2025.7 - Required
| Version | |
|---|---|
| 2025.7.0 | July 25, 2025 |
| 2025.7.1 | August 8, 2025 |
System Requirements Update
Ensure your infrastructure meets the latest requirements for optimal performance and security:
| Component | Minimum Version | Recommended Version |
|---|---|---|
| KOTS | 1.117.3 | Latest |
| Kubernetes | 1.28 ⚠️ | 1.32 |
| PostgreSQL | 15 | 16 |
| Redis | 6 | 7 |
| ggscout | 0.16.6 | Latest |
Helm & Upgrade Considerations
To ensure compatibility, please review Helm values updates from the previous version. Air gap deployment? Find all the images and tag names in the air gap install page.
⚠️ Important: This is a required release and cannot be skipped.
Machine Learning engine is now enabled by default. Ensure your infrastructure meets the ML requirements.
If you're concerned about resource usage, you can lower the priority of ML pods to ensure other critical services are scheduled first.
Historical Scanning now available for Jira and Confluence Data Center

We’re excited to announce a significant enhancement to our secret detection capabilities for both Jira and Confluence Data Center: historical scanning is now available!
What's new?
Previously, our integrations would surface hardcoded secrets in real-time, alerting you to newly introduced risks as soon as they appeared. With this update, we’re extending our detection to include secrets that were leaked in the past—not just those introduced going forward.
Why does this matter?
Once a secret is leaked, it should always be considered compromised, regardless of when the leak occurred. By surfacing historical secrets, you can now:
- Identify and remediate old, forgotten leaks that may still pose a security risk.
- Reach a comprehensive security posture by ensuring that no secrets—past or present—slip through the cracks.
- Take proactive action to rotate or revoke secrets that may have been exposed long ago.
Check out our documentation to enable historical scanning now:
Automatically Ignore Invalid Incidents with New Playbook
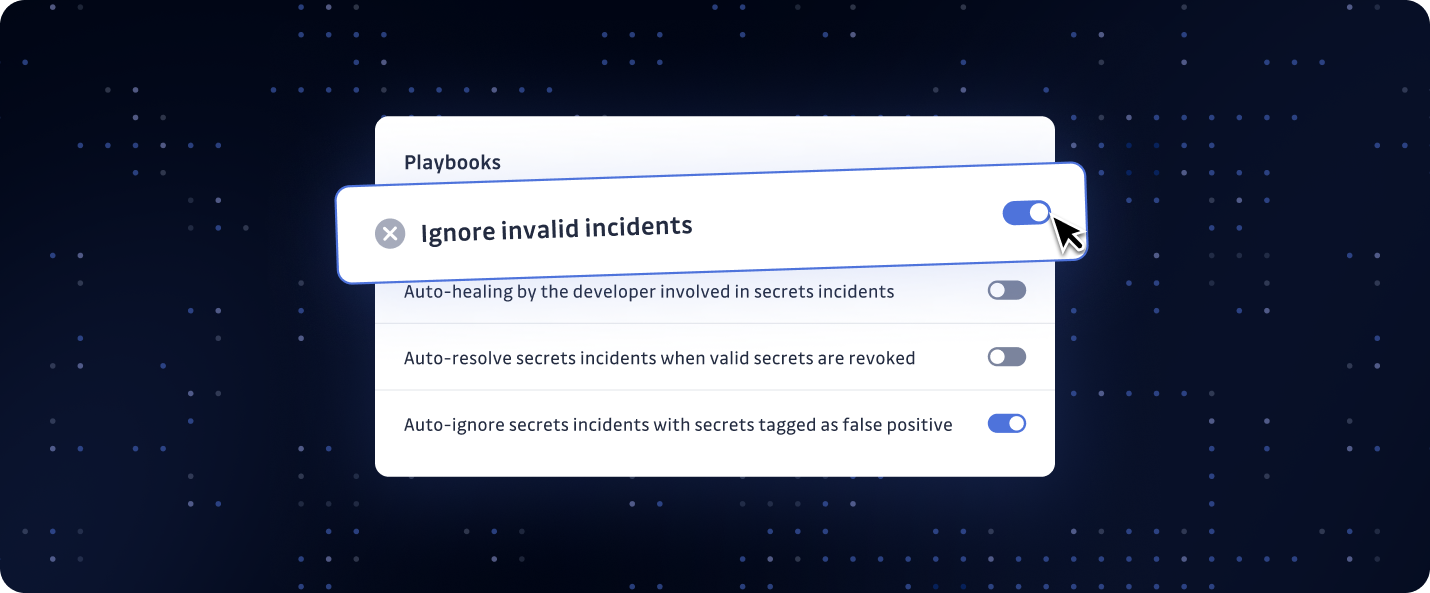
We’re excited to announce a powerful enhancement to your incident management experience, designed to help you focus on what matters: we are introducing a new playbook: Automatically Ignore Invalid Incidents.
What's new?
This new playbook will automatically ignore incidents where the detected secret has been confirmed invalid and revoked, even for those that have never been valid. With this new capability, your team can immediately focus on genuine, actionable threats without being distracted by unnecessary noise from already-resolved issues.
Why This Matters?
By automatically clearing these known invalid incidents, you'll save valuable time, reduce alert fatigue, and maintain a clear focus on critical security issues that require your attention.
Important Note
This playbook is designed for incidents from standard detectors and will not impact those related to detectors with a custom host.
You Stay in Control
The playbook will be enabled by default, but you can opt out at any time if it doesn’t fit your needs. All incidents will remain accessible in your workspace for review.
Secrets Detection Engine (v2.143)
New Detectors
- GitLab Incoming Mail Token – Detects tokens used for GitLab incoming mail.
- Coze Personal Access Token – Detects personal access tokens for Coze services.
- Tavus API Key – Recognizes API keys for Tavus services.
- Heroku Platform Key – Detects prefixed variants of Heroku Platform Keys.
- SSH Credentials – New detector
ssh_password_with_portallows matching SSH passwords with ports. - Tableau Cloud PAT – Detects personal access tokens for Tableau Cloud.
- Notion Integration Token v2 – Detects the new Notion token format.
- AI71 API Key – Detects API keys for AI71 services.
- AMP API Token – Recognizes API tokens for AMP services.
- Kubernetes User Certificate with Port – Extracts port numbers for Kubernetes user certificates.
- NVIDIA API Key – Detects API keys for NVIDIA services.
- Alchemy API Key v2 – Identifies API keys for Alchemy services.
- OpenRouter API Key – Detects API keys for OpenRouter services.
- Duffel API Key – Recognizes API keys for Duffel services.
- Apify Token – Captures tokens for Apify services.
- Jina API Key – Detects API keys for Jina services.
- Deno Account Token – Identifies tokens for Deno accounts.
- Segment Workspace Key v2 – Detects workspace keys for Segment services.
- Resend API Key – Recognizes API keys for Resend services.
- VKontakte Access Token – Detects access tokens for VKontakte services.
- Fireworks AI API Key – Captures API keys for Fireworks AI services.
New Checkers These checkers are implemented to verify the detected secrets, adding another layer of security and ensuring their validity and correct application:
- Coze Personal Access Token
- Tavus API Key
- Heroku Platform Key
- Tableau Cloud PAT
- Notion Integration Token v2
- Salesforce OAuth2
- AI71 API Key
- AMP API Token
- Kubernetes User Certificate with Port
- Alchemy API Key v2
- OpenRouter API Key
- Duffel API Key
- Apify Token
- Jina API Key
- Deno Account Token
- Resend API Key
- VKontakte Access Token
- Fireworks AI API Key
Detector Improvements
- Google OAuth2 Keys – Improved precision for Google OAuth2 detector and enhanced regex for better detection accuracy.
- Zendesk Token – ZendeskTokenAnalyzer has been rewritten in Rust for improved performance.
- Sendinblue Key – SendinblueSecretAnalyzer has been rewritten in Rust.
- Generic High Entropy Secret – No longer considers IDs in ServiceNow migration files as secrets and removed AWS ECR images that were misclassified as secrets.
- Algolia Keys – AlgoliaKeysSecretAnalyzer has been rewritten in Rust.
- Fastly Personal Token – FastlySecretAnalyzer has been rewritten in Rust.
- [Hugging Face User Access] – Migrated analyzer to Rust for improved performance.
- Kubernetes Docker Secret – Enhanced detection for
kubernetes.io/dockercfgsecrets with more precise regex for JWTs. - MySQL Assignment – Restricted the maximum number of secrets per document to prevent combinatorial explosion.
- Sourcegraph Token – Updated regex for
sourcegraph_access_token_v3as per customer request. - GitHub Access Token – GitHub classic analyzer has been rewritten in Rust for improved performance.
- HashiCorp Vault Token – Improved precision for HashiCorp Vault token detection.
- Confluent Keys – Updated checker for Confluent API keys.
- GitHub Fine-Grained PAT – Analyzer now handles archived repositories.
- Slack Tokens – SlackBot analyzer has been rewritten in Rust for improved performance and applies to Slackbot, Slack App, and Slack User tokens.
- DigitalOcean Spaces Token – Fixed checker for tokens that do not have permission to list buckets.
- Checkout Secret Key – Updated endpoint to avoid deprecated usage.
- Checkout Sandbox Secret Key – Enhanced pattern and updated endpoint for improved accuracy.
- Bunny.net API Key – Fixed checker for better validation.
- Dify API Key – Updated checker endpoint for enhanced detection.
Engine Enhancements
- All JWT detectors will now only catch signed JWTs, enhancing security.
Enhancements
- Jira Data Center Integration: Enhanced Jira Data Center incident creation to include leaker email addresses for historical comments occurrences.
- Custom Tags API: Enhanced the custom tags filter in the public API to support filtering by key/value pairs in addition to IDs, improving search flexibility for better incident management. Learn more.
- Playbook: "Auto-resolve secrets incidents when valid secrets are revoked" playbook is officially activated for all accounts. Learn about Playbooks
- Custom remediation: Added dynamic links to custom remediation pages, providing users with seamless access to relevant documentation and revocation support.
- Public API: Custom Tags (custom_tags) query parameters have been documented as part of the API documentation.
- GitLab integration: Configuration of multiple GitLab integrations using both system hooks and group hooks simultaneously is now supported.
Fixes
- Custom Tags: Fixed an issue where assigning tags to selected filtered issues was incorrectly applying tags to all issues instead of only the selected ones.
- Azure DevOps Integration: Improved token handling to prevent unnecessary revocation of Azure DevOps installations due to intermittent 401 errors.
- Email Notifications: Improved email delivery logic for Microsoft Teams integrations to prevent excessive notification sending during periodic scans.
- GitHub Integration: Fixed an issue where dangling GitHub installations were being unnecessarily checked when no installations were present.
- User Management: Ensure SCIM user provisioning matches emails case-insensitively to prevent duplicate or mismatched user entries.
- Incidents Management: Resolved a regression where secrets detected on deletion lines could reopen incidents. Deletion lines are no longer scanned for secrets, as per the expected "Scan only addition line" behavior.
Hotfixes
2025.7.1
Release Date: August 8, 2025
Fixes
- Embedded Cluster with Embedded Redis: Updated configuration to use
bitnamilegacy/redisregistry following Bitnami's registry changes. - ML Secret Engine: Updated to version 20250806 fixing critical CVE-2025-54381.
- NHI Scout: Bumped to version 0.18.2.
 Never miss a critical security event with real-time GitGuardian alerts in Microsoft Teams.
Never miss a critical security event with real-time GitGuardian alerts in Microsoft Teams. Streamline incident response with Jira Data Center integration.
Streamline incident response with Jira Data Center integration. Our first internal machine learning model halves false positives, ensuring data security and privacy without third-party dependencies. This in-house capability is now available for Self-Hosted. More information is available in the
Our first internal machine learning model halves false positives, ensuring data security and privacy without third-party dependencies. This in-house capability is now available for Self-Hosted. More information is available in the  Slack integration is now supported for scanning the full history of your public and private Slack channels to detect leaked secrets.
Slack integration is now supported for scanning the full history of your public and private Slack channels to detect leaked secrets.
