GitGuardian Bridge
GitGuardian Bridge extends GitGuardian SaaS with secure access to your private infrastructure through encrypted tunnels. This approach allows you to leverage the full benefits of GitGuardian's cloud platform while maintaining secure access to your internal resources.
Built with security at its core, GitGuardian Bridge uses outbound-only connections, mutual TLS authentication, end-to-end encryption, minimal attack surface with distroless container images, and provides complete audit logging for full compliance.
GG Bridge is only available for:
- Workspaces under Enterprise plan
- US and EU SaaS customers
What is GitGuardian Bridge?
GitGuardian Bridge creates an encrypted, outbound-only tunnel from your private network to GitGuardian SaaS, allowing you to:
- Scan private repositories without exposing them to the internet
- Monitor self-hosted services while maintaining network isolation
- Meet compliance requirements by keeping sensitive infrastructure private
- Support multiple networks with separate bridge configurations
Cost considerations
GitGuardian Bridge has the same egress cost implications as direct GitGuardian SaaS access. Consider data volume when scanning large datasets, and deploy your bridge close to data sources to minimize network transfer costs.
Supported integrations
GitGuardian Bridge works with:
| Service | Type |
|---|---|
| GitHub Enterprise Server | Version Control |
| GitLab Enterprise Edition | Version Control |
| Bitbucket Data Center | Version Control |
| Azure DevOps Server | Version Control |
| JFrog Artifactory | Container Registry |
| Azure Container Registry | Container Registry |
| Confluence Data Center | Documentation |
| Microsoft OneDrive | Documentation |
| Microsoft SharePoint Online | Documentation |
| Jira Data Center | Ticketing |
| ServiceNow (on-premise) | Ticketing |
| Bring Your Own Sources | Custom Sources |
| Custom webhooks | Notifications |
| Splunk Enterprise | Notifications |
| Custom validity endpoints | Secret Validation |
| Secrets Analyzers | Secret Analyzers |
GitGuardian Bridge currently supports validity checks for detectors that allow you to configure custom hosts (such as GitLab instances). However, validity checks are not yet supported for detectors where GitGuardian automatically extracts the host information from the location where the secret is discovered (such as PostgreSQL connection strings).
Reach out to support@gitguardian.com if you have any questions.
How to set up GitGuardian Bridge
Step 1: Request bridge access
Contact support@gitguardian.com to request bridge functionality for your account. Specify how many bridges you need (typically one per isolated network segment).
Step 2: Create your bridge
-
Log into GitGuardian Dashboard and navigate to Settings > Security > GitGuardian Bridge
-
Click "Create Bridge"
-
Configure your bridge: Name your bridge (e.g., "Production Network", "Dev Environment"), optionally add a Custom CA if your internal services use custom certificates, and add domain names of internal services (you can also do this later). Then download the certificate bundle and copy the bridge URL.
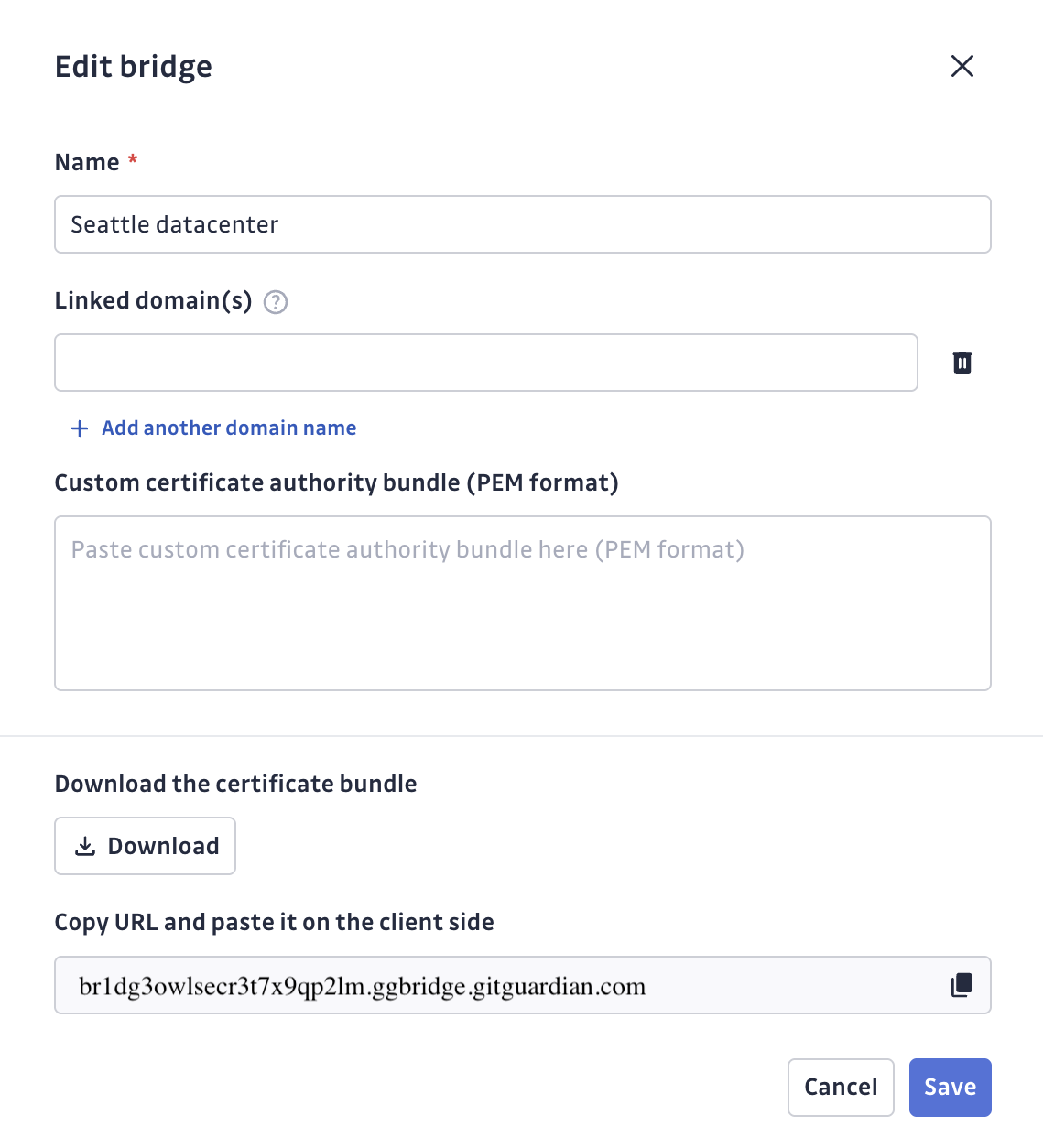 Custom CA Configuration
Custom CA ConfigurationThe Custom CA field is required when your target services use certificates signed by a custom Certificate Authority (CA). You must provide the complete certificate chain in PEM format, including:
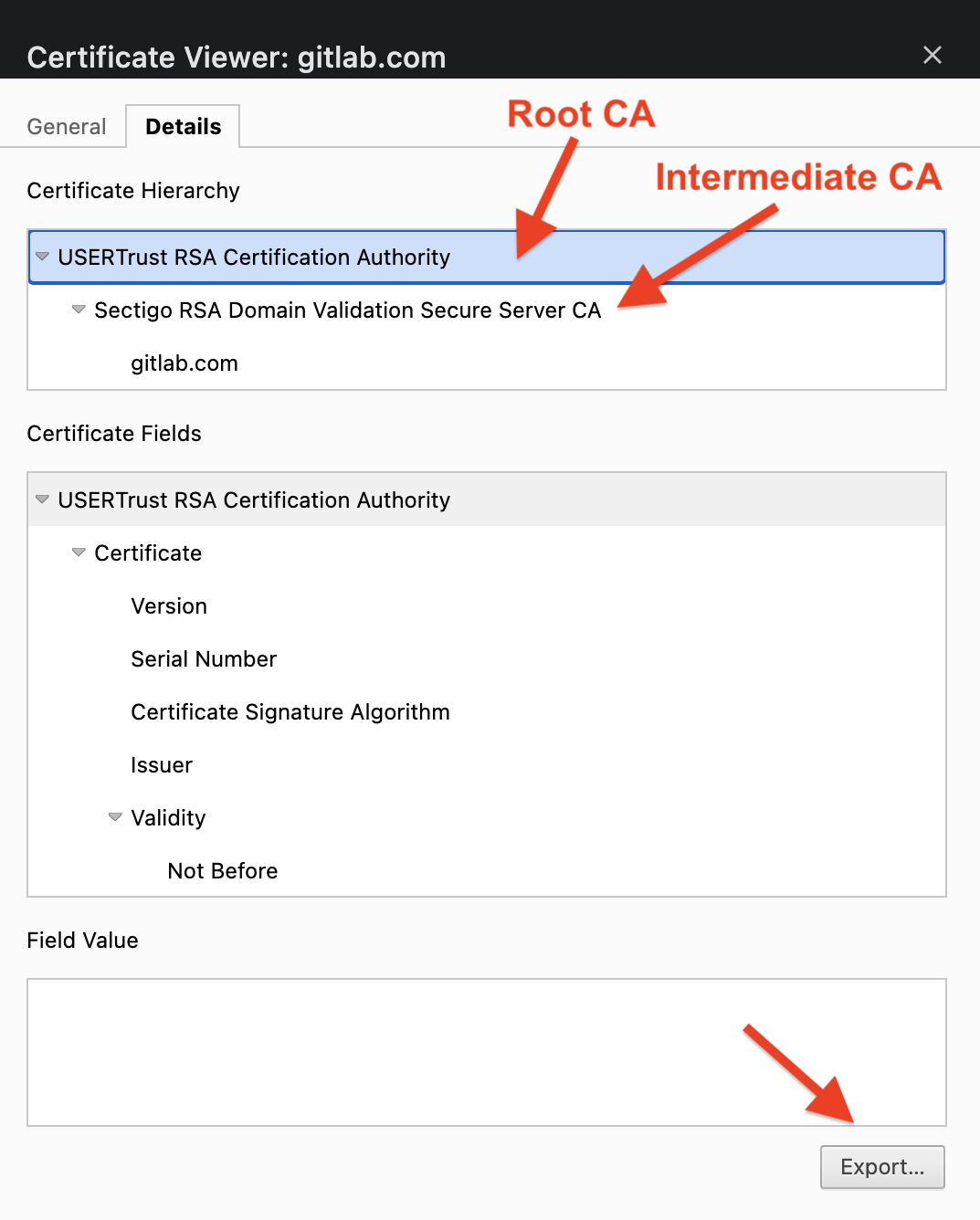
- The Root CA certificate
- All intermediate CA certificates (if any)
To export the certificate chain from your service:
openssl s_client -showcerts -connect your-internal-service.com:443 -servername your-internal-service.com </dev/null 2>/dev/null | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > bundle.pemExample PEM format:
-----BEGIN CERTIFICATE-----
MIIDXTCCAkWgAwIBAgIJAKoK/OvD... (Root CA)
...certificate content...
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIDbTCCAlWgAwIBAgIJAKoK/OvD... (Intermediate CA)
...certificate content...
-----END CERTIFICATE-----Alternatively, you can export the Root CA and Intermediate CA certificates from your browser and concatenate them into a single file:
Without proper Custom CA configuration, GitGuardian Bridge will be unable to establish secure connections to your internal services and will fail with SSL verification errors.
Step 3: Configure bridge client
Deploy the bridge client in your private network using the certificate bundle and bridge URL from Step 2.
📋 Follow the detailed installation guide: github.com/GitGuardian/ggbridge
The repository provides complete instructions for:
- VM deployment (via k3s)
- Kubernetes/Helm deployment
- OpenShift configurations
- Troubleshooting guides
Make sure to whitelist the bridge URL in your network security settings to allow outbound connections from your private network to GitGuardian SaaS.
Step 4: Configure URL mapping (if not done during creation)
If you didn't add domain names during bridge creation, go to your bridge settings and add the domain names of internal services that should route through the bridge:
gitlab.internal.company.combitbucket.team.localartifactory.dev.internal
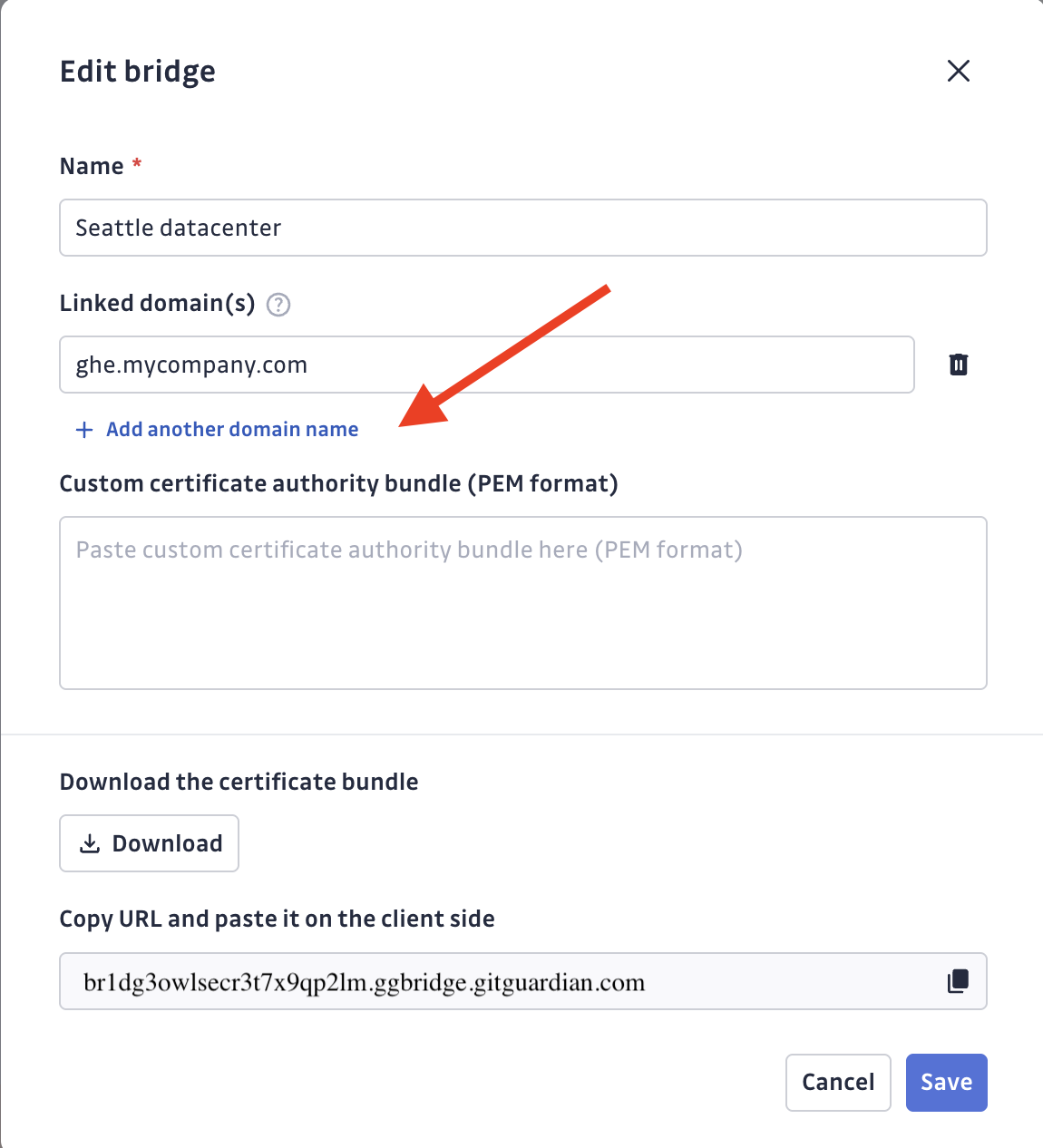
GitGuardian will automatically route traffic to these URLs through your bridge.
Step 5: Configure your integrations
Set up your self-hosted services in GitGuardian Dashboard:
- Sources: Navigate to Settings > Integrations > Sources
- Destinations: Navigate to Settings > Integrations > Destinations
- Custom Hosts: Navigate to Settings > Secrets > Detectors.
Example with GitHub Enterprise:
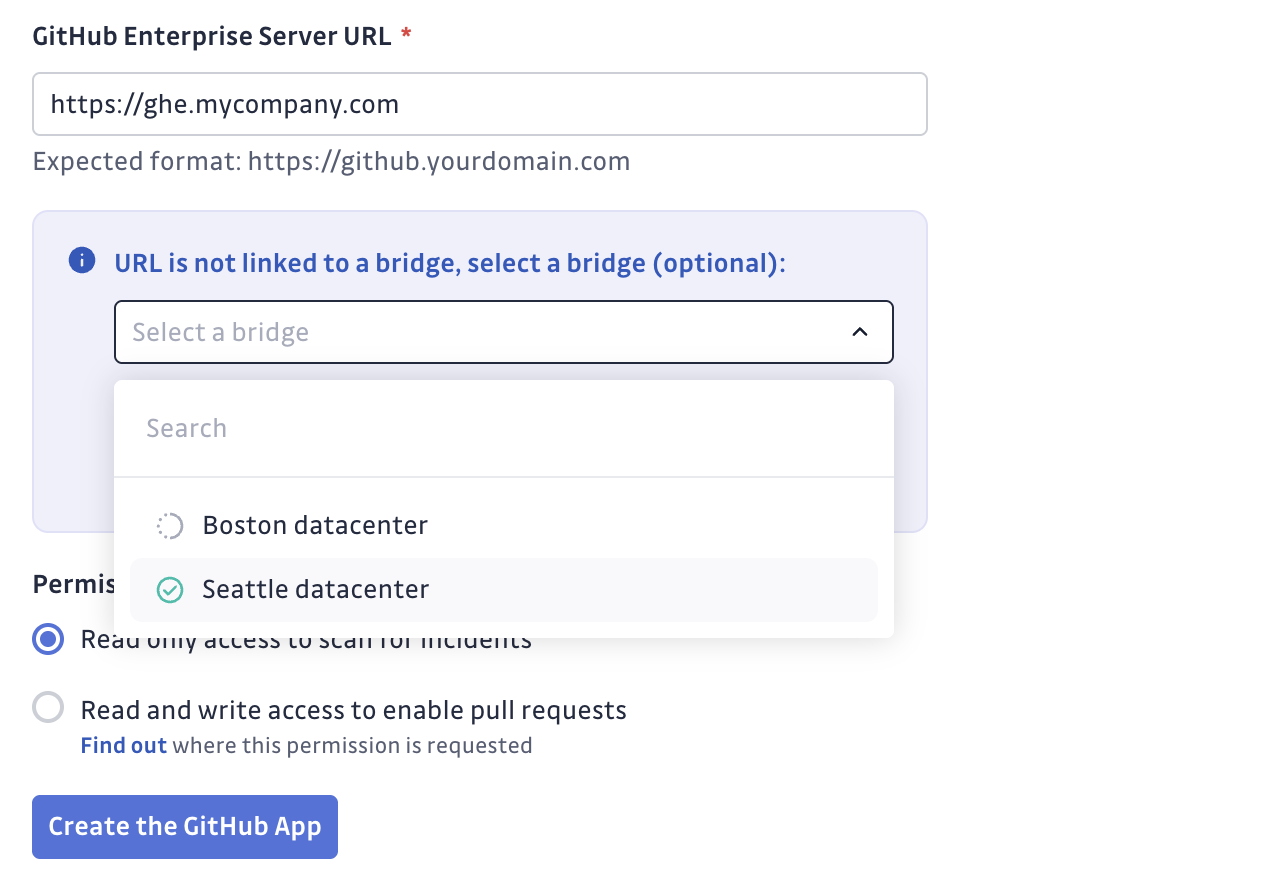
When you enter URLs that match your bridge configuration, GitGuardian automatically uses the bridge connection.
Verify everything works
- Bridge Status: Check Settings > Security > GitGuardian Bridge for connection status
- Integration Health: Monitor your source/destination health checks
- Test Scans: Run a test scan on a private repository
Before launching full-scale scans, we recommend starting with a small batch of repositories/sources to confirm the bridge is working correctly. This approach helps:
- Verify connectivity and authentication
- Validate certificate configurations
- Test integration health without overwhelming your network
- Identify and resolve any configuration issues early
Once you've confirmed everything works smoothly with the small batch, you can proceed with larger-scale scanning operations.
For assistance, contact support.

