ML-Powered Similar Incident Grouping - Combat Incident Fatigue!
Release Date: January 8, 2025
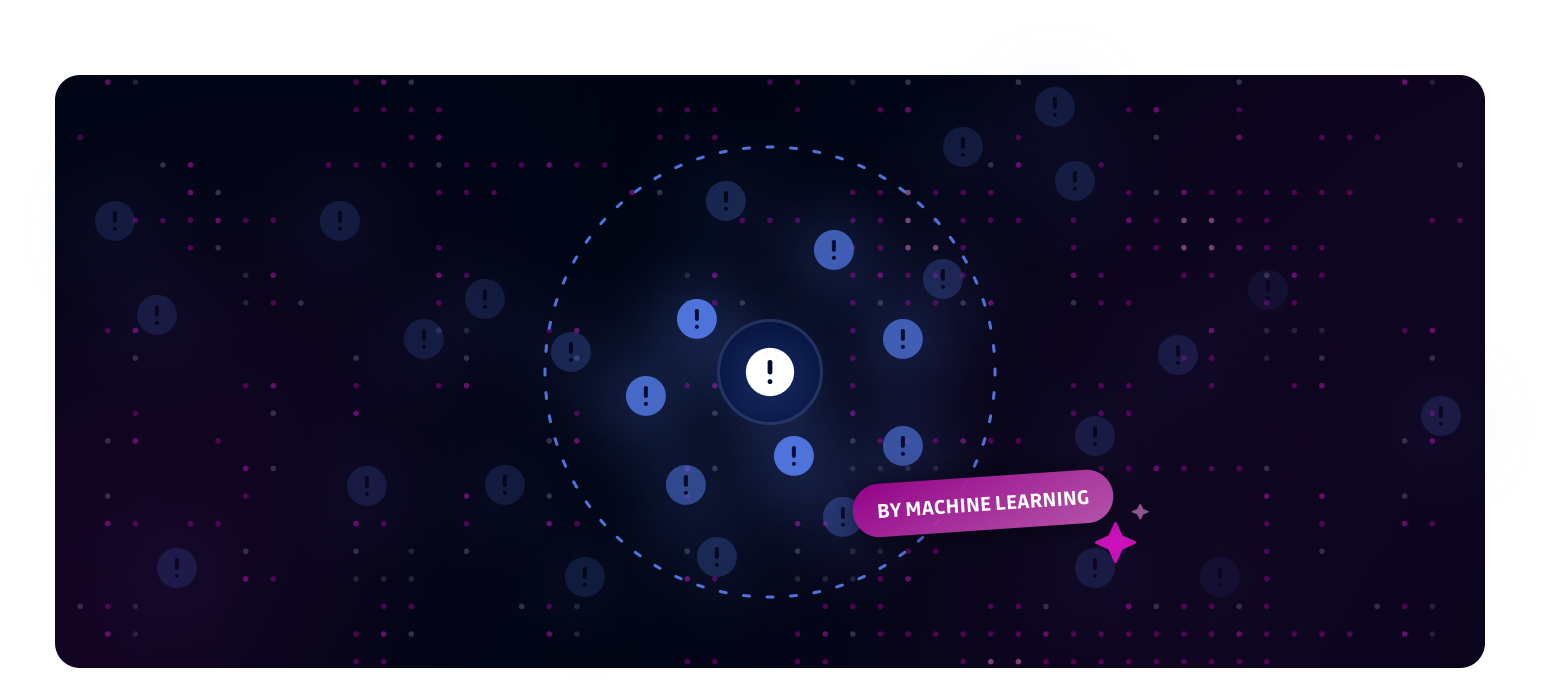
Introducing ML-Powered Similar Incident Grouping - a smart solution to combat incident fatigue by automatically grouping related incidents for efficient bulk remediation.
Key Benefits:
- Reduce incident overload by identifying patterns in similar security incidents
- Streamline bulk actions on groups of related incidents
- Focus on unique issues while efficiently handling repetitive cases
Common grouping scenarios:
- Rotating tokens in automated deployments
- QA test credentials appearing across multiple files
- Database connection strings to the same environment
- Repeated false positives from templating code or tutorials
- High-entropy strings in logs that are likely system-generated
- Known noisy patterns from specific services or file types
Our ML algorithms analyze incident context beyond just detector types to identify meaningful relationships between incidents. View similar incidents in the sidebar of any incident detail page, then use bulk actions to resolve them efficiently.
This feature is available for both Internal Monitoring and Public Monitoring on the Business & Enterprise plans.
Enhancements
- Integrations: Improved token refresh reliability for Slack and Atlassian Cloud integrations with automatic retry on transient failures.
Fixes
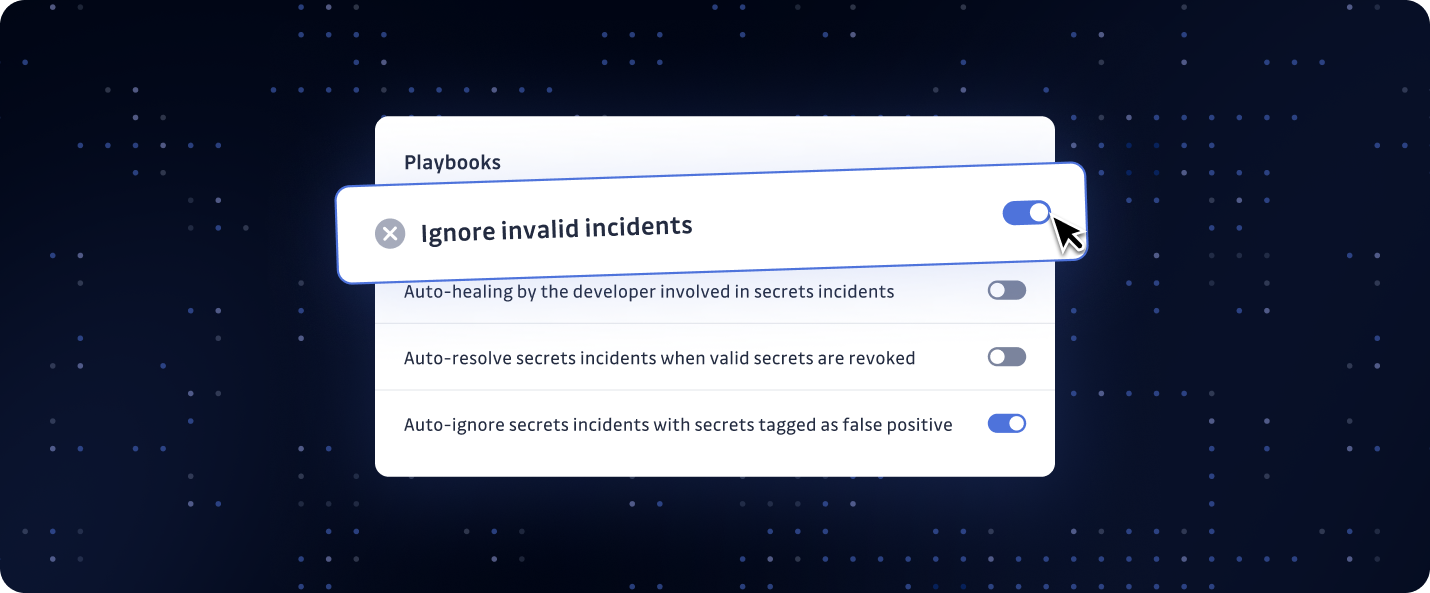
- Playbooks: Fixed an issue where the "Auto-ignore incidents when secrets are tagged as false positive" playbook was incorrectly reactivated when a Business account's plan was edited in the back office.
- Historical Scans: Resolved a scan queueing issue that prevented all eligible sources from being properly enqueued during bulk scan operations.
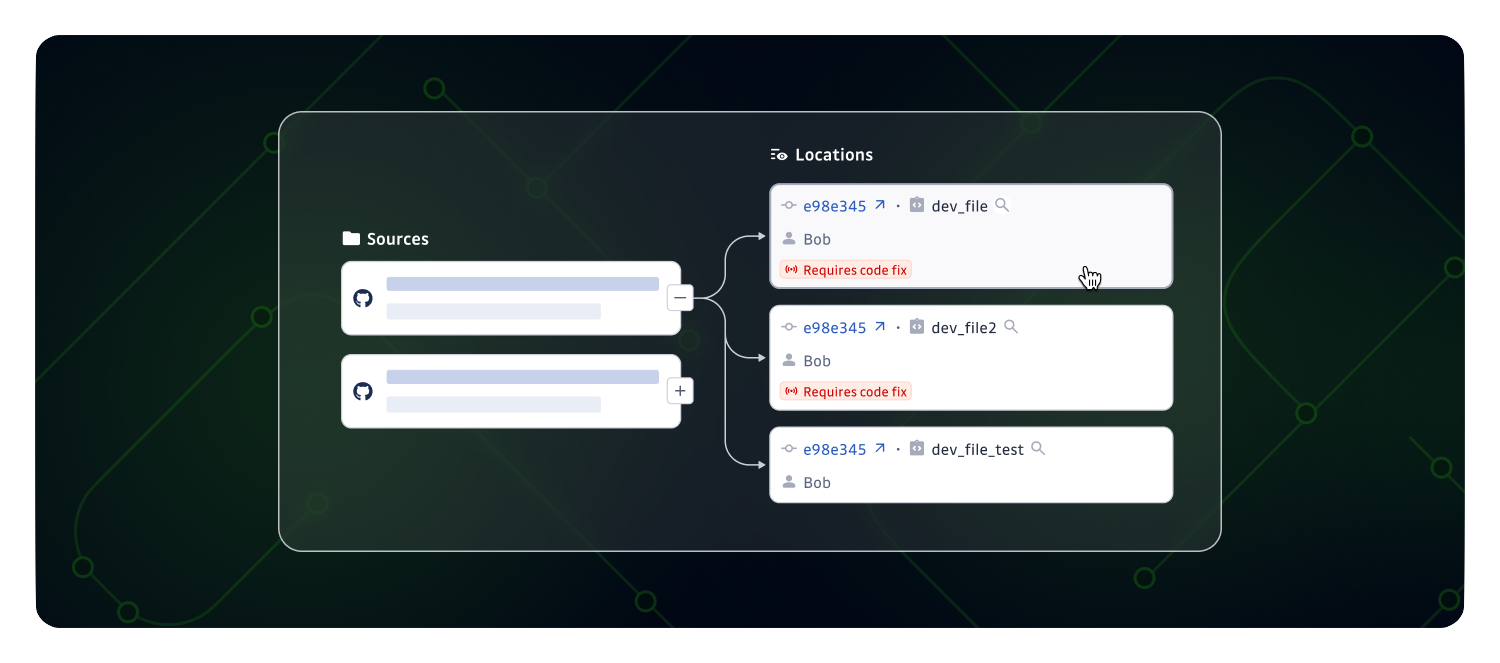


 GitGuardian allows you to monitor secret leaks across thousands of your repositories and over
GitGuardian allows you to monitor secret leaks across thousands of your repositories and over 
