Database Security (legacy)
You are now on a GitGuardian legacy architecture page.
Looking for the GitGuardian new architecture Database Security page? Please visit the Database Security page.
For information on the new architecture, as well as determining whether you are using the new or the legacy GitGuardian architecture, explore the New GitGuardian Architecture page.
Maintaining the security of your database systems is paramount in protecting sensitive information and ensuring the integrity of your data. This guide provides comprehensive steps for updating the security settings of PostgreSQL and Redis databases, including password changes, encryption key rotation, and client certificate updates. Follow these procedures carefully to enhance the security posture of your databases.
Update PostgreSQL Password
Ensure the security of your PostgreSQL database by setting a new password.
Ensure you back up your database before starting this procedure, which will incur minimal application downtime—from scaling down to full redeployment.
- Scale down the Dashboard, Public API and Webhook receivers.
kubectl scale deploy/gitguardian-app --replicas 0 --namespace <namespace>
If needed, specify the Kubernetes namespace with --namespace (default namespace is used if not specified).
- Confirm all asynchronous and scheduled tasks have finished.
kubectl --namespace <namespace> exec --tty deploy/gitguardian-worker \
-- celery -A ward_run_app inspect active
The output should indicate - empty - for each pod, signaling completion.
app@(...):/app$ celery -A ward_run_app inspect active
(...)
-> email@gitguardian-email-(...): OK
- empty -
-> scanner@gitguardian-scanner-(...): OK
- empty -
-> email@gitguardian-email-(...): OK
- empty -
-> workers@gitguardian-worker-(...): OK
- empty -
-> long_tasks@gitguardian-long-tasks-(...): OK
- empty -
-> workers@gitguardian-worker-(...): OK
- empty -
-> scanner@gitguardian-scanner-(...): OK
- empty -
-> long_tasks@gitguardian-long-tasks-(...): OK
- empty -
- Scale down all workers and scheduler pods.
kubectl scale deploy/gitguardian-beat --replicas 0 --namespace <namespace>
kubectl scale deploy/gitguardian-email --replicas 0 --namespace <namespace>
kubectl scale deploy/gitguardian-long-tasks --replicas 0 --namespace <namespace>
kubectl scale deploy/gitguardian-scanner --replicas 0 --namespace <namespace>
kubectl scale deploy/gitguardian-worker --replicas 0 --namespace <namespace>
If needed, specify the Kubernetes namespace with --namespace (default namespace is used if not specified).
- Configure your environment, update the namespace
gg_namespaceas needed.
gg_namespace=<namespace>
pg_host=$(kubectl -n $gg_namespace get secret gitguardian-env-variables -o jsonpath="{.data.POSTGRES_HOST}" | base64 -d)
pg_port=$(kubectl -n $gg_namespace get secret gitguardian-env-variables -o jsonpath="{.data.POSTGRES_PORT}" | base64 -d)
pg_user=$(kubectl -n $gg_namespace get secret gitguardian-env-variables -o jsonpath="{.data.POSTGRES_USER}" | base64 -d)
pg_passwd=$(kubectl -n $gg_namespace get secret gitguardian-env-variables -o jsonpath="{.data.POSTGRES_PASSWORD}" | base64 -d)
pg_db=$(kubectl -n $gg_namespace get secret gitguardian-env-variables -o jsonpath="{.data.POSTGRES_DB}" | base64 -d)
- With your environment set, you're ready to launch a PostgreSQL shell.
echo "Connection to $pg_user@$pg_host:$pg_port/$pg_db"
kubectl -n $gg_namespace run postgresql-client --rm -it \
--restart='Never' --image docker.io/bitnami/postgresql:13 \
--env="PGPASSWORD=$pg_passwd" --command \
-- psql --host $pg_host -U $pg_user -d $pg_db -p $pg_port
- Inside the shell, update your password.
ALTER USER <postgres user> WITH PASSWORD '<new password>';
Replace <postgres user> with your username and <new password> with the desired password.
-
Navigate to the “Config” tab in the KOTS Admin Console and update the PostgreSQL password. Save the configuration.
-
Deploy the updated configuration.
Update Redis main Password (external cluster)
The process for updating the Redis main password varies by installation method:
- Standard Redis Installation: either create a new instance with identical settings or directly update the password in the existing instance's configuration file.
- AWS Elasticache: use the AWS CLI or API to follow the Rotate AUTH token guidelines.
- GCP Memorystore: modify the AUTH string by toggling AUTH from off to on.
- Bitnami Helm chart: in the Redis Helm Chart value file, change the value
global.redis.passwordwith the new password.
- In the KOTS Admin Console's “Config” tab, update the Redis host and password.
- Save the configuration.
- Deploy the updated configuration.

Update Redis main Password (embedded cluster)
- Get the Redis configuration from the secret:
kubectl get secrets --namespace <namespace> redis-config-files -o 'go-template={{index .data "redis.conf"}}' | base64 -d > redis.conf
If needed, specify the Kubernetes namespace with --namespace (default namespace is used if not specified).
- Change the value of
requirepassby the new password and save the file.
(...)
################################## SECURITY ###################################
requirepass <new password>
################################### CLIENTS ####################################
(...)
- Update the existing secret with your changes.
REDISCONF=$(base64 < ./redis.conf)
kubectl patch secret --namespace <namespace> redis-config-files \
-p "{\"data\":{\"redis.conf\":\"${REDISCONF}\"}}"
Update PostgreSQL client certificate (external cluster)
This procedure is intended for PostgreSQL configurations using mTLS (Mutual TLS). Please be aware that configuring PostgreSQL to utilize client certificates is not feasible with AWS RDS.
Ensure you back up your database before starting this procedure, which will incur minimal application downtime—from scaling down to full redeployment.
- Scale down the Dashboard, Public API and Webhook receivers.
kubectl scale deploy/gitguardian-app --replicas 0 --namespace <namespace>
If needed, specify the Kubernetes namespace with --namespace (default namespace is used if not specified).
- Confirm all asynchronous and scheduled tasks have finished.
kubectl --namespace <namespace> exec --tty deploy/gitguardian-worker \
-- celery -A ward_run_app inspect active
The output should indicate - empty - for each pod, signaling completion.
app@(...):/app$ celery -A ward_run_app inspect active
(...)
-> email@gitguardian-email-(...): OK
- empty -
-> scanner@gitguardian-scanner-(...): OK
- empty -
-> email@gitguardian-email-(...): OK
- empty -
-> workers@gitguardian-worker-(...): OK
- empty -
-> long_tasks@gitguardian-long-tasks-(...): OK
- empty -
-> workers@gitguardian-worker-(...): OK
- empty -
-> scanner@gitguardian-scanner-(...): OK
- empty -
-> long_tasks@gitguardian-long-tasks-(...): OK
- empty -
- Scale down all workers and scheduler pods.
kubectl scale deploy/gitguardian-beat --replicas 0 --namespace <namespace>
kubectl scale deploy/gitguardian-email --replicas 0 --namespace <namespace>
kubectl scale deploy/gitguardian-long-tasks --replicas 0 --namespace <namespace>
kubectl scale deploy/gitguardian-scanner --replicas 0 --namespace <namespace>
kubectl scale deploy/gitguardian-worker --replicas 0 --namespace <namespace>
If needed, specify the Kubernetes namespace with --namespace (default namespace is used if not specified).
- The process for updating the PostgreSQL client certificate varies by installation method:
- GCP Cloud SQL: Create a new client certificate following the procedure.
-
Navigate to the “Config” tab in the KOTS Admin Console and update the PostgreSQL password. Save the configuration.
-
Deploy the updated configuration.

Update PostgreSQL Data Encryption Key
Rotating the data encryption key (Django Secret Key) is a critical process that involves several steps.
Data Encryption key rotation is an intensive process that may:
- Take significant time to complete, fully occupying a Celery worker.
- Generate constant read/write load on the database.
- Increase database disk space usage (it's recommended to ensure at least 5GB of free disk space).
Add a new data encryption key to your configuration
Reach out to our support team to get the script for creating a new encryption key.
The script requires kubectl and kots CLI (see installation documentation), and an access to the kubernetes namespace where the application is installed.
The script has two actions, status and rotate. status will output current key(s) hashes, and rotate will update the configuration.
bash gitguardian_secret_key.sh rotate --namespace <namespace>
Specify the Kubernetes namespace with --namespace.
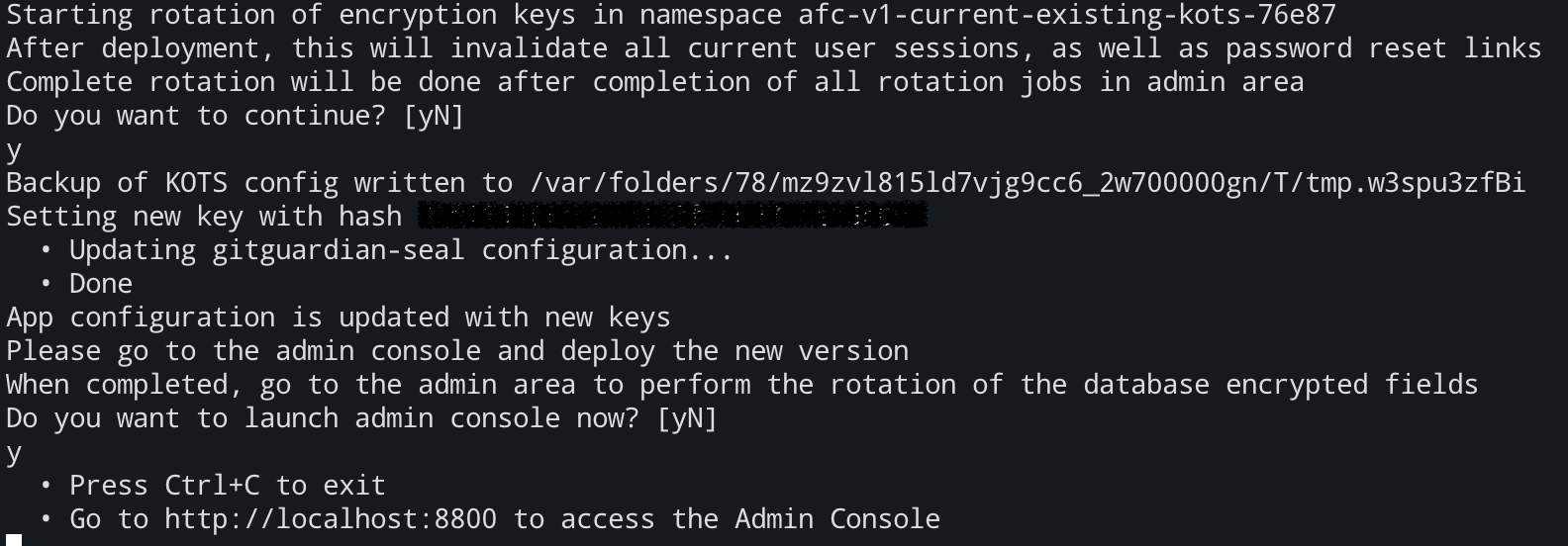
After configuration update, the script will launch the KOTS Admin Console where you will need to deploy the updated configuration.

Initiating data encryption key rotation
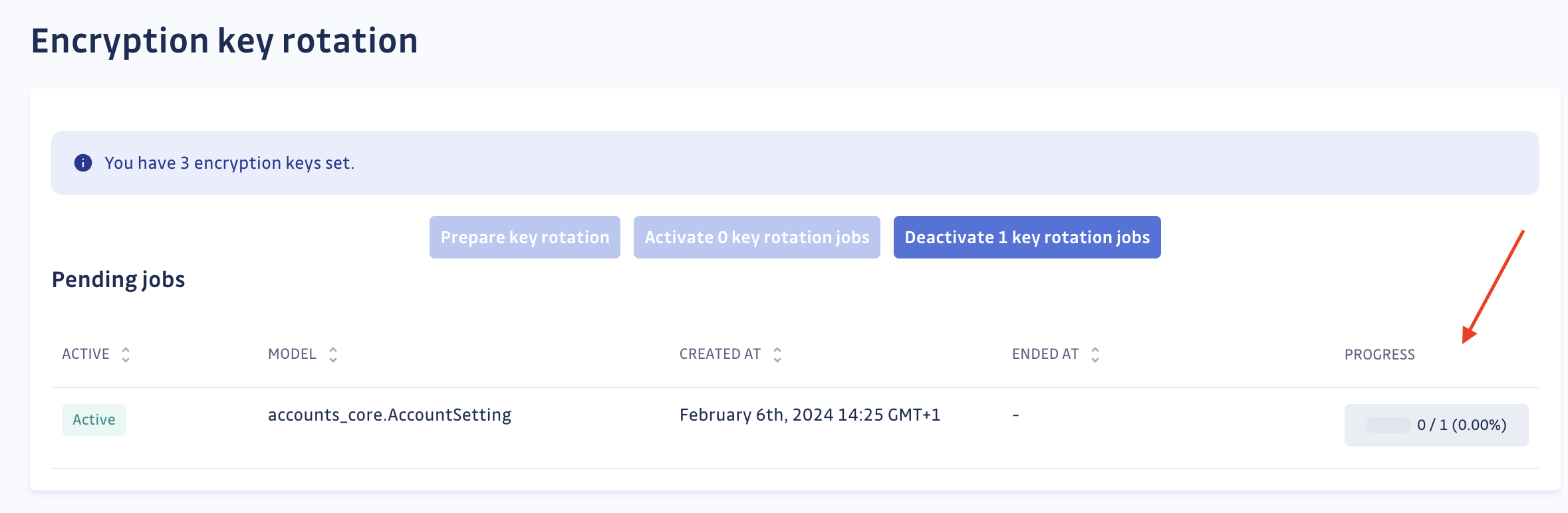
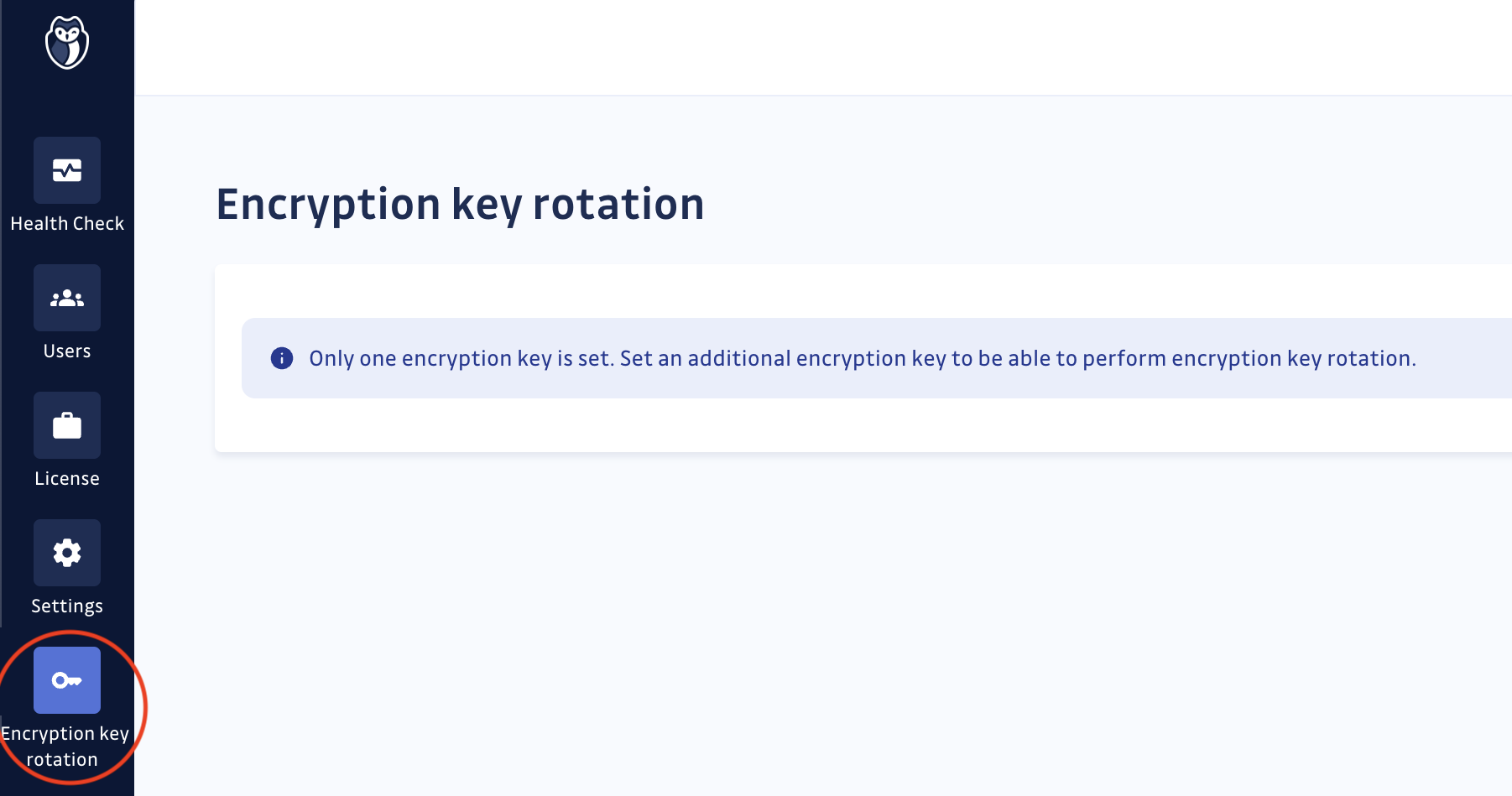
Once at least two encryption keys are set in your settings:
- Navigate to the Encryption Key Rotation page in the Admin area:
- If no rotation has been initiated for the recently added key, start by triggering the creation of rotation jobs. Click the “Prepare Key Rotation” button.
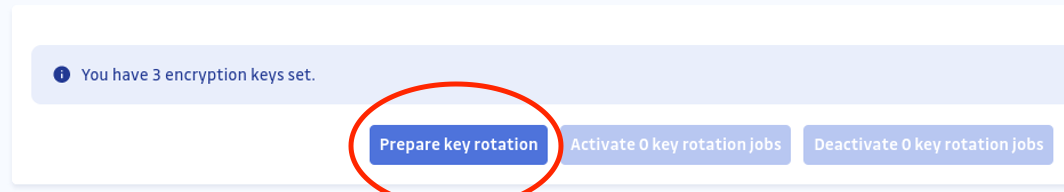
- Activate the key rotation jobs
Be aware that these jobs may take a long time and will fully occupy one Celery worker.
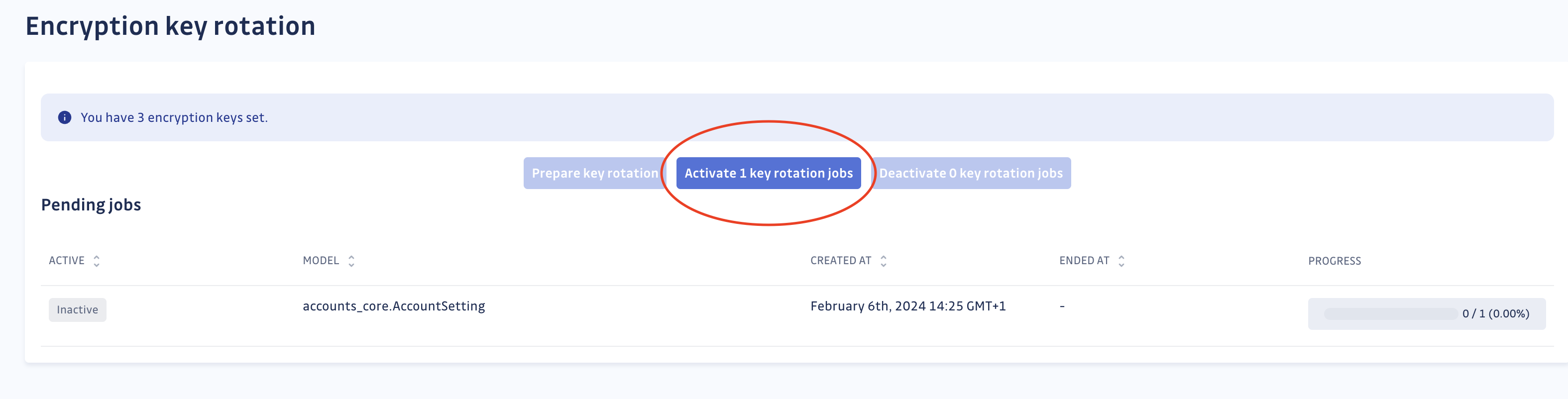
- The jobs will run automatically. All that's left is to wait for their completion. You have the option to stop or restart the jobs as needed.