Okta
You can configure SSO using either the GitGuardian app from the Okta Integration Network (recommended) or a custom SAML app.
Prerequisites
- An Okta account with administrator privileges
- A GitGuardian workspace with Owner or Manager role
- Your GitGuardian Workspace ID (found in your dashboard URL or workspace settings)
Supported features
- SP-initiated SSO: Users can sign in to GitGuardian directly from the application URL
- IdP-initiated SSO: Users can sign in to GitGuardian from the Okta dashboard
- Just-in-Time (JIT) provisioning: New users are automatically created in GitGuardian on first login
GitGuardian also supports SCIM provisioning for Okta. See the SCIM configuration guide for setup instructions.
SP-initiated SSO
Users can sign in directly to GitGuardian without going through Okta first:
- Navigate to your GitGuardian dashboard URL (e.g.,
https://dashboard.gitguardian.com). - Enter your email address.
- If your email domain is reserved, you will be automatically redirected to Okta for authentication.
- After authenticating with Okta, you will be redirected back to GitGuardian.
Okta OIN app
The GitGuardian app is available in the Okta Integration Network.
-
In Okta, go to Applications > Applications and click Browse App Catalog.
-
Search for "GitGuardian" and select the GitGuardian app.
-
Click Add Integration.
-
On the General Settings page, configure the following:
- Application label: Enter a name for the app (e.g., "GitGuardian").
- GitGuardian Workspace ID: Enter your GitGuardian workspace ID.
- GitGuardian API FQDN: Enter
api.gitguardian.comorapi.eu1.gitguardian.com(or your self-hosted API domain). - GitGuardian Dashboard FQDN: Enter
dashboard.gitguardian.comordashboard.eu1.gitguardian.com(or your self-hosted dashboard domain).
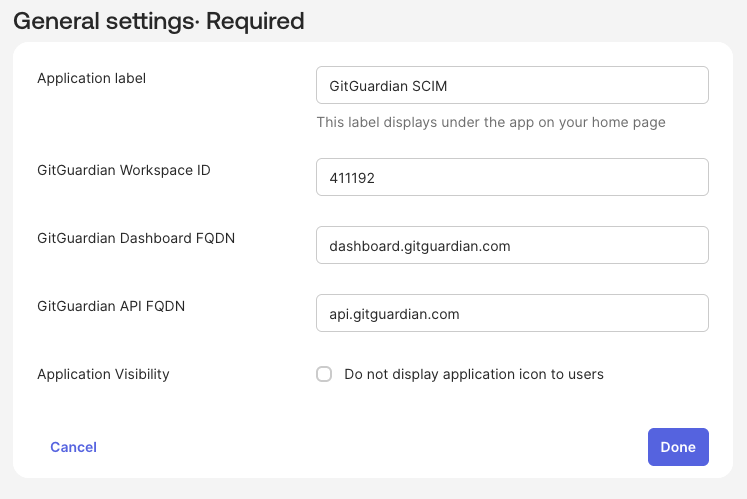
-
Click Done to create the application.
-
Go to the Sign On tab to view the SAML configuration.
-
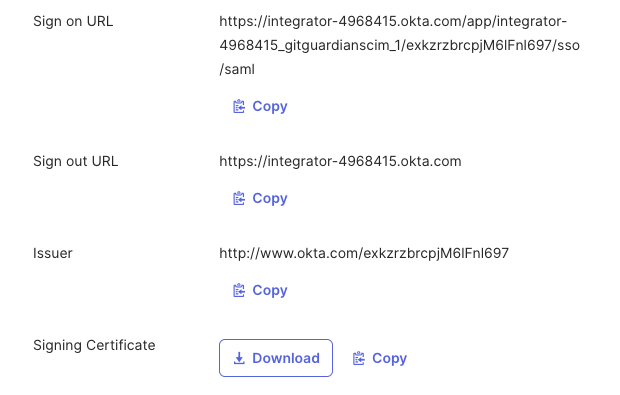
Scroll down to find the SAML metadata and copy the following values:
- Sign on URL
- Issuer
- Signing Certificate (download or copy)
-
In your GitGuardian dashboard, navigate to Settings > Authentication and click Configure.
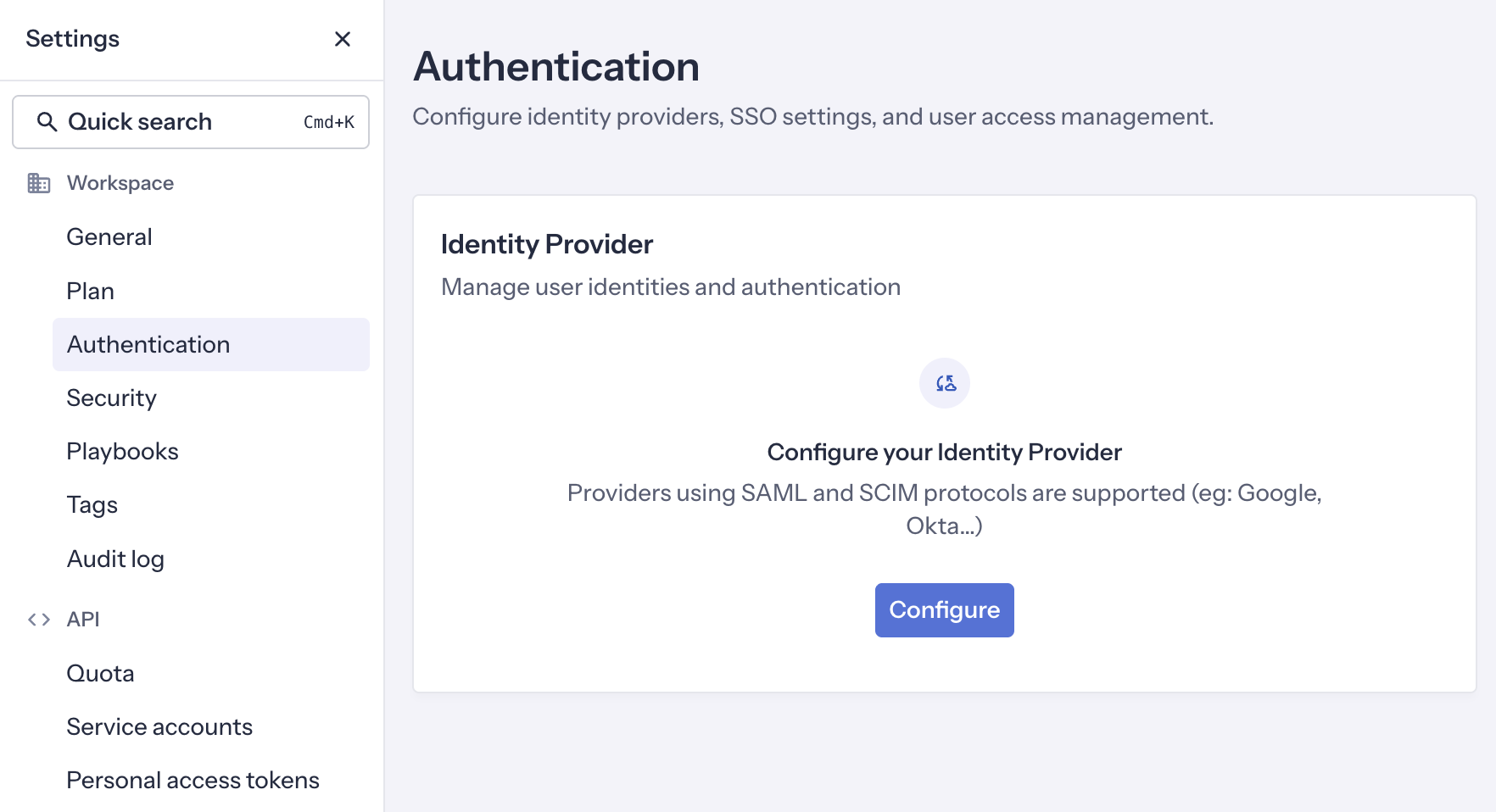
-
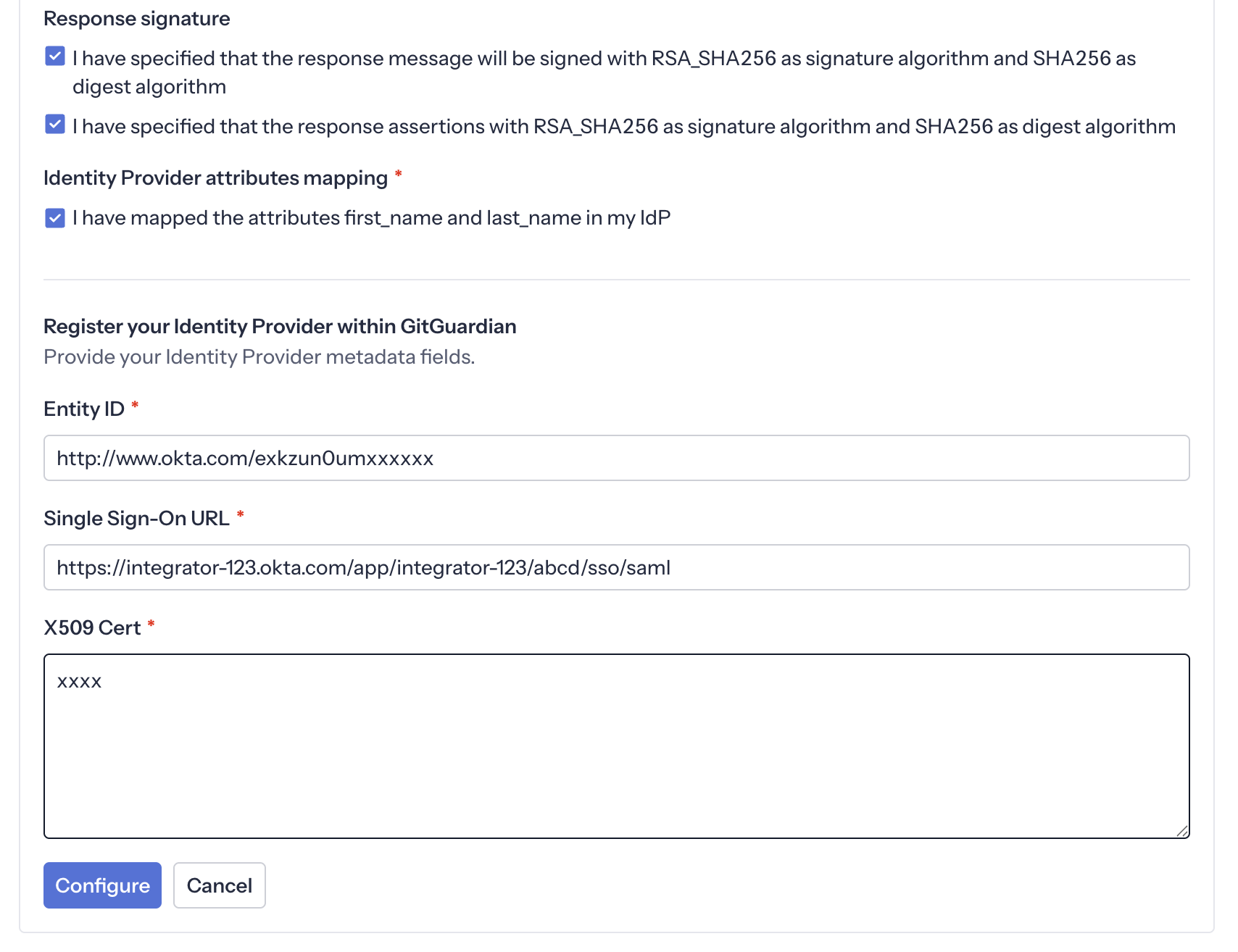
Configure the Identity Provider with the values from the previous step:
- Entity Id: paste the Issuer value
- Single Sign-On URL: paste the Sign on URL value
- X509 Cert: paste the Signing Certificate content
- Ensure that the checkbox I have mapped the attributes first_name and last_name in my IdP is checked
-
Assign users to the app in the Assignments tab.
-
Important: Reserve your email domain to enable automatic SSO discovery.
Okta custom SAML app
If you prefer to create a custom SAML application, follow these steps:
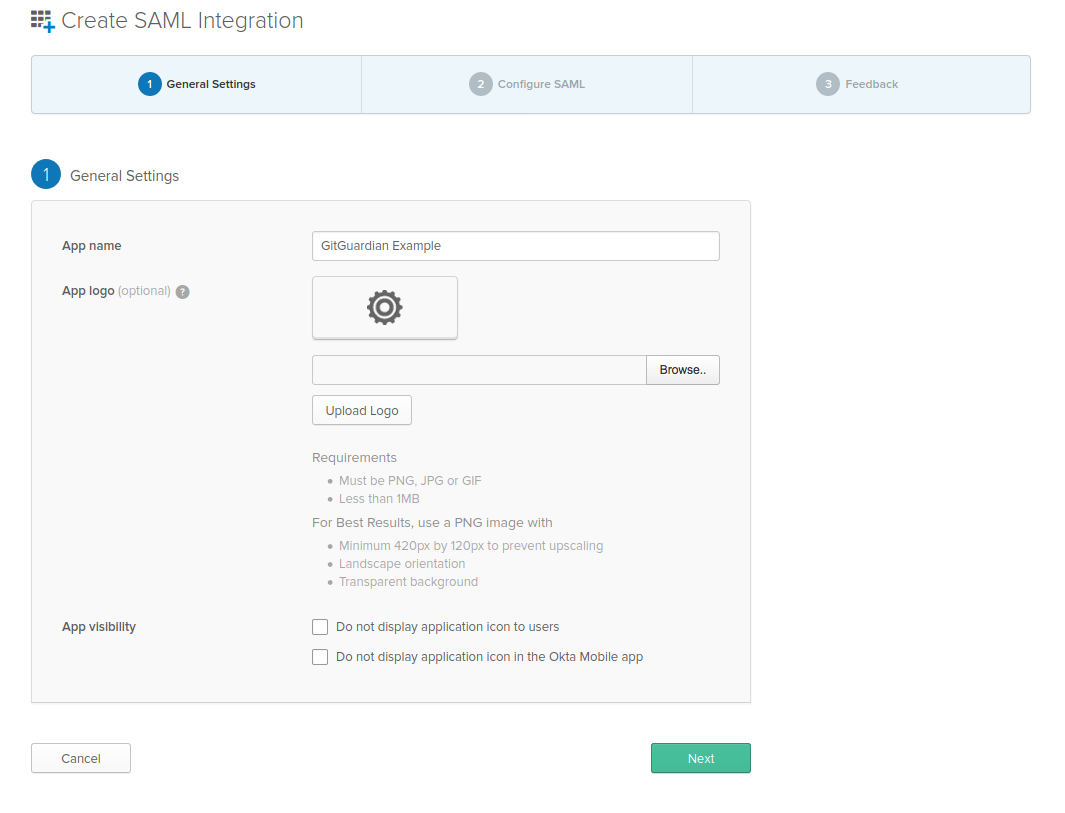
- First, go to https://$YOUR_OKTA_DOMAIN-admin.okta.com/admin/apps/add-app, then click on "Create New App".
- You will land on this page, where you can set the general information for your SAML app that users will see when
logging in.
- Click "Next". You can now configure basic settings:
Single sign on URLfield is filled with theACS URLvalue on GitGuardian dashboard.Audience URI (SP Entity ID)field is filled with theSP Entity IDvalue on GitGuardian dashboard.Default RelayStateis left blankName ID formatmust be set toEmailAddress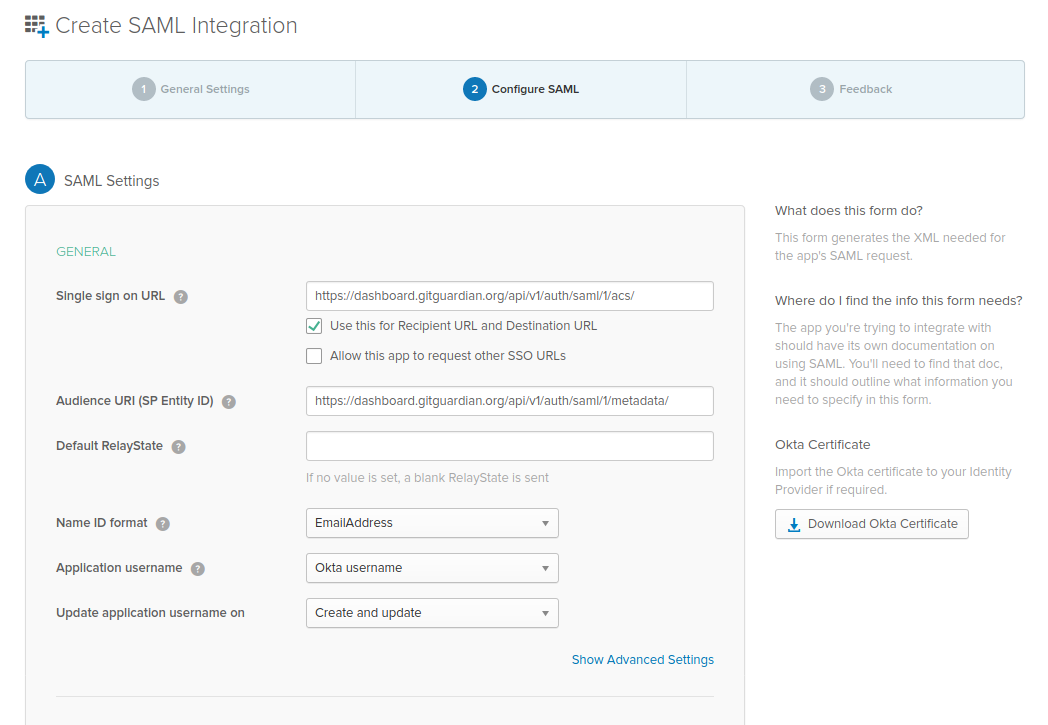
- Click on "Show Advanced Settings". Here make sure that both
ResponseandAssertion Signatureare signed, and thatSignatureandDigest Algorithmare respectively set toRSA-SHA256andSHA256. Assertions are not encrypted.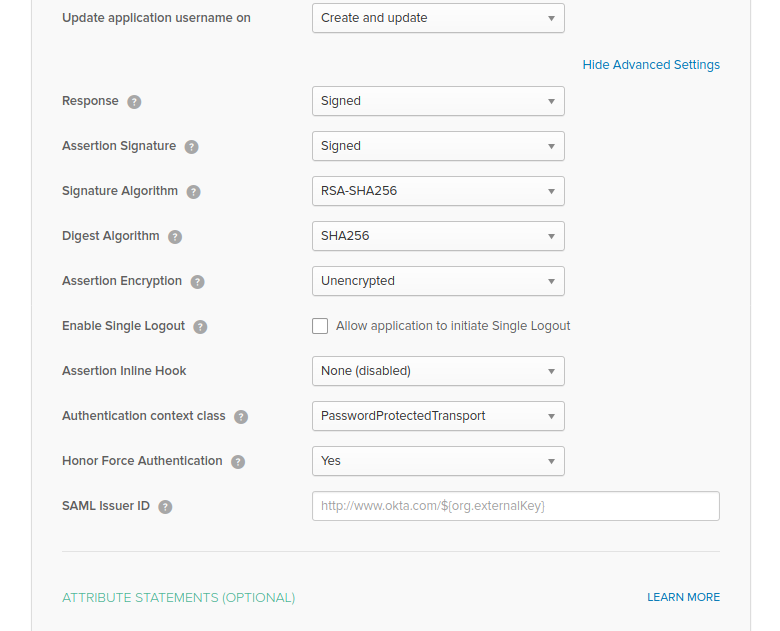
- Now, some straightforward mapping needs to done:
first_nameis mapped the user first namelast_nameis mapped the user last name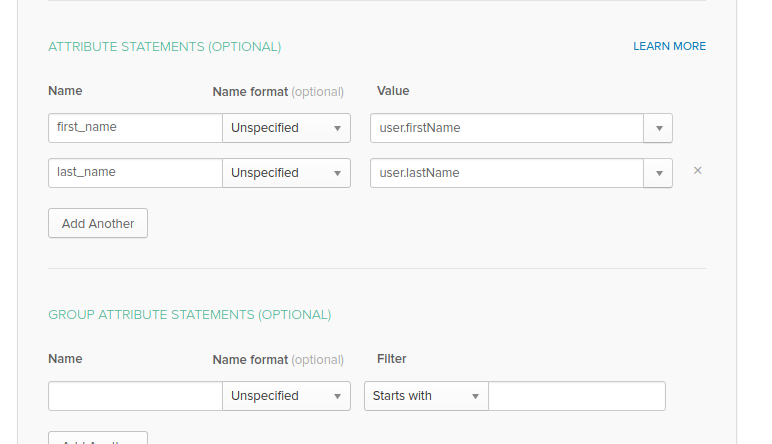
- Finish your app configuration.
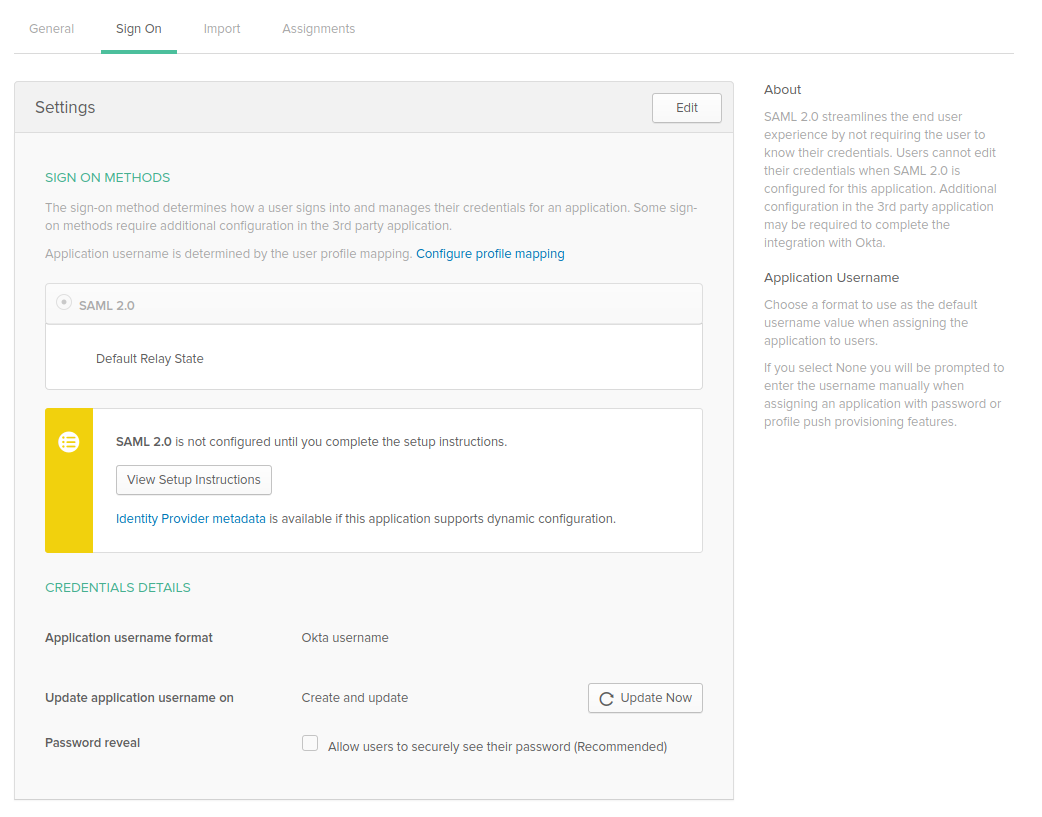
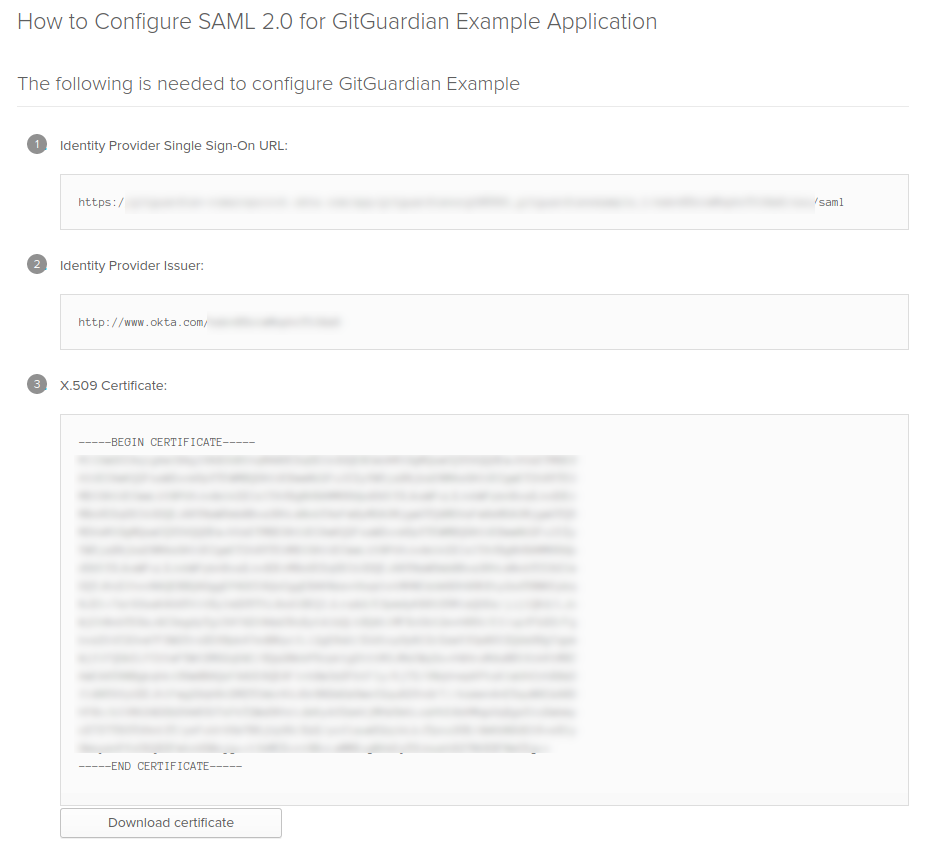
- Finally, we need to configure the Identity Provider in GitGuardian dashboard. First, click on "View Setup Instructions", then use these values:
Entity Idfield is filled with theIdentity Provider IssuerSingle Sign-On URLfield is filled with theIdentity Provider Single Sign-On URLX509 Certfield is filled with theX.509 Certificate- Ensure that the checkbox I have mapped the attributes first_name and last_name in my IdP is checked
- Important: Don't forget to reserve your email domain to enable automatic SSO discovery.

