command will create a .tar.gz support bundle in your current directory. You can then send it to GitGuardian support.
To customize the number of log lines captured, set the maxLines parameter as shown below. Adjust the value to capture more or fewer logs as needed:
replicated:
supportBundle:
logs:
maxLines: 100000 # Maximum number of log lines
For generating a support bundle using Helm, the following YAML configuration provides minimal Role-Based Access Control (RBAC) settings. Cluster admins must apply these RBAC rules where GitGuardian is deployed.
If you are not a cluster-admin in your Kubernetes cluster, you will need to apply the configuration below in your targeted namespace <gitguardian_namespace>:
# Below role is mandatory
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: support-bundle
namespace: <gitguardian_namespace>
rules:
- apiGroups: ['*']
resources: ['*']
verbs: ['get', 'list', 'watch']
- apiGroups: ['']
resources: ['pods/exec']
verbs: ['create']
# This role is optional and is used to retrieve cluster-scoped information, which can be useful for troubleshooting
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: support-bundle
rules:
- apiGroups: ['']
resources: ['namespaces', 'nodes']
verbs: ['get', 'list', 'watch']
- apiGroups: ['apiextensions.k8s.io']
resources: ['customresourcedefinitions']
verbs: ['get', 'list', 'watch']
- apiGroups: ['storage.k8s.io']
resources: ['storageclasses']
verbs: ['get', 'list', 'watch']
KOTS-based installation
If you previously installed GitGuardian on an existing cluster using KOTS and either lack cluster-admin rights in your Kubernetes cluster or wish to limit permissions for the KOTS Admin Console, you must apply the configuration in your targeted namespace as described in Kubernetes Application RBAC.
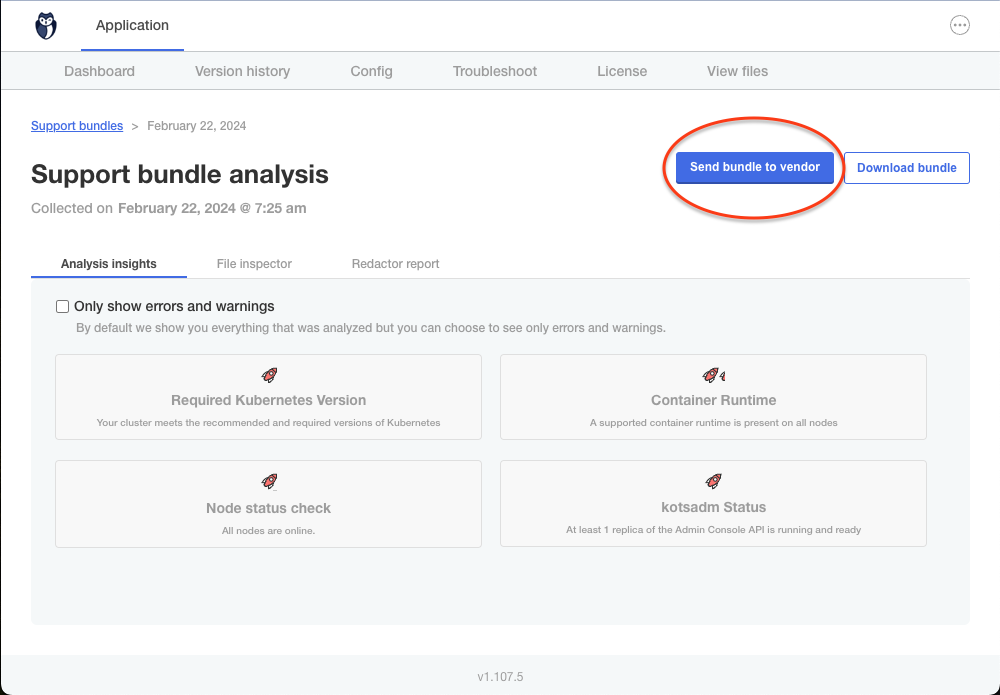
The KOTS Admin Console includes a diagnosis tool for generating a support bundle to identify common issues. Sensitive information is automatically redacted. You can also get a command to manually generate a support bundle from a CLI.

Once generated, you can preview the contents and send it directly to GitGuardian for analysis.
To customize the number of log lines captured in the support bundle, go in the KOTS Admin Console and set the Maximum number of lines in logs field in the Support Bundle section of the configuration section.
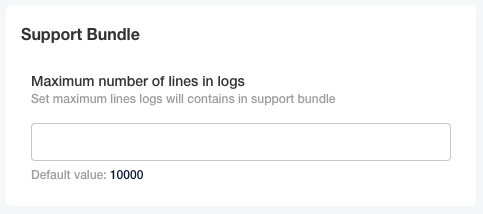
Then save the configuration, and Deploy the application to apply the new configuration.
Generate a support bundle when the Kubernetes cluster is down
When debugging an offline Kubernetes cluster, you can utilize host collectors to generate a support bundle even without access to the Admin Console.
To begin, install the support bundle tool on a host with access to the cluster you need to debug:
curl -L https://github.com/replicatedhq/troubleshoot/releases/latest/download/support-bundle_linux_amd64.tar.gz | tar xzvf -
Next, generate the support bundle using the following command:
./support-bundle --interactive=false https://raw.githubusercontent.com/replicatedhq/troubleshoot-specs/main/host/default.yaml
If your current user lacks the necessary access to gather information for a specific collector, you may need to run the above command with sudo.
For air gap environments, download the YAML file and copy it to the air gap machine.
For more details, refer to Replicated Documentation.

